News, news analysis, and commentary on the latest trends in cybersecurity technology.
Organizations do not have good visibility into all the software-as-a-service applications that connect to and access data stored in core business.
While software-as-a-service helps organizations improve productivity and agility, it also adds complexity to the enterprise environment as IT security teams need to have visibility over the data stored in each of the applications.
And when organizations integrate SaaS applications with other SaaS applications, the attack surface grows even more because more applications have access to the corporate data. For example, connecting Asana to Google Workspace gives the task management platform access to data stored in the productivity suite.
In a recent report from Valence Threat Labs, 56% of CISOs said they don't have a process in place, or are not satisfied with the process they have, for discovering and managing SaaS-to-SaaS connections and integrations.
Understanding SaaS Mesh
SaaS mesh refers to connecting a SaaS application with another SaaS, using methods such as OAuth and API tokens, low-code/no-code workflow, and SaaS marketplaces. Examples include using third-party platforms such as Heroku to access GitHub repositories via OAuth user tokens, or creating and sending email campaigns from the organization's website using the API instead of logging into Mailchimp's platform. It is possible to complete a task in Asana and have a corresponding notification message be printed in Slack.
Connecting SaaS tools to core business applications such as Office 365, Salesforce, and Google Workspace within a SaaS mesh helps enhance the organization's agility, productivity, and collaboration. However, if the mesh isn't managed correctly, it can expose data stored in business-critical applications, according to Valence Threat Labs.
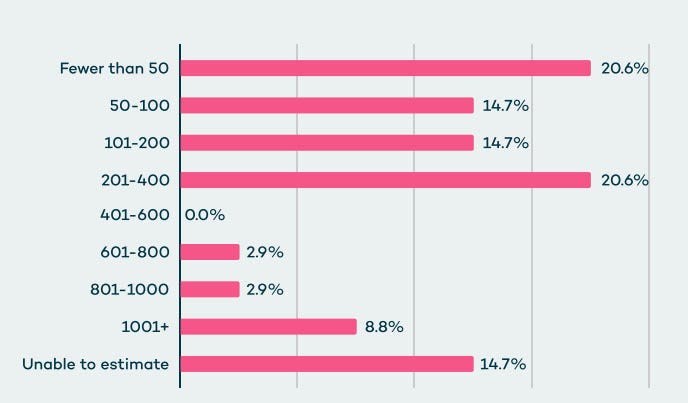
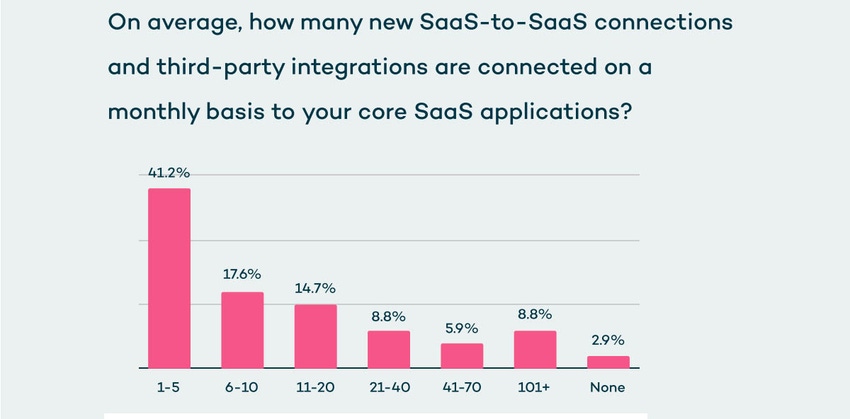
The average organization uses around 80 SaaS applications — BetterCloud estimates that organizations with more than 1,000 employees use more than 150 applications, while organizations with 50 employees or less use only 16 SaaS applications. When asked how many SaaS-to-SaaS connections and third-party integrations are connected to core SaaS applications (such as Office 365, Salesforce, and Google Workspace), 50% of CISOs said they have 200 or fewer integrations, or that they didn't know, Valence Threat Labs found.
In actuality, the average organization has 917 SaaS-to-SaaS third-party integrations, according to Valence Threat Labs.
While 76% of CISOs think under 20 new integrations are added every month to their environment, in reality, 76 new third-party integrations are onboarded every 30 days.
Over-Provisioned Connections
When asked if they had a process in place to determine if an integration is overprivileged, 53% of CISOs in the Valence Threat Labs report said they didn’t. This is a problem because nearly half, or 48%, of SaaS integrations (443 integrations, to be specific) are unused, and many of them have more privileges than they need. A SaaS-to-SaaS integration is usually inactive because someone forgot to turn it off after testing out the integration and then deciding not to use it. But because the integration is still there, someone else who gains access to one application now has access to the other and can move laterally.
"Most organizations do not have a continuous process in place that allows them to assess the business justification of non-human identities and properly offboard unnecessary third-party vendors," Valence Threat Labs said in its report.
Low-code/no-code platforms such as Workato, Zapier, and Microsoft Power Platform are powerful because non-developers can pull together workflows to access data from multiple sources. However, if they aren't configured correctly, they can expose data erroneously. Because these platforms often are not managed by application security or IT security teams, CISOs may not even know these tools exist or are accessing business applications. In the Valence Threat Labs report, 35% of CISOs said they do not have low-code/no-code platforms in their environment, when it turns out over 96% of companies have at least one such platform in use. In fact, the average organization has four or five, according to the report.
In the report, 85% of CISOs said they did not have appropriate visibility and protection from the risks of SaaS-to-SaaS connections and third-party integrations. "The fact that 85% of CISOs were unhappy with the current solutions suggests the need for more solutions specifically designed to protect the SaaS mesh," Valence Threat Labs said in its report.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024