Attackers are becoming more sophisticated in their obfuscation and anti-analysis practices to avoid detection.
September 3, 2019
As cybercriminals continue to hone their attack approaches, they are also tuning their post-intrusion models. Many modern malware tools already incorporate features for evading antivirus and other threat detection measures, but research shows that attackers are also becoming more sophisticated in their obfuscation and anti-analysis practices to avoid detection if an infiltration attempt is successful.
Based on analysis of data from Fortinet's "Q2 2019 Threat Landscape Report," this article examines a recent spam campaign that used novel anti-analysis and evasion techniques.
Anatomy of a Spam Attack
Many modern malware tools include features for evading antivirus and other threat-detection measures. Examples include routines that enable the malware to detect when it is running within a sandbox environment, functions for disabling security tools on an infected system, and the use of junk data to make disassembly harder.
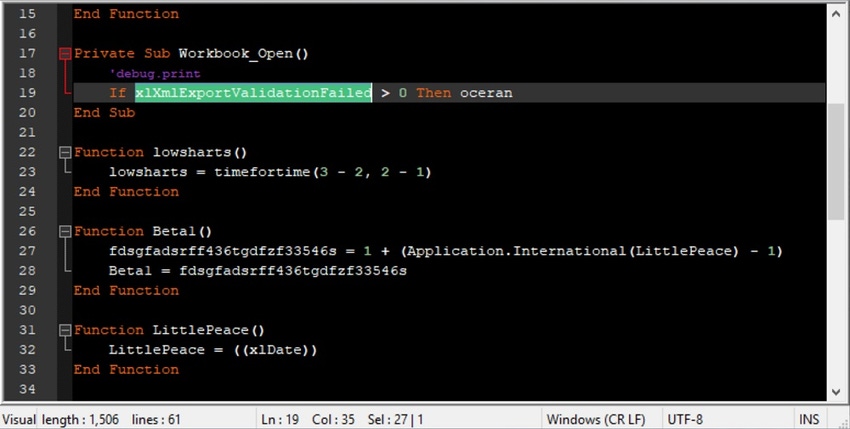
A good example of how adversaries are tweaking these anti-analysis techniques can be found in a macro that was used in a major spam campaign in Japan last quarter. This campaign involved a phishing email with a weaponized Excel document attached that contained a malicious macro. Our analysis showed the macro had attributes for disabling security tools, executing commands arbitrarily, and causing memory problems — and also ensuring that it would run only on Japanese systems.
The macro used in the Japanese spam campaign, like much other malicious software, was designed to look for certain Excel-specific variables at multiple points during execution to ensure it was running within an Office Excel environment and not in an emulator. One Excel property that it looked for in particular — the xlDate variable — was something that we haven't observed before in other malware. Interestingly, the variable appears to be undocumented in Microsoft's documentation —at least, we were unable to find it.
The use of such anti-analysis techniques, though nothing new, appears to be growing. In June, for example, security researchers found a new variant of the Dridex banking Trojan that evaded several traditional antivirus tools by using 64-bit DLLs with file names of legitimate Windows executables. The file names and associated hashes changed each time the victim logged in, making it hard for signature-based antivirus tools to spot the malware on infected host systems. This Dridex variant also took advantage of a known weakness in the Windows Management Instrumentation Command-line (WMIC) utility to bypass application whitelisting measures and execute malicious VBS code embedded within an XSL file.
Multiple reports of downloaders with sophisticated, built-in defense-evasion techniques also appeared in the second quarter. One example is AndroMut, a downloader that the Russian-speaking TA505 group used in a campaign targeting individuals working at financial companies. AndroMut's anti-analysis features include sandboxing and emulator verification and checks for mouse movement and debuggers. At least two other downloaders — Brushaloader and a new version of JasperLoader — were reported in the second quarter as having similarly advanced evasion mechanisms.
Best Practices
Here are five best practices you can implement to build or expand on a multilayered defense strategy.
Add this anti-analysis trend into your current risk analysis strategy. Your IT team needs to know about this risk and consider options, such as storing system backups off-site, putting redundant systems in place, and being able to lock down segments of the network when an attack is detected.
Inventory all critical assets and services across your network. Expand your efforts to identify and patch vulnerable systems, replace older systems that are no longer supported, or enhance compensating security tools. This will likely involve implementing some sort of asset-tracking and management solution.
Segment your networks. Segmentation can be used for a variety of security purposes. For example, you can keep Internet of Things (IoT) and similar devices automatically separated from your production network until they can be properly secured. This should also be tied to device authentication and network access control at access points. This enables you to identify and authenticate devices, manage access, inspect traffic, and then assign it to secure network segments — all at wire speed. You also need to set up checkpoints to monitor traffic that passes between network segments looking for anomalous behaviors, malware, and other sophisticated attacks.
Inspect encrypted traffic. It takes 50 to 100 times more processing power than conventional traffic to perform deep inspection of encrypted traffic and unstructured data, such as the raw data produced by many IoT devices. Unfortunately, most security devices and may need to be upgraded to do this.
Automate event correlation. In today's high-performance environments, you can't afford to hand-correlate threat data to detect threats or respond at anything less than machine speeds. To address this issue, you must be able to automatically collect and correlate real-time threat intelligence to identify and stop an attack before it can deliver its payload or extract the data it's looking for.
Future-Forward Security
Malicious actors aren't only creating new ways to access your network but are also developing new ways to remain undetected once in and do as they please for as long as they like. By understanding the risks and putting the right defenses in place, your organization can defend itself against not only these latest attack trends but also those that have yet to be devised.
Toward that end, FortiGuard creates adversary playbooks based on its role in the Cyber Threat Alliance. These playbooks describe the tools, techniques, and steps that adversaries use to achieve their goal. The goal is to enable IT security teams to disrupt malicious actors more systematically. The most recent playbook dissects Zegost, an info-stealer used recently against a Chinese government agency, and is available here.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "'It Saved Our Community': 16 Realistic Ransomware Defenses for Cities."
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "'It Saved Our Community': 16 Realistic Ransomware Defenses for Cities."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




