BEC fraud netted cyberthieves five times more profit than ransomware over a three-year period, according to Cisco's midyear report released today.

Despite all the recent attention paid to ransomware, cybercriminals walked away with $5.3 billion from business email compromise (BEC) attacks compared with $1 billion for ransomware over a three-year stretch, according to Cisco's 2017 Midyear Cybersecurity Report released today.
Cybercriminals are increasingly taking a practical approach to their pilfering, going for the fastest method that they can steal a buck, or in this case, billions, says Steve Martino, Cisco's chief information security officer. "What we are looking at is the continual commercialization of cyberattacks," Martino says, pointing out that is a major theme in the report.
Ransomware exploits take time to develop before any financial gain is realized for cyberthieves, compared to crafting a phishing attack or blasting out spam of which 8% is found to be malicious, notes Martino. BEC attacks are less time-consuming to wage.
In addition, ransomware Bitcoin fees are often lower-dollar figures.
Spam volume peaked towards the end of the year and has since tapered off a bit this year, the report found.
Exploit kits have sharply declined, according to the report. In the February to March period last year, 5,799 exploit kits were blocked. But in May, that figure has since plummeted to under 1,000 exploit kits blocked.
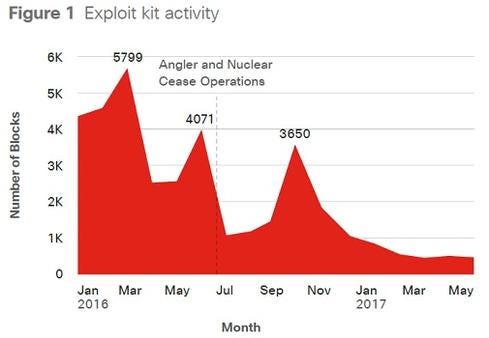 [Source: Cisco 2017 Midyear Cybersecurity Report]
[Source: Cisco 2017 Midyear Cybersecurity Report]
Malware Evolution
Cisco found that in the first half of this year, attackers altered their methods of delivering, hiding, and evading their malicious packages and techniques.
Fileless malware is popping up, which lives in memory and deletes itself once a device restarts, according to the report. As a result, it makes detection and the ability to investigate it more difficult.
Additionally, attackers are also making use of anonymized and decentralized infrastructures, such as Tor proxy services, to hid command and control activities.
Meanwhile, three families of spyware ran rampant, with Hola, RelevantKnowledge, and DNSChanger/DNS Unlocker affecting more than 20% of the 300 companies in the sample for the report.
Ironically, however, many companies and organizations underestimate or virtually dismiss spyware. "Spyware is being disguised as adware and adware, unlike spyware, does not create damages for a company," says Franc Artes, Cisco's Security Business Group architect. He adds that attackers are injecting spyware and other forms of malware into adware, since adware is a low priority for security teams.
Schooling Users on BEC, Ransomware
Cisco's Martino says targeted cybersecurity education for employees can help prevent users from falling for BEC and ransomware attacks. The finance department could especially benefit from security training on phishing campaigns, so when the bogus email comes across the transit of the CEO asking for a funds transfer it can be detected, Martino says.
"I believe in educating the right people on the matters that mean the most to them. I don't believe in sitting everyone down for 45 minutes to run through the same cybersecurity awareness training," Martino says.
Regular software patching also is crucial. When spam laden malware hits or ransomware attacks similar to WannaCry surfaces, the impact can be minimized. "People focus on new technology, but forget about patching and maintaining the infrastructure," Martino observed.
And a balanced defensive and offensive posture, with not just firewalls and antivirus but also including measures to hunt down possible attacks through data collection and analysis, he adds.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




