Researchers find booming underground market for stolen and fake email credentials from the 300 largest universities in the US.
March 29, 2017
.jpg?width=850&auto=webp&quality=95&format=jpg&disable=upscale)
Stolen email addresses and passwords from the largest US universities are offered for sale on the Dark Web at anywhere from $3.50 to $10 apiece.
But that's only a snapshot of a lucrative underground market for pilfered – and even spoofed and phony - student, faculty, staff, and alumni email credentials, according to new research published today by the nonprofit Digital Citizens Alliance (DCA) that searched the Dark Web for credentials from the top 300 US universities.
With the help of research firm ID Agent, they found 13,930,176 credentials from those big schools, with the University of Michigan (122,556), Penn State (119,350), University of Minnesota (117,604), Michigan State (115,973), and Ohio State (114,032), with the most credentials for sale, and MIT with the biggest ratio of stolen and spoofed email addresses to number of enrolled and staff, 2.81:1, followed by Carnegie Mellon University, 2.4:1, Cornell University, 2.39:1, and others.
"I've been scraping the Dark Web since 2009. There were 2.2 million .edu [emails] there back in 2015, 2.8 million in 2016, and now almost 14 million a year later. That's a significant spike," says Brian Dunn, managing partner at ID Agent.
.jpg/?width=100&auto=webp&quality=80&disable=upscale)
Source: DCA
Dunn says the massive increase likely has to do with third-party website breaches, where university users register with their .edu email addresses with social media, e-commerce, and other websites that suffered breaches, either reported or unreported. "There have been significant third-party breaches in 2016," he notes. ID Agent has seen a 547% increase in all types of credentials (including universities') for sale in the Dark Web over the past three years. Think big breaches at Yahoo, DropBox, LinkedIn, and others.
The caveat, however, is that the researchers don't know how many of the stolen passwords are valid (they can't legally confirm that). Also, some of the emails are spoofed or phony, but DCA notes that doesn't mean they aren't a danger to a university: spoofed emails are often used in phishing attacks. Also, the report only looked at the largest US universities, so other high-profile but smaller-enrollment universities weren't included.
Purveyors of the .edu credentials in the Dark Web are typically cybercriminals, hacktivists, and scammers, the researchers say.
"[The] .edu [domain] is a generally valuable email domain just like .gov and .mil," Dunn says.
Buyers can use those stolen credentials to cash in on university discounts, such as software and Amazon Prime memberships, for example. They also can use them for phishing or gaining further access to university financial, research, and other potentially lucrative information.
Many breaches of all types begin with stolen user credentials. Dunn says one of his firm's clients estimates that 94% of network login attempts are executive via automated scripts of reused credentials. "When you [an attacker] can automate that with a script, you can have tremendous amount of success."
A University of Michigan spokesperson said the majority of the U-M credentials found in the study likely were the source of students, staff, and alumni, using their school email address when registering for third-party websites, and they don't indicate any new threats to the university. Even so, "we explicitly discourage" using UMICH passwords for other online accounts.
"Our Information Assurance group, and other Big 10 IT security organizations, have analyzed the report and have determined that there is no new risk or significant threat to the university's systems or data," the spokesperson said, adding that the university has tools and processes that "help limit any exposure" when user accounts are compromised.
But the spokesman pointed out that "there is no evidence that the accounts and credentials were valid - at U-M or elsewhere."
Ohio State University said DCA's report doesn't indicate any new threats to OSU. "Together with our peer institutions, the university has reviewed the report and determined that there is no new risk or significant threat to the university's systems or data. Ohio State has a robust security framework which complies with industry standards and includes a number of technology tools and processes to limit exposure for potentially compromised accounts," an OSU spokesperson said in a statement.
Hacked university emails and credentials have been in the spotlight plenty of times before. The Research and Education Networking ISAC (REN-ISAC) last year notified universities about the compromise of some 2.2 million user credentials. And back in 2012, the hacktivist group Team GhostShell dumped on Pastebin some 36,000 names, email usernames and passwords, phone numbers, and other personal online information of students, faculty, and staff from 53 of the largest universities in the world, including Michigan, Harvard, Stanford, Cornell, Johns Hopkins, and Carnegie Mellon.
DCA, while working on its project, reached out to Team GhostShell via Twitter and ended up communicating via email for several months with a member of GhostShell who claimed to be the the leader of hacktivist group Team GhostShell, "DeadMellox," who last year came out of the shadows and gave his name as Razvan Eugen Gheorghe, 25, based in Bucharest, Romania. Razvan told the DCA that the data he leaked was only the tip of the iceberg and higher-ed personal information is constantly being abused.
In an email exchange with Dark Reading arranged via DCA, Razvan pointed out that the higher-ed credentials for sale in the Dark Web represent a small portion of the overall problem. "The findings themselves of those so called millions of stolen credentials represent a spec of private information compared to the overall hacking that's being done on a daily basis all around the net," he wrote.
Razvan, whose identity as DeadMellox could not be confirmed by Dark Reading, said it's up to the higher-ed institutions to school their users on security threats. "It's better to have young students and people in general learn about cybersecurity from their schools, rather than some shady hacker marketplace online," he said in the email.
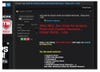
Source: DCA
The basic goal of the DCA report was to shed light on the Dark Web's abuse of .edu email accounts and credentials. "We wanted to give their [universities'] IT security teams something they can use and talk about with administrators and stakeholders on the scale of the problem … what kind of challenges they are facing," says Adam Benson, deputy executive director of DCA.
University email accounts are juicy targets for opportunistic cybercriminals: "Some of these schools have thousands of people coming in every year with different levels of sophistication, and education about financial and medical records [for instance]" and may be using a credit card for the first time, he says.

Related Content:
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


