Survey finds 'lack of competent in-house staff' outranks all other forms of cybersecurity worry, including data breaches to ransomware attacks.

The top concern among CISOs for 2018 falls outside the typical realm of attacks, employee negligence, or staffing shortages, according to findings released this week in a Ponemon Institute Survey.
The top concern: "lack of competent in-house staff."
"I am not surprised that this was a leading concern - it is consistent with what we have been hearing as a critical need and gap in the market. However, being the leading concern was somewhat surprising if you follow what’s typically the most reported consequences of the staffing situation: breaches and cyberattacks," says Lee Kirschbaum, senior vice president and head of product, marketing, and alliances at Opus, which commissioned the report.
Larry Ponemon, author of the report, says he was also was surprised by the finding, adding that typically data breaches, ineffective security tools, or some other technical aspect of guarding security tops the concerns list. Workforce issues are usually somewhere in the middle, he says.
According to the survey of 612 chief information officers and IT security pros, the top five threats that worry them the most in 2018:
70%: lack of competent in-house staff
67%: data breach
59%: cyberattack
54%: inability to reduce employee negligence
48%: ransomware
A majority of survey respondents, 65%, also believe attackers will be successful in duping employees to fall for a phishing scam that will result in the pilfering of credentials – even more so than the organization suffering from a data breach or cyberattack.
"It is one of the oldest forms of cyberattacks, dating back to the 1990s, and one of the most widespread and easier forms of attacks," Kirschbaum says. "It targets one the weakest links – the human factor - and focuses on human behavior to encourage individuals to discuss sensitive information."
Challenging technologies for IT security professionals in 2018 include IoT devices, 60%; mobile devices, 54%; and cloud technology, 50%, according to survey respondents.
Over the last year or two, CISOs have been increasingly talking about how to secure IoT devices and the challenges they pose, Ponemon says. Their questions have ranged from how to encrypt a smart lightbulb to whether IoT security should rest on the company or the manufacturer, he notes.
Gloom and Doom
CISOs exhibited a general sense of gloom in their survey responses, says Ponemon.
"Maybe security people are stoic. They don't see 2018 as a year for improvement, and that security risks are becoming a greater problem," notes Ponemon.
The survey found 67% of respondents believe their organizations are more likely to fall victim to a data breach or cyberattack in the New Year.
And the majority of respondents expect breaches and attacks to stem from inadequate in-house expertise (65%); inability to guard sensitive and confidential data from unauthorized access (59%); an inability to keep pace with sophisticated attackers (56%); and a failure to control third parties' use of company's sensitive data (51%), according to the survey.
"The sheer volume of information, ranging from threat intelligence to third-party assessments, continues to increase," Kirschbaum says. "In an environment with increasing risks from new threats, new disruptive technologies, and legacy systems that continue to demand attention, companies are simply unable to bring on enough qualified staff to keep up."
Despite all the talk of an IT security labor shortage, survey respondents appear relatively optimistic that improvements may be on the horizon in 2018. According to the survey, 61% of respondents believe they could see staffing improvements in 2018. That coincides with other research that Ponemon Institute is involved with, Ponemon says.
Four years ago, a Ponemon survey found 40% of IT security respondents complained that job openings went unfilled because they could not find candidates, but that figure has since dropped to 32% based on a follow-up survey this year, Ponemon says.
Despite potential staffing improvements, CISOs and other IT security professionals foresee stress in the New Year, according to the report.
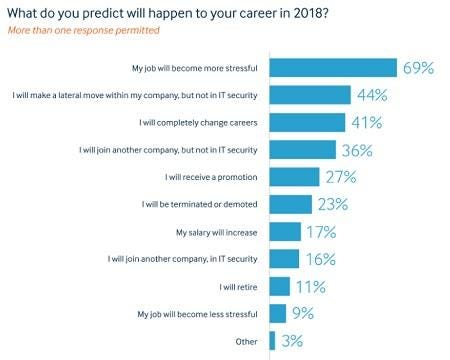
Source: Ponemon Institute Survey and Opus
"Overall, threats are multiplying, CISOs are having trouble finding in-house resources to keep up – and above all, are worried about threats they have limited control over, like the billions of new devices in the Internet of Things, each bringing with them potential new security threats and the always unpredictable element of human behavior," Kirschbaum says.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




