Mining malware ebbs and flows with the price of cryptocurrencies, and given the momentum on price is upward, cryptojacking is a very present threat.
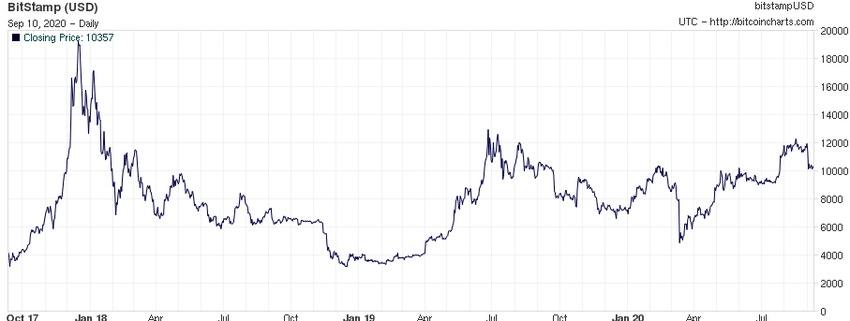
Cryptojacking isn't a new threat, but it's highly evolving. This type of mining malware tends to ebb and flow in infections with the price of cryptocurrencies. The bad news is that cryptojacking is experiencing new upward momentum in 2020. As background, 2018 was one of the biggest years for cryptomining malware development and proliferation. In 2019, there was a 40% drop early in the year, followed by a steady infection rate into 2020, with a slight uptick through August. Those trends line up with the price of Bitcoin over the last three years.
So, why is an old threat significant and timely news? Cryptojacking is heavily underreported in the security industry, and only a small fraction of what is out there, due to the nature of the malware involved, has been seen. When the mining malware is examined, it's incredibly lightweight, elegant, and easily changed. Its sole purpose is to calculate numbers using computer CPUs, and it's very difficult to differentiate between a legitimate script and a cryptominer's script. In addition, code is often so customized and benign in behavior that malware scanners overlook the code all together.
Given that cryptocurrency prices are rising, the number of Internet of Things (IoT) devices has doubled since 2017, mobile phones with web browsers are ubiquitous, and the number of vulnerabilities discovered has tripled over the same time period, we are facing a perfect storm of opportunity for cryptominers to evolve their tactics and create wormable mining malware for illicit gains.
Consider the following: An average CPU can process around 500 hashes per second on the Monero network. Servers have many CPUs, so they are a more lucrative target than IoT devices, but IoT devices are more numerous, and often a softer target (all targets, including IoT devices, web browsers, mobile phone, etc., are kept equal for the sake of this article and simplicity). At current prices, this hash rate translates to $0.21 per week per CPU from mining.
One might say that's a paltry amount, but let's put it in a different perspective. The Mirai botnet infected 600,000 devices. A cross-site scripting attack on Google search could affect 6 billion devices in a single day. There are roughly 20 billion Internet-connected devices today. Even someone who could infect 10,000 of the 20 billion instances (0.00005%) could make $2,100 a week, enough to live very comfortably in most places.
Infecting All the Devices
How do you infect 10,000 devices? The easiest way is to find exploitable software in an automated fashion. Code execution is the top reported vulnerability category the last three years running. Cross-site scripting (XSS) was the No. 1 reported vulnerability through HackerOne in 2019.
The reasons around why cryptojacking is more prolific is threefold: It doesn't require elevated permissions, it is platform agnostic, and it rarely sets off antivirus triggers. In addition, the code is often small enough to insert surreptitiously into open source libraries and dependencies that other platforms rely on. It can also be configured to throttle based on the device, as well as use a flavor of encrypted DNS, in order not to arouse suspicions.
Cryptojacking can also be built for almost any context and in various languages such as JavaScript, Go, Ruby, Shell, Python, PowerShell, etc. As long as the malware can run local commands, it can utilize CPU processing power and start mining cryptocurrency. In addition to entire systems, cryptominers can thrive in small workhorse environments, such as Docker containers, Kubernetes clusters, and mobile devices, or leverage misconfigured cloud instances and overpermissioned accounts. The possibilities are endless.
Unbalanced Scales
The goal is to minimize detection and maximize longevity. Even with cryptocurrency prices in flux, for financially motivated actors, cryptojacking is still lucrative. Resource overhead is minimal and direct profits are obtained.
Here are three reasons why we will see continued cryptojacking growth and development:
The number of potential targets is in the billions. Many devices are already infected and flying under the radar.
It's direct payout for minimal effort. There is no need for additional steps to get money, such as data brokers or via "crypto tumbling," a process similar to money laundering.
Cryptojacking is only one step removed from data exfiltration. Once a foothold is established within environments, cryptojacking could easily evolve into wormable malware, piggybacking on advanced techniques. It could also evolve into botnets for hire or data theft.
In addition to the huge number of targets, corporate data breaches are heavily underreported because laws vary by jurisdiction on when a company is required to report a breach. Because cryptojacking generally does not steal data or cause a business outage, no one is forcing victims to report an infection. The malware is stealthy to begin with, so it is underreported.
Cryptojacking can also target the biggest portion of IoT devices, often of which lack any malware detection. Unless a company has a well-established baseline and a tight budget, no one will be wiser.
Developing a Response
Evaluating macro trends is critical to developing cyber defenses for the future. Cryptojacking threats should be taken seriously as they can evolve into a security breach at any time. We should be hunting for cryptojacking threats at multiple levels:
Identifying mining algorithms at runtime rather than on disk
Full DNS inspection for all connected devices
DNS/IP alerting for known mining pools, Tor usage, or blacklisted Git repos
CPU/GPU monitoring for high usage
Temperature baseline monitoring for physical devices
In addition, more visibility into our IoT devices and containers is needed to understand abnormal baseline usage. Until the security industry as a whole is able to effectively identify this threat at scale, it will only continue to get worse.
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




