Satellite terminals widely used in transportation, military, and industrial plants contain backdoors, hardcoded credentials, weak encryption algorithms, and other design flaws, a new report says.
April 17, 2014
Critical design flaws have been discovered in the firmware of popular satellite land equipment that could allow attackers to hijack and disrupt communications links to ships, airplanes, military operations, industrial facilities, and emergency services.
If just one of these thousands of devices were to be compromised, the entire satellite telecommunications infrastructure could be in danger, according to research published today.
In some cases, an attacker need only send an SMS text message to launch an attack. "You could attack one of these devices with SMS, and trigger features to install new firmware or to compromise it," says Ruben Santamarta, principal security consultant for IOActive, who discovered the security flaws last fall and published a report on his findings today. An SMS from one ship to another could compromise some satellite communications, the report says.
"Attackers who compromise the database of an Inmarsat SIM/Terminals reseller can use this information to remotely compromise all those terminals," he says.
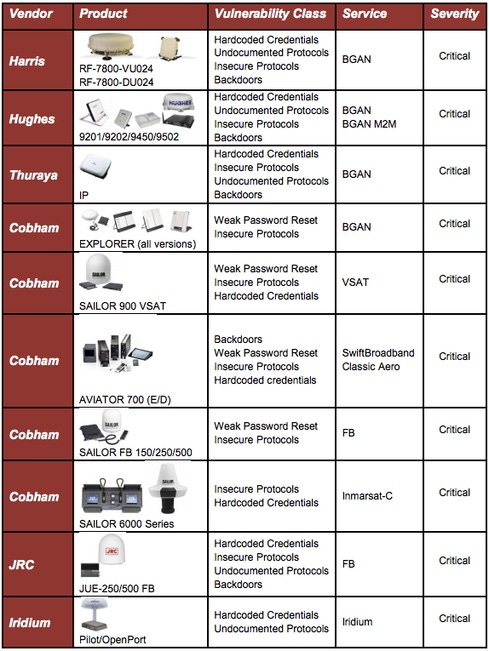
Santamarta dug up numerous design flaws in satellite ground terminal equipment from Harris Corp., Hughes, Thuraya, Cobham, JRC, and Iridium. The flaws include hardcoded credentials, undocumented protocols, insecure protocols, backdoors, and weak password reset features. He reported his findings to the CERT Coordination Center, which in turn alerted the affected vendors in January. But to date, just one vendor -- Iridium -- has responded to the alerts and is working on fixes.
"In most cases, attackers can completely compromise" the system, Santamarta says. "They could run their own code, install malicious firmware... and do anything they want with that device."
An attacker could disrupt satellite communication to a ship or aircraft, he says, potentially wreaking catastrophic damages. "They can spoof messages and trick the ship to follow a certain path, or to rescue another ship. They can disrupt communications... if a vessel can't send a distress signal, that's the worst scenario, if a ship can't communicate."
The same would be true for an airplane, he says. And an attacker would not even need physical access to the satellite equipment to pull off a link hijack or spoof; in many cases, hackers could execute their attacks remotely.
Santamarta found the flaws after downloading and reverse engineering the firmware for the systems. "I wasn't looking for memory or buffer overflow or other typical vulnerabilities. But design flaws [found] like backdoors or [weak] protocols are in a way more dangerous because you can reach the device" by using them.
Attackers would have to have some knowledge of the inherent firmware weaknesses and how to exploit them, and some vulnerabilities are easier to exploit than others. "But if you can reach the device, you can compromise it. You can access it through HTTP or some other kind of documented interfaces. In most cases, you can remotely exploit these flaws."
The vulnerable products found by IOActive are Harris' RF-7800-VU024 and RF-7800-DU024 terminals for Broadband Global Area Network (BGAN) services; Hughes 9201/9202/9450/9502 for BGAN and BGAN M2M services, Thuraya IP for BGAN services, Cobham Explorer and SAILOR 900 VSAT for VSAT services, Cobham AVIATOR 700 (E/D) for SwiftBroadband Classic Aero services, Cobham SAILOR FB 150/250/500 for Inmarsat FB services, Cobham SAILOR 6000 Series for Inmarsat C services, JRC JUE-250/500 FB for Inmarsat FB services, and Iridium Pilot/OpenPort for Iridium services.
Dan Kaminsky, co-founder and chief scientist at White Ops, says the IOActive findings demonstrate how hacking has evolved and satellite technologies have not kept up. "Historically, those who could attack satellites were bound by financial and diplomatic considerations -- it's expensive to talk to the birds, and those who can afford it are nation-states who need to be careful about acts of war," Kaminsky said in an email interview with Dark Reading. "This has the effect of insulating engineers from a lot of security fears, a convenient thing when the underlying technology is hard enough to build without making it secure. Of course, time passes, tech gets cheaper, regular hackers get access...and you have, in 2014, an actual 'first contact' situation between a public researcher and a very private engineering community."
When asked if these device satellite equipment firmware weaknesses could be discovered via public Internet scans, Santamarta declined to comment.
IOActive recommends in the report that users of these satellite products move to mitigate any potential attacks using these vulnerabilities. "Owners and providers should evaluate the network exposure of these devices, implement secure policies, enforce network segmentation, and apply restrictive traffic flow templates (TFT) when possible. Until patches are available, vendors should provide official workarounds in addition to recommended configurations in order to minimize the risk these vulnerabilities pose."
The full report is available here.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


