By understanding how cybercriminals use bitcoin, threat analysts can connect the dots between cyber extortion, wallet addresses, shared infrastructure, TTPs, and attribution.
Cryptocurrency, particularly bitcoin, has captured the attention of Wall Street and Silicon Valley over the past few months. It seems like everybody wants to talk about bitcoin as if it is something brand new.
The truth is that cryptocurrencies have been the norm on the Dark Web for quite some time. Bitcoin has been payment method of choice for ransomware and cyber extortion because it allows bad actors to operate under a cloak of anonymity. But that could be changing. Threat intelligence analysts are beginning to incorporate bitcoin wallet addresses into their investigations, and we'll soon be able to recognize attack patterns and track attribution. One thing we've noticed is the ability to track, to some degree, the correlations and connections between cyberattacks by following bitcoin transactions.
In order to understand why tracking bitcoin wallet addresses as indicators of compromise (IOCs) is so valuable, we need to understand why cybercriminals use bitcoin in the first place. There are three primary reasons.
Anonymity: Bitcoin provides anonymity when payments are received and when they are cashed out. That's because bitcoin accounts and money transfers are difficult to trace and depend largely on the cybercriminal being sloppy with operations security.
Global Currency: Hackers typically prey on out-of-country targets and need a fast, untraceable method to transfer funds across nations without worrying about account freezes. Bitcoin is used as a global currency because you don't need to worry about the exchange rates between your home country's currency and US dollars.
Ease of Payments: In the past, hackers used to rely on gift cards for payment. This was troublesome on many levels — for instance, gift cards can't be used globally, and criminals needed to come up with a mailing addresses that can't be traced. Bitcoin and the higher profile of cryptocurrency have contributed to the rise in ransomware, as well as hackers' ability to use extortion to elicit payments. One example occurred after the Ashley Madison website breach, when hackers threatened some users with a bitcoin ransom or have their identities revealed as adulterers. Another tactic involved using malicious emails to threaten a distributed denial-of-service attack on an organization's network unless a bitcoin payment was made.
By tracking bitcoin wallet addresses as an IOC, we've been able to connect the dots between ransomware, wallet addresses, and shared infrastructure, TTPs (tactics, techniques, and procedures), and attribution.
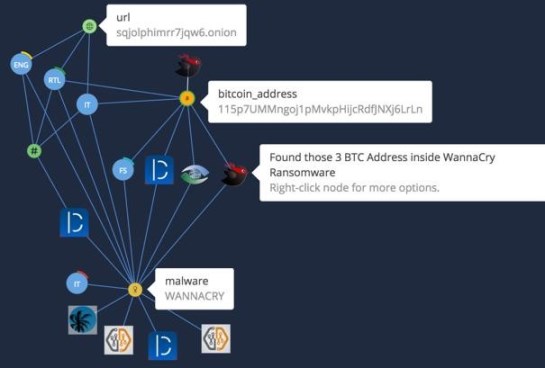
Here is an example of how bitcoin is used in a ransomware campaign: A new piece of ransomware gives you a bitcoin address for payment. You can then make correlations that connect across sectors, like retail, energy, or technology groups based on the blockchain and/or reuse of the same address. With WannaCry, there were hard-coded bitcoin addresses that made it easy to correlate what you are dealing with and which sectors were being affected. The more bitcoin addresses are shared, the more you can identify addresses to which bitcoins are forwarded.
The ability to track transactions through the blockchain allows you to connect different ransomware campaigns. Cybercriminals don't typically share bitcoin wallets as they might share the same exploit kit, but by tracking blockchain transactions, analysts have another investigation point from which they can pivot and dig for more.
Why is it important to be able to track bitcoin wallets as IOCs? With the ability to track payments, you can determine if bitcoins are going to specific wallet addresses, and then narrow that down to determine if they are the same two or three addresses over time. This will give you some idea of where and when cybercriminals are cashing out.
The value of the metadata as an indicator for malicious activity is because, although there are many variants of ransomware, the number of variants does not necessarily represent separate campaigns or cybercriminal groups. If you can follow the transactions through the blockchain, you can see how or if these variants are connected, and identify specific campaigns.
There is a well-known saying that if you want to know where trouble is coming from, follow the money. It's hard to follow bitcoins, but all of those bitcoin wallets can help you see how ransomware is connected.
This research was provided by the TruSTAR Data Science Unit. Click here to download the top ten bitcoin addresses with the highest IOC correlations on our platform.
Related Content:
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




