Secure code development should be a priority, not an afterthought, and adopting the software development life cycle process is a great way to start.
The increasing dependence on software in every aspect of our lives makes us more vulnerable to cybercrime. Not only are breaches getting more ingenious and frequent, but they are also getting more expensive in terms of cost and damage to reputation. The average cost of a data breach is $3.86 million, up 6.4% from last year. Even more unnerving: 60% of small companies go out of business within six months of an attack.
Organizations are actively responding to the rising threats — $1 trillion is expected to be spent globally on cybersecurity from 2017 through 2021, according to Cybersecurity Ventures. However, for cybersecurity to successfully thwart attacks, we need to be proactive in patching code as it is developed rather than being reactive and fixing it after deployment. What's required is a multipronged strategy with security built in, in a sustainable manner from the first line of code.
The secure software development life cycle (SDLC) process is gaining ground as an effective methodology to do precisely that by integrating activities such as penetration testing, code review, and architecture analysis into the SDLC.
What Is a Secure SDLC?
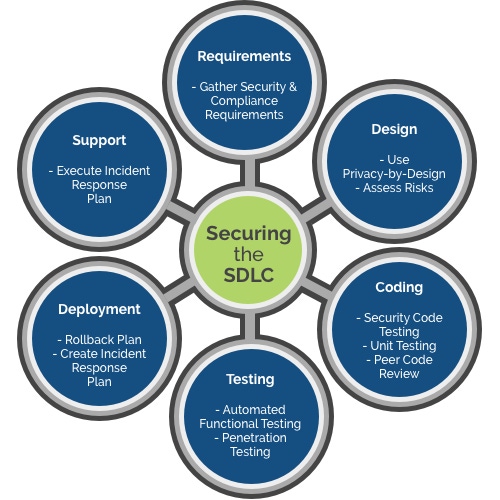
Here is a quick visual snapshot of the Secure SDLC:
Why Is the Secure SDLC a Necessity?
Vulnerabilities that creep into software because of minor kinks and overlooked aspects can be successfully dealt with only when security becomes a continuous concern. The Secure SDLC does that — and more. Here are three key areas where the Secure SDLC shines.
#1 Creates a Security-focused Culture
The Secure SDLC provides a practical framework to realize a security-focused culture.
#2 Mitigates Risks
Baking security in from requirements gathering and design leads to more predictable deployments, fewer rollbacks, and higher customer satisfaction.
#3 Cost Benefits
It is almost 100 times more expensive to fix security flaws in deployed software than during the requirements stage, thus reducing a project's overall expense.
Tips to Implement the Secure SDLC
Select a Secure SDLC Model
The first step to implementing the Secure SDLC is picking a model. Here are some commonly used models:
Get Buy-in, Train, and Champion
After finalizing your methodology, the next step is to get buy-in, train, and champion. As with the adoption of any other organizationwide process change, for it to be a success, the triad of executive buy-in, companywide training and dedicated security champions are a must.
While stakeholder buy-in is needed to drive change across the various teams, developer, tester, and analyst buy-in is critical for Secure SDLC, too, because it fundamentally alters the way they develop, test, and analyze. Those three groups need to fully grasp the benefits of including security and testing right from the nascent stages. Architects, developers, testers, and analysts must be trained to maintain a security-focused "privacy by design" (a GDPR requirement) mentality/development process that infuses security from the time requirements are gathered. Some ways include:
● Architects and analysts need to perform architecture reviews and threat modeling. Using tools like the OWASP Top Ten, they must understand critical web application security risks. Decisions about the design and app infrastructure — technology, frameworks, and languages — need to be made with regulatory considerations and possible vulnerabilities in mind.
● Developers should add security code testing and security plug-ins to their daily coding routine/IDE. They need to adopt secure coding standards, static code analysis, and unit testing along with peer code reviews during the development stage. Checks should be put in place to update software, libraries, and tools on a regular basis to address vulnerabilities.
● Quality analysts need to thoroughly execute test plans with the help of automated testing tools and perform penetration testing on the final product.
● While the Secure SDLC can be kick-started with security champions, a dedicated software security group is a must for a sustainable implementation. It is an effective way to educate, assess, and enforce established security measures across the organization.
Building a Culture of Security
Secure code development should be a priority, not an afterthought. The benefits are significant and well worth the additional time and effort. Building a culture of security with the help of tools, processes, and training, is the strongest offense against the onslaught of malware, spyware, viruses, worms, Trojans, adware, and ransomware.
Related Content:

Black Hat Europe returns to London Dec. 3-6, 2018, with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions, and service providers in the Business Hall. Click for information on the conference and to register.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




