What Game of Thrones' Arya Stark and the Faceless Men can teach security pros about defending against modern malware and identity theft.
**Warning: Potential Spoilers for Game of Thrones**
Let's assume for a moment that you're not a security practitioner, at least not in the cyber sense, and instead you're the Commander of the Guards at one of the many forts or castles that pepper the landscape of Westeros. The local lord (hopefully not a Lannister) has charged you with protecting the castle and its inhabitants from various threats, including the occasional band of raiders, drunken ruffians, and their ilk, and even opposing armies. In each case, you've used your past experiences to accurately assess the threat you're facing, select the appropriate countermeasures, and dispatch your foes.
Typically this boils down to:
Using past experiences to predict your potential exposure or vulnerability
Preventing attacks by fortifying your castle's defense mechanisms (walls, gates, moats, etc.)
Putting in place detection mechanisms such as guards and scouts to sound alarms when threats are discovered
Having troops available to respond to threats as needed
Interestingly, modern security personnel follow an eerily similar methodology for addressing cyberthreats, except that they've added the word "fire" to their "walls" and replaced drawbridges and gates with usernames and passwords. Sounds great, right? Almost. Except for what happens when the threat comes from a trusted party.
Stolen Credentials Enable Fabulous Attacks
To illustrate the danger compromised insiders pose to an organization, let's discuss Arya Stark's storyline. In season five, Arya embarked upon a journey to the House of Black and White in Braavos to train with the Faceless Men, a powerful guild of assassins with the unique ability to steal the faces (and identities) of their victims. This ability lets the faceless men mask their activities and go undetected until they reach their ultimate targets.

Source: Orion Cassetto, Exabeam
Traditional Security Doesn’t Stand A Chance
Passwords, gates, moats and firewalls, are all designed to keep the bad guys out. They may be great at keeping Wildlings out of your castle, but cease to be effective if the threat comes from the inside; from your employees, allies, or bannermen. Most security solutions — modern or otherwise — have no graceful answer for insider threats. These attacks prove just as difficult for today's security teams as they would be for the guards of the best-fortified castle in Westeros. Why is that?
Compromised insider attacks use legitimate credentials, leverage known devices, and make use of valid access privileges. When hackers use stolen credentials or a compromised machine, the attack appears normal from the point of view of point security products. "Legitimate" behavior doesn't trip alarms and it doesn't create security alerts that can be investigated. This situation is further compounded when lateral movement is involved because one part of the attack might use one identity or machine, while the other part of any attack may leverage a different identity, IP address, or device.
A strong parallel can be drawn between the tactics of the Faceless Men and modern malware. For those unfamiliar, malware means "malicious software," and it includes a wide variety of nefarious programs including viruses, worms, ransomware, Trojans, and more. What all malware has in common is that it is programmed to take control of resources such as machines, credentials, and accounts, and then use them to do the bidding of the attacker. Similar to the tactic of the Faceless Men, stolen credentials and machines often are used to freely navigate through a corporate network looking for high-value targets and sensitive data. These attacks are difficult to detect because they leverage legitimate identities and access privileges to do their dirty work. In other words, by stealing the identity of someone with the gate key, malware can walk freely through the castle instead of spending time trying to break down the gate.
How Compromised Insiders Leverage Lateral Movement
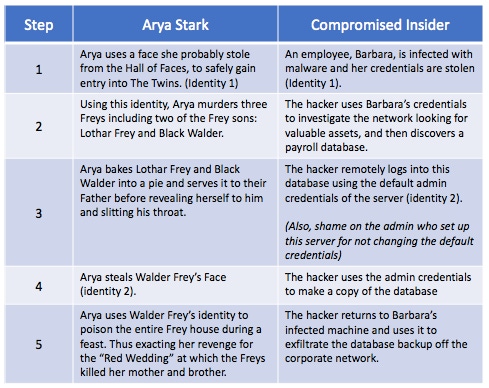
To get a better understanding of the similarities between the Faceless Men and compromised insiders, let's compare the attack chain of Arya with Barbara, an employee who has been infected with malware.
Observing Behavior May Still Prove Effective
While hackers may disguise their attacks with legitimate credentials and access privileges, they still can be uncovered by understanding how users normally behave and by looking for anomalous activity. For example, is it normal for the stable boy to raid the armory at night, or your HR coordinator to login remotely from Ukraine and back up the payroll database? Maybe the stable boy needs a knife to pry off a horseshoe, or perhaps this midnight trip to the armory is a sign that Arya or Jaqen is plotting their next move.
By using machine learning and data science to baseline the behavior of all users and machines in an organization, it's possible to automatically identify risky, anomalous behavior that may indicate a threat. This approach provides security teams — or guards — the ability to automatically detect compromised users even if the attacker is using advanced tactics such as lateral movement or stolen faces.
Related Content:

Learn from the industry’s most knowledgeable CISOs and IT security experts in a setting that is conducive to interaction and conversation. Click for more info and to register.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




