With the right tools and trained staff, any organization should be able to deal with threats before information is compromised.
Why are we so good at identifying attacks but so bad at preventing them? Every day, we hear of new organizations getting hacked or old targets getting tagged again. Clearly, our defenses are not getting the job done. However, forensics experts have been able to quickly retrace each attack sequence, identify details about which systems were compromised, and determine how much information leaked. That is only possible if the necessary clues were collected during the attack.
Obviously, we are solving the challenge of identifying important details and retaining that information. We are becoming adept at mining that information once we know what to look for. The failure comes in connecting dots in real time as hackers (excluding those spreading ransomware) hide within our networks for hundreds of days before detection. As a result, they have time to conduct reconnaissance, escalate privilege, and exfiltrate information with increasing regularity and severity.
Why are hackers able to hide for so long? Imperva reports that 27% of security professionals receive over 1 million alerts per day and most receive over 10,000. Those are overwhelming numbers. No team can effectively respond to that many incidents. Most alerts are false positives that suck up resources to investigate and make it impossible to automate responses — the impact would be more damaging than the attacks.
On the other hand, we already see the impact of not responding. No defenses will survive well-trained, determined attackers free inside the organization for an extended period. If unable to achieve their goals initially, the attackers collect credentials, expand footprint, and catalog defenses. When a new exploit is available, the hackers have a list of potential targets. Each exploit creates a race to see if the hackers can exploit vulnerabilities in their catalog of devices before the ops team can patch systems. Given enough time and exploits, the hackers will win a race and penetrate defenses. Attacking becomes a numbers game that is clearly in favor of the hackers.
How can an IT team survive continuous assault? Social engineering attacks allow hackers to bypass firewalls with some regularity. Detecting intruders quickly and completely removing them is key. As described above, most organizations already have systems in place that are detecting attacks and logging evidence. This information needs to be processed in real time and without the false positives.
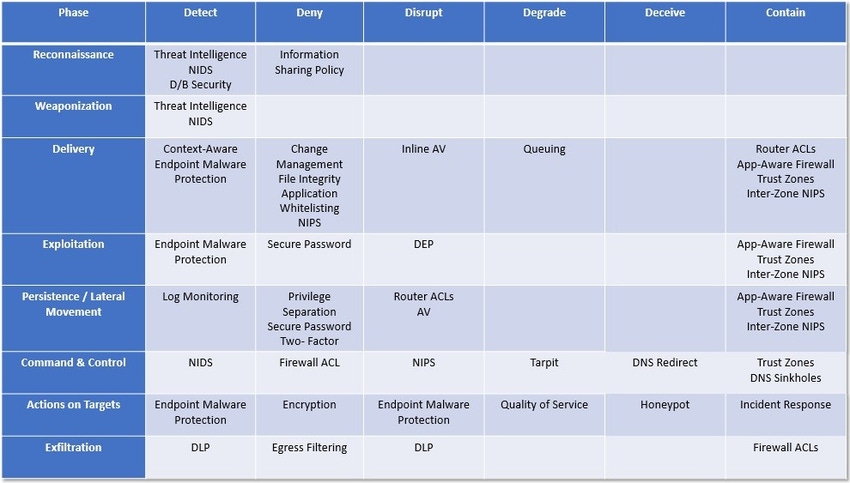
The cyber kill chain (CKC) is a great framework to start organizing network and application defenses. I like this version of the framework because it provides a little more detail on containing an attack than most others. (Most models seem to portray containment as dealing with lateral movement.) The framework makes it easy to catalog types of attacks and develop strategies to intercept them.
Using the CKC, make sure you have tools in place to at least "Detect," "Deny," and "Contain" attacks. Just detecting hackers is insufficient because that only helps identify what information has been stolen. You want to block or at least stall them long enough to give security team time after detection to remediate the issue.
Next, identify which alerts are actionable and map those alerts to boxes in the CKC. These are the alerts that quickly resolve issues. They must contain detailed information about the attack such as source, target and any confirming information. For example, an attempt to log in to a honeypot should result in an alert indicating which machine is being attacked, where is the attacker coming from, and whose credentials are they using. Actionable alarms represent the best bang for the buck for the support team. Other alerts might be helpful for an attack postmortem, but don’t provide real protection. Make sure your SIEM escalates actionable alerts for immediate resolution. Secondarily, escalate the most informative alerts for each block in the matrix. Hopefully, taking care of priority issues will eliminate enough symptoms to enable some investigation into secondary warnings.
Reassess the effectiveness of your defenses using the CKC framework but only include reliable, actionable indicators. This provides a true picture of information security posture. For remaining boxes, check with existing tool vendors to see if they have plans to make their systems more actionable and less noisy. Find solutions to cover remaining gaps.
Review the operational value of each tool. If a tool is not providing enough useful information, or is generating too much noise, replace or eliminate it. With all the low-commitment software-as-a-service solutions available, it is easier than ever to swap tools. The goal is to build a CKC filled with actionable, effective tools that can:
Detect attacks at each stage in the chain from inside and outside the organization.
Provide actionable information to remediate the attack,
Block the attack long enough for the security operations center to respond (bonus points if the hacker is deceived or disrupted as well).
Quickly restore systems to a clean state.
With the right set of tools and trained staff, any organization should be able to deal with threats before information is compromised.
Related Content:
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




