Harden your defenses to ensure that your holiday downtime doesn't become an open door for cyber threats.
For many people around the world, 2020 has been a deeply challenging year. Fear and uncertainty have shaped their lives personally and professionally. At the same time, accelerated digital transformations have been thrust upon countless organizations. In the midst of this adversity, an ever-growing cohort of cyber-threat actors has seized on 2020's challenges as the ultimate opportunity.
Unfortunately, 2020 has already claimed the regrettable title of having the "highest number of potential intrusions uncovered by Falcon OverWatch in a calendar year."
Adversaries Don't Vacation
Organizations will naturally look toward the holiday season as an opportunity for employees to regroup and recharge. But defenders should be proactively working to harden their defenses to ensure that any operational downtime doesn't become an open door for threats. Both state-sponsored and e-crime actors have remained highly active through the second half of 2020.

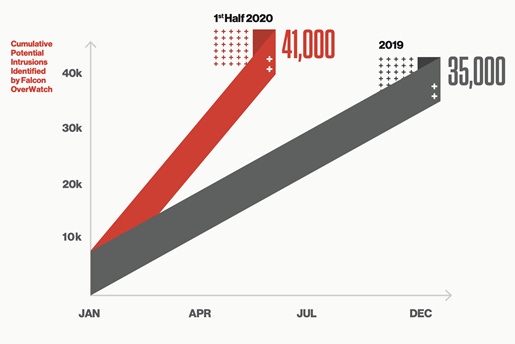
Fig. 2. OverWatch observed intrusion campaigns increasing throughout 2019 and into 2020. Source: CrowdStrike
Opportunistic e-crime actors have found 2020 to be a particularly lucrative year. It is continuing to make gains on state-sponsored activity; e-crime now comprises 82% of all intrusions uncovered by OverWatch (where it was possible to make attribution to a high degree of confidence). One particularly disappointing development from e-crime threat actors has been the widespread ransomware attacks against the healthcare industry, resulting in potentially serious delays in patient care. This should show organizations across all sectors the extreme lengths that today's e-crime actors will go to in pursuit of profit.

Fig. 3. In 2020, e-crime intrusions gained ground over state-sponsored attacks compared to 2019. Source: CrowdStrike
Threat hunters routinely observe threat actors staging their campaigns outside of business hours or during holiday periods, when it is perceived that organizations' defenses will be weaker. Knowing this helps defenders make decisions to ensure business resiliency during these periods to keep their environment safer.
Holiday Season Security Checklist
Before settling in for the holidays, I strongly recommend that defenders address five key areas of defense that will be critical to preventing intrusions at the end of 2020:
Establish a proactive and continuous threat-hunting practice.
Complement investments in technology-based defenses with human capabilities to hunt down and protect against the persistent and stealthy intrusions that automated detection systems alone cannot prevent. Human hunters are the best defense against human adversaries. Organizations can implement threat-hunting teams in-house or outsource resources to meet demands.Audit internet-facing infrastructure for missing security patches.
Accelerated digital transformation in 2020 has opened the door for adversaries — now is the time to close it. Getting the basics right has never been more important. Any infrastructure that is internet facing needs to be properly configured and fully patched.Eliminate excess software.
Adversaries will attempt to evade defenses by using native tools or legitimate software. Organizations should establish strict controls over at-risk services exposed to the internet and eliminate unneeded software running in their environments.Establish and enforce strong password policies and multifactor authentication.
The use of valid accounts continues to be among the most commonly seen techniques employed by adversaries. Defenders should ensure strong password policies are in place, enforce use of multifactor authentication, and routinely monitor authentication logs, account creation, and changes in user privileges.Prepare your users to join the fight.
While technology is clearly critical in the fight to detect and stop intrusions, the end user remains a crucial link in the chain to stop breaches. Users should be alert to COVID-19 or holiday-season themed phishing attempts. Well-trained employees can be an asset in combating the continued threat of social engineering techniques.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




