Your organization's most valuable data may be stored in scattered – and insecure – locations. Here are some tips for identifying that data and making sure it doesn't leak out
October 14, 2011


When Michael Belloise joined human resources outsourcing firm TriNet four years ago as the IT manager, the amount of sensitive data held by the company put him on edge.
TriNet handles payroll and benefits for its customers. As such, its systems store Social Security numbers, birth dates, employee ID numbers, and addresses for 100,000 workers at other companies. That data isn't necessarily subject to the kind of detailed privacy and security rules covering financial transactions or healthcare information, but it's highly sensitive nonetheless.
Belloise brought in data loss prevention vender Vontu (now part of Symantec) to install a data discovery appliance that finds and monitors all data leaving the company's network. The results, says Belloise, were shocking.
"I dare not drop any numbers about what we saw, but it was egregious," he says.
TriNet had secure ways of transmitting and storing data, but its employees were using alternative, less-secure methods, including unencrypted portable media, drop boxes, and attachments to email sent from personal accounts. In most cases, they were skirting the rules in order to serve customers faster, but some of the activity looked questionable and possibly malicious. The security violations didn't result in any data breaches, but the results were eye opening, Belloise says.
"It was to the point where you couldn't put your head in the sand anymore, because it was that shocking," he says.
Belloise called a meeting of C-level execs and embarked on a mission to secure the company's data. TriNet first studied its data to gauge the risk it faced. Then it altered processes and educated employees to minimize misuse of data, and also installed a DLP system to monitor compliance.
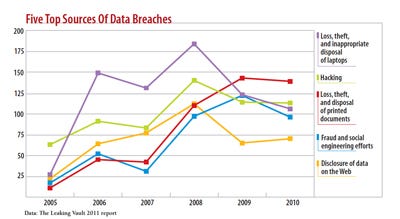
TriNet's experience isn't all that unusual. Sensitive data has a habit of spreading throughout companies and ending up in places it shouldn't be--places it's more likely to be stolen or accidentally leaked. Lost, stolen, and inappropriately disposed-of laptops have accounted for the greatest number of breach incidents in most of the last five years, according to The Leaking Vault 2011, the Digital Forensics Association's comprehensive report. But much of the information that's on those laptops shouldn't have been there to begin with.
Start Talking
To tackle data problems, companies have to find out which systems and devices hold sensitive data, reorganize their infrastructure and business processes to restrict access to that data, and then monitor their systems to ensure compliance. It's difficult, and without support from company executives, it won't happen, says TriNet's Belloise.
"The hardest thing in the entire world is to get your executives on board," he says. "It's not as easy as plugging in an appliance--that's just a fraction of the effort. It's a cultural change."
Companies that haven't had a data breach might question if it's worth the effort. In those cases, Belloise's strategy of getting a vendor to document the problem is a good way to gain support.For companies that have suffered breaches, the challenge is moving quickly enough to identify and fix any problems.
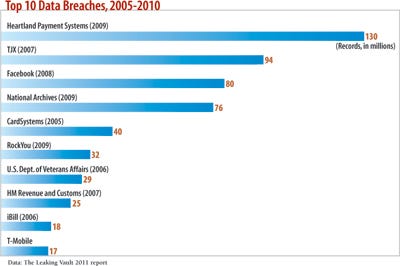
In 2008, credit card processor Heartland Payment Systems found that attackers had breached its systems and stolen details on more than 130 million credit card accounts. Heartland's security team received the equivalent of a blank check from top company execs. Its first step: Find out what systems had access to data and where legacy data had gone, CTO Kris Herrin says.
"We had the green light to do whatever it takes to find any data that might be old, historic, or legacy and get it cleaned up," he says, "so we could take a very draconian approach."
Most companies won't have that kind of support, but that's no excuse for not having the conversation.
Journey Of Discovery
Discovering where sensitive data resides is the one indispensable data security step in this process. Once you know where the data is, you can use a variety of strategies from centralizing critical data assets on a server that's highly secured and monitored to implementing a comprehensive suite of data loss prevention tools. But each strategy requires that a company first survey its systems for business-critical data so it knows what needs to be protected.
"Know where your data is from inception to disposal," advises Suzanne Widup, the author of the Digital Forensics Association's report and a veteran information security specialist. "If you do not know where it comes into the organization, where it's transformed, stored, shared with outside parties, archived, and finally how it's disposed of, you cannot hope to keep it secure."
Nearly nine out of 10 companies that suffer a breach find out about it from a third party, in many cases a credit card company, according to Verizon Business's 2011 Data Breach Investigations Report. However, 69% of those incidents could have been discovered by closely monitoring data and log files, Verizon's report says.
The lesson for companies: Get control of your information or run the risk of a breach.
Following its own breach, Heartland bought ArcSight's data loss prevention appliance and used it to scan its network to see where sensitive data was located. It found such data in log files, in the output from developers' debuggers, and in notes written by support people troubleshooting customers' problems.
DLP tools search for data in different ways. Some look for patterns indicating the leak of certain types of sensitive information. For example, they can look through log files and spreadsheets for digit patterns that indicate the presence of credit card numbers or bank transactions. They also can search for documents that match a certain template, and for specific keywords and metatags on documents.
Some companies may not even know what constitutes critical data for their business. Vector learning is included in some DLP tools to help the system learn a definition of what constitutes business-critical data for that company based on examples that the company provides.
Secure The Data
Once the sensitive data is found, the next step is to minimize the data that needs to be secured and revamp business processes that are letting data collect where it shouldn't. For companies that don't want to implement expensive data loss prevention solutions, that means taking steps to keep sensitive data off laptops and other mobile devices likely to be lost or stolen. A virtual desktop infrastructure can be used to keep sensitive data behind corporate firewalls, while still providing access to it, says Gartner analyst Trent Henry. VDI centralizes data in a closely monitored server that acts as a secure digital vault. Employees can access the data, but it isn't stored on their laptops and other remote devices.
Heartland ferreted out legacy data that it no longer needed to store, such as expired credit card numbers, and it discarded old transaction data, provided it didn't need it to be in compliance with the Payment Card Industry's Data Security Standard. It also consolidated the data it kept.
"If you can reduce your exposure and have people continue to perform their business functions, without necessarily giving them complete access to the unadulterated, unfiltered sensitive data, why not do that rather than trying to track it everywhere it goes in the enterprise," says Ryan Kalember, Hewlett-Packard’s director of solutions marketing, enterprise security.
Limiting data retention should be the top priority if you want to reduce risk from credit card and payment data, according to Verizon Business. Unfortunately, only 78% of companies meet PCI-DSS's requirements for minimizing their data footprint and eliminating personal financial data no longer needed to process transactions.
In addition to reducing the amount of sensitive data flowing through your systems, companies should consider encrypting it. Encryption doesn't protect against malicious insiders, but it does blunt the damage from accidental data leaks, such as sensitive data on a stolen laptop or misplaced USB memory stick.
Another way to protect data that's in use is to make sensitive pieces of information within a database or data store unrecognizable using a technique called masking. Using masking, whenever a copy of data is made, sensitive data like names and Social Security numbers is replaced with scrambled data that still looks realistic. Masked databases can be used for business analysis and testing without exposing sensitive information.
4 Steps
To DLP On A Budget
Use enterprise app search products to find data that's where it shouldn't be Set policies to keep employees from inadvertently misusing and misplacing data Centralize data in a well-protected server--a secure digital vault Use security appliances that are designed to secure email and Web traffic and also can detect data movement and find data where it shouldn't be
"It is a one-way hash," says Allan Thompson, senior VP of business development for Dataguise, a provider of data masking products, meaning whoever gets the data can't undo the scrambling.
Catch Data In Transit
Any company can reduce the amount of data it retains and centralize it on a highly secured and monitored server. However, far fewer companies can afford a full, enterprise-wide data loss prevention system, with multiple appliances and software agents on all protected devices. Those systems can cost hundreds of thousands of dollars.
In addition to up-front capital, companies must put policies and rules in place that "take some serious care and feeding," Gartner's Henry says.
There are cheaper options such as channel DLP, which is also more flexible than a centralized secured server. Channel DLP targets data in transit, using one or more devices to monitor network traffic inside a company, and as it leaves the network. These products use their knowledge of the various network protocols to inspect Web traffic, email messages, and file transfers for sensitive data.
Smaller DLP vendors, such as Palisade Systems and Code Green Networks, offer channel DLP products that require little management, hoping to meet the needs of small businesses. Other providers--such as McAfee, Symantec, RSA, and Websense--offer network monitoring versions of their more comprehensive DLP products to help manage a company's data policies and monitoring, without requiring that host-based agents be installed on every desktop, laptop, and mobile device. Channel DLP can catch sensitive data traveling over the network, but it would likely miss a worker copying a local database to a USB drive.
Many DLP features also are being built into gateway security appliances and online services that previously focused only on detecting attacks and malicious software. Websense's DLP product, for example, now stops confidential information from going out the door, says Tom Clare, Websense's senior director of product marketing. It also checks to see if data is using proprietary encryption and being sent to nonapproved locations.
Security information and event monitoring maker NitroSecurity argues that technology that monitors network and log traffic to detect network attacks can protect companies against the loss of sensitive data and guard against data policy violations, such as employees sending e-mail with foul language. The same scanning engine and content inspection techniques that detect attacks can be modified to catch other data of interest.
"If you protect on the network side, you don't have to go through this arduous [DLP] process," contends Mehlam Shakir, CTO at NitroSecurity. "You don't have to worry so much about the endpoints."
The Bottom Line
For companies that can afford to support a larger security infrastructure, a full suite of DLP tools will let workers take data with them and still keep it protected, minimizing the impact on business processes. Network appliances monitor communications, while software agents enforce policies.
By reducing and consolidating critical data and then using an enterprise DLP suite, IT has a much better chance of detecting and stopping attacks and leaks. "If you're monitoring the right systems, you can get to them before the data gets out," says HP's Kalember.
But a comprehensive deployment is too complex for most companies to do all at once, as well as being too expensive. "We always argue for a phased deployment," says Gartner's Henry. "You probably want to start with just discovery, or just endpoint, or just network monitoring."
Going forward, the technology should become more affordable as more security vendors provide some benefits of DLP technologies as part of their gateway appliances and other security products.
As DLP becomes more mainstream, companies that don't want to make the multiappliance investment will opt for email gateways, firewalls, and intrusion detection systems that also have some DLP features. "DLP technology is only going to become more ubiquitous--it's going to go into all sorts of different places," says Nikfar Khaleeli, group product marketing manager for data loss prevention at McAfee, an Intel subsidiary.
And that's just what businesses need as they try to protect all that elusive data that's spread out over the enterprise.
Sidebar The Dark Side Of Encryption:
Encryption is a necessary consideration in any data protection regime, but it can also pose a threat. Employees with bad intentions and intruders who gain access to data can use their own encryption software to make information unrecognizable and sneak it past a data loss prevention system.
It's possible for a knowledgeable person to use encryption and trickery to trump a DLP system, says Robert Hamilton, a product marketing manager for Symantec's DLP business. "If you're hell-bent on stealing documents … and you're clever about it, there are ways of getting around it," he says.
To detect attempts to use encryption to steal data, look for the telltale signs that workers are trying to hide information, rather than trying to decode the encrypted data itself. "There will be some anomalous access to the database. There will be a staging server. And data will be archived and hashed up into smaller files--that's a pretty consistent MO in these cases," says Ryan Kalember, VP at HP's enterprise security business.
DLP and security information and event monitoring systems can detect when employees are encrypting data in suspicious ways. Pattern analysis also can detect when encryption is being misused. --Robert Lemos
Lessons Learned From Real-World Attacks Our full Database Breaches report is free with registration.
Our full Database Breaches report is free with registration.
This report includes 20 pages of action-oriented analysis packed with 9 charts. What you'll find:
Profiles of five database breaches, and lessons learned
Six ways you can reduce your company's risk
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




