
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Criminals will keep stealing end-user credentials despite employee awareness, so organizations need high-tech solutions as well.
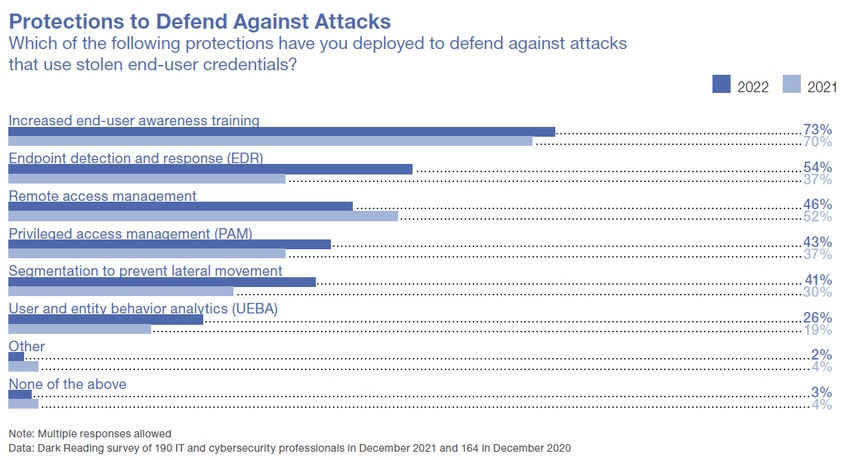
In the endless battle to secure endpoints, companies are still emphasizing user training to avoid phishing and other social engineering gambits. However, rapid growth in tools like endpoint detection and response (EDR) and user and entity behavior analytics (UEBA) reveals the understanding that educating employees isn't sufficient to protect against hacks — you need to find advanced solutions to counteract new attack techniques.
The results come from Dark Reading's "2022 Endpoint Security Survey," which polled 190 cybersecurity and IT professionals on how pandemic-related changes affect their endpoint security strategies.
In the above graphic, the darker blue bars represent results from the 2022 survey, while the lighter blue shows 2021 numbers. At first glance, user training is clearly the top choice for defending against attacks; not only is it the most universally adopted countermeasure, at 73% of respondents implementing it for 2022, but it has grown from 2021's 70%. But the funny thing is, almost every category has also grown.
EDR has displaced remote access management as the second-most implemented measure. Last year, remote access management was used to secure endpoints by 52% of respondents, with only 37% using EDR to detect and respond to threats. This year, remote access management was the only technique to fall in popularity; it dropped to 46%, while EDR rose to 54% in 2022.
To protect against misuse of credentials, 43% of respondents apply privileged access management (PAM), up six points from 2021's 37%, and 41% segment their networks to prevent lateral movement following a breach (up 11% from 2021's 30%). Over a quarter of companies (27%) are now employing UEBA to try to catch intruders by monitoring expected user behavior and watching for anomalies; UEBA stood at only 19% in 2021.
Stolen access credentials are a hot commodity on the black market, with privileged accounts particularly valuable. Indeed, the Colonial Pipeline attack started with access granted via a stolen VPN account. And a 2021 report showed that stolen credentials were the most expensive insider threat, costing an average of $805,000 to remediate.
For more, read the full report.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

