Cyber criminals often go after your enterprise data by preying on your end users. Here are ten of the most current exploits to watch for
August 1, 2013


Download the Dark Reading August special issue on Web-based attacks
Download Dark Reading's August special issue on Web-based attacksWith so much of today's business conducted via the Web -- on so many types of devices -- cybercriminals smell blood in the water. Employees share more information than ever and connect to more outside networks than ever, making them subject to the threats posed by opportunistic attackers.
Every day, criminals devise new malware and social engineering attacks that target what has become an organization's weakest link: end users and their Web-connected devices. Here are the most common attack methods and social engineering techniques, and ideas on how to stop these attacks before they infect end user devices and work their way into your corporate data.
1. Drive-By Downloads
Drive-by downloads are a central part of many of the most sophisticated Web attacks that criminals perpetrate against online users. They are so dangerous because they require no user action to download malicious content onto an endpoint. What's more, these attacks are often unleashed from legitimate sites.
Drive-by downloads are typically deployed by hackers who have taken advantage of Web vulnerabilities such as SQL injection that can be exploited to "allow attackers to change the content of a website," says Chris Wysopal, CTO at the app security testing company Veracode.
Once implanted on a site, drive-by downloads typically take advantage of browser vulnerabilities to automatically download anything from full-fledged viruses to less detectable downloader apps that will trick the user into eventually loading malware onto the machine via a button press or click.
"They can be encountered in the wild, or users could be directed to them via social engineering attacks," says Patrick Thomas, security consultant for Neohapsis, a mobile and cloud security firm. Drive-by-download attacks are commonly part of commercial exploit kits that make it easy for a nontechnical criminal to deliver an attack. These kits provide code that can automatically fingerprint a browser version and choose an exploit most likely to work against it.
More often than not, drive-by download attacks depend on vulnerabilities that browser vendors have already discovered and fixed, so patching is critical to protecting against them, Thomas says. Patch cycles of two to three months aren't fast enough to keep up with the latest threats.
Also, IT should "include browsers in patch reports and make sure that alternate browsers are considered in your enterprise patch management," he says.
2. Clickjacking
If the attacker requires extra interaction from the user to load malware, this will be accomplished through an attack called "clickjacking."
"The purpose of this attack is to open the target website in an invisible frame and get the user to click somewhere in the frame when they don't even know they're clicking in that website," says Ari Elias-Bachrach, application security consultant and trainer for security consultancy Defensium. "In this way, you can trick the user into making a mouse click that does something [malicious] on the website."
A common example is offering a bogus pop-up window made to look like a legitimate plug-in update or antivirus alert, such as a Microsoft Security Essentials window that says you have a few viruses and should push a button to clean them. "The pop-up itself is not harmful, but if you click the button, you open the gate to infect your machine," says Rick Doten, chief information security officer for DMI, an enterprise mobility company.
Users should be educated about how an organization's antivirus upkeep works to keep them from falling for these more obvious ploys. They also should be apprised of another variation of clickjacking called likejacking, which tricks users into clicking on a predictable location on a page containing an invisible link. The term was coined because often the link is placed over something such as a Facebook "like" button, so that the user not only stumbles into something malicious but also promotes the attacker's page on his Facebook wall in the process. Another form of likejacking can happen when an attacker posts a fake video to get users to click the play button. "More advanced likejacking scams will even use JavaScript to create a dynamic link that follows the user's mouse to ensure that any click, regardless of location, hits its intended target," says Michael Sutton, VP of security research for cloud security vendor Zscaler.
3. Plug-In- And Script-Enabled Attacks
Not only do attackers look for vulnerabilities within the browser itself, they also frequently ferret out bugs in browser plug-ins and scripting programming to help them carry out drive-by downloads and clickjacking attacks.
Since these attacks rely on known vulnerabilities, "make sure users keep browsers and browser plug-ins updated to the latest versions by enabling auto-update functions," says Wolfgang Kandek, CTO of vulnerability management firm Qualys.
In some cases, it may also make sense to turn off scripting within the browser and other susceptible programs, such as Adobe Reader. Similarly, uninstalling certain problematic plug-ins can reduce the attack surface within susceptible user bases. But you'll still need to put controls in place and train users not to undo the work.

"Users often just 'allow all scripts on page' when the site doesn't load correctly," DMI's Doten says.
In particular, companies should be wary of Java. It's one of the most susceptible languages to attack, and Java is a favorite among criminals to begin Web attacks that can get them deep within an enterprise network. Unless there's a pressing need for a business application that requires Java, IT should uninstall the plug-in altogether, recommends Andrew Brandt, director of threat research at Solera Networks, a network security intelligence company. Many attacks do spawn a pop-up message from Java asking for permission to execute a malicious Java file, but it's often too hard for users to tell which browser window created the pop-up.
"One accidental 'allow' click is all it takes to start the ball rolling," Brandt explains. "Once the malicious Java applet is running, it takes only seconds for the malware payload -- a Windows application -- to arrive, execute and do its dirty work."
In many of the current versions of Java-based attacks, users might see a small window labeled 'JNLP' appear in the taskbar, he says. This can be an indication of compromise, so educate users to look out for such a red flag.
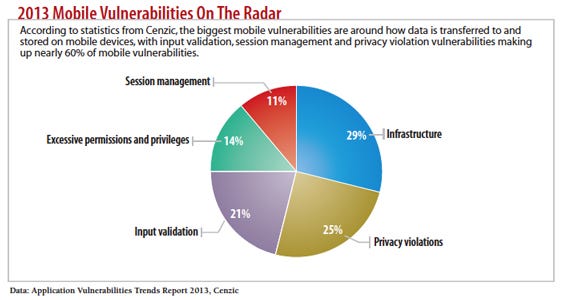
Most common attack methods
4. Advanced Phishing Attacks
While phishing attacks are typically associated with email, most are perpetrated via links to malicious content on the Web, whether a simple password capture form used in traditional phish attempts or a malicious drive-by download in more advanced targeted attacks.
Phishing attacks are designed to trick users into thinking they are a link from an organization or person they know, making people feel safe enough to click or divulge information they otherwise wouldn't. Many corporate security training programs have helped users spot the most obvious first-generation phishing attempts, which were designed to steal credentials such as banking passwords. But attackers are getting more crafty.
"Often, these attackers will perform reconnaissance on a specific target, then craft a sophisticated pretext or story to ensure the likelihood of success," says Scott Behrens, head of Neohapsis Labs.
These so-called spear-phishing attacks may single out an executive and barrage that person with specially crafted emails tailored to her interests based on research done online.
"Getting basic information about a person often requires little more than a Google search," says Benjamin Caudill, co-founder and principal consultant at Rhino Security Labs, a security consulting firm. "Many times in penetration testing, when unsuccessful with a mass email, I've been able to spearphish the CEO by replicating an email and link from his alma mater and getting direct access to his system."
In addition to spear phishing, credential-stealing mass phishing attempts are making a comeback thanks to increasing use of mobile devices.
"Unlike desktop browsers, mobile devices typically do not display the actual URL links, so there's no red flag alerting users to potential danger," says Chris Larsen, malware lab architect for Web security firm Blue Coat.
Users should look for telltale phishing signs such as misspelled words and links on their desktop browsers that don't go where the hyperlink supposedly points, Larsen says. And mobile users should be encouraged to inspect the URL by dragging down the URL bar on their browsers after clicking links, if their browsers automatically hide URLs. That's especially important if a site asks for login credentials and other personal information.
5. Social (Engineering) Networks
Millions of people sharing information on social networking sites such as Facebook, Twitter, LinkedIn and Google+ creates "an ideal attack bed for someone who wants to socially engineer a target individual, group of individuals or an organization as a whole," says Joe DeSantis, manager of incident response at security consultancy SecureState.
If people don't configure their privacy settings very stringently, attackers can simply troll their pages to dig up information about the target and then hone a particularly effective spear-phishing email. Or attackers can pose as friends or family to "friend" a target -- or a friend of the target -- to gain that intelligence. They can also use a social networking connection to directly send targets malicious links on their walls or Twitter feeds.
"They may also seek to socially engineer as many people as possible," DeSantis says. "For instance, an attacker may create a Facebook application that shares profile information with the attacker or posts things such as malicious links to Facebook news feeds on behalf of the user without their knowledge or approval."
With so many possibilities available to criminals on social networking sites, users must arm themselves with information about how potential attacks work to sidestep the danger.
6. Watering Hole Attacks
It's easy these days for attackers to use exploit kits to break into legitimate sites and implant drive-by-download attacks. With "watering hole attacks" they're taking that technique further. The idea is that, just as a lion waits by a watering hole visited by the prey it would like to eat, an attacker plants malware at news or networking sites that he knows his targets are likely to visit. For example, employees of an accounting firm are likely to visit an accounting association website.
Sometimes attackers will wait patiently for months to spring their traps, says David Ulevitch, CEO of OpenDNS, a DNS and security service provider. "Criminals will conduct reconnaissance on their targets to gather information about their interests, devices and apps, and even physically survey their browsing habits at cafes or airports," he says. "If they don't succeed immediately, they will keep trying until they do, which may take months."
Organizations should not only encourage users to look for unusual pop-ups on sites they frequently visit, they should also practice good endpoint hygiene to keep watering hole attacks from hitting the mark.
The best way to counter this attack is by keeping antivirus software up to date and browsers patched, and "consider using browser protections such as NoScript, disabling Java and turning off PDF readers in the browser," says Michael Smith, CSIRT director for content delivery network provider Akamai Technologies.
7. Third-Party Web Apps
As more employees do work via third-party Web applications, criminals are having a heyday using these apps to compromise endpoints and enterprise networks. If policies for third-party apps aren't well-known and there are no controls in place to keep people from installing them within the corporate environment, companies can expect to find these apps in spades. Many people use Web apps in their personal lives, so they may not think twice about allowing a project management app to integrate with their Salesforce.com identities, says Tsahy Shapsa, co-founder of cloud security firm CloudLock.
"It may seem harmless, but attackers could -- and are -- taking advantage of users' tendency to authorize blindly by developing enticing apps and offering them for free," Shapsa says. "These apps can give attackers access to emails, files and contacts. They can even give attackers the ability to operate on behalf of the user."
In addition, existing cloud-based file-sharing and external collaboration applications can pose their own sets of problems.
"In the on-premises world, an attacker would send an email attachment containing malicious code. In the cloud, or in the case of Web-based apps, this attack would involve a file being shared inbound using a legitimate service like Dropbox, Box, Salesforce.com Chatter or Google Drive," Shapsa says. "That file can be made to look and feel like a corporate form asking for user's personal information, client information or something of that nature."
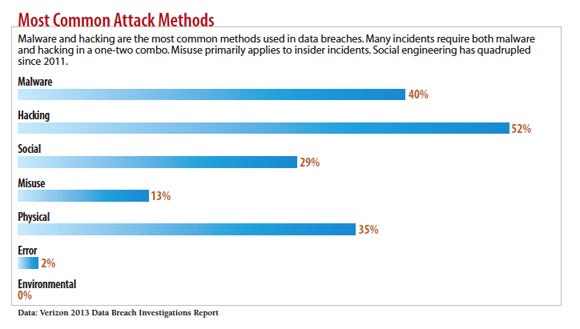
2013 Mobile vulnerabilities on the radar
8. Mobile Application Threats
As mobility extends the reach of third-party apps to users' smartphones and tablets, it also increases the risk that these Web-enabled applications will compromise corporate networks.
The use of enterprise mobile apps "blows away all the old models of enterprise security, including traditional firewalling, intrusion protection, and data loss prevention technologies," says Kevin Morgan, CTO of mobile app security vendor Arxan Technologies. The new risk comes from the "extreme variety of enterprise mobile applications being deployed."
Morgan says that mobile apps are frequently subject to direct attack by criminals who reverse engineer the applications, tamper with them and redistribute them to compromise devices. It isn't difficult for attackers to redistribute compromised applications that look legitimate on the Android marketplace, which tends not to vet or manage how code is signed. Similarly, attackers target jailbroken Apple phones through rogue marketplaces.
"This creates tremendous risk that individuals pick up applications that are tampered and repackaged versions of the original legitimate application, providing all the same functions -- but with unknown 'extras,' such as capturing and sending to a remote server login credentials, credit card numbers, or high-value and sensitive corporate information," Morgan says.
Users shouldn't be allowed to use jailbroken or rooted devices on the corporate network, and enterprises should consider some form of mobile application management to constrain application downloads, Morgan advises.
9. Malvertising
Online advertising that contains embedded malware or links to malicious websites, otherwise known as malvertising, is among the most common high-volume, Web-based attacks assaulting online machines today, according to researchers with OpenDNS.
"That's because hundreds of thousands of websites allow the same third-party network to put ads on their sites," says Ulevitch. So if one third-party network is compromised, it can affect thousands of sites.
In many cases, the malicious ads attack visitors without the site owners ever knowing there's a problem. Once attackers compromise the third-party network, they'll find a way to add malicious code to existing advertisements placed by a network provider to fill in banner ad spots. These sites could be legitimate news sites, blogs or any other ad-supported site.
When the user visits that legitimate site, the malicious code within the infected advertisement redirects the request for the ad content from the third party's queue of ads and requests content from a different Internet host that's serving up malware. Sometimes the malicious ad content can take advantage of browser vulnerabilities to automatically redirect to a malicious site or initiate a drive-by download. Other times the ad will entice users to click through some kind of lure -- perhaps a fake AV warning or a promise for a weight loss product -- and send them to a site hosting malware.
In addition to typical advice about maintaining strong endpoint security -- namely through frequent patching, updated antivirus, and effective configuration and vulnerability management -- network security precautions can help protect users as well, says Ulevitch.
"To protect against these types of attacks, enterprises need to block the DNS requests by domain name or IP address or by the subsequent IP-based connection," Ulevitch says. Security intelligence feeds may help block infection by pinpointing malicious IP addresses associated with current malvertising campaigns, he notes.
Users should be trained to avoid potential scams originating from banner ads, even from legitimate sites. They should be on guard for similar scams delivered through mobile apps. Many mobile apps are given away for free but supported by ad revenue. Most of those ads are delivered by third-party ad networks, and cyber crooks are increasingly attacking these networks, says Blue Coat's Larsen.
"As a recent example, an advertisement for a fake Angry Birds download delivered an SMS Trojan that [sent] premium SMS texts to the malware host, which then billed the unsuspecting users," Larsen reports.
10. P2P Dangers
Peer-to-peer networks have long been a hotbed of criminal activities, but as more legitimate networks such as Skype and Spotify gain mainstream acceptance, the bad guys are using them as platforms for malicious activity.
Researchers at Damballa, a provider of advanced threat protection, have seen a fivefold increase in malware using P2P for command-and-control instructions and data transfers in recent studies. P2P often gives attackers the power to bypass traditional network defenses.
"As the security industry starts to mitigate the risks from advanced malware by detecting communication 'up' to C&C, malware authors incorporate 'sideways' P2P communication so there is no one set of addresses that can be blocked," says Brian Foster, CTO for Damballa.
Even in organizations that have stamped out P2P activities on the corporate network, the threat may be introduced via mobile workers outside the network.
The less-reputable P2P networks continue to be bastions of malware distribution. Solera's Brandt recently did research on the less seemly "file indexing" directories set up for the sole purpose of delivering pirated software, many of which link to files stored in file drop services similar to the now-defunct Megaupload.
"On many attempts I found my browser endlessly loading pop-under ads while the file drop sites played countdown timers, demanded that I entered captchas and asked for other nonsense that serves no purpose other than to give the ads time to load," Brandt recalls. More than once, Brandt's test machine was infected simply by waiting for a download to begin. "Usually the culprit was a pop-under ad window, which itself contained a malicious iFrame reference to the hostile code," he says.
Protect Your Users From Web Threats
The starting point to protect against these many Web threats are basic endpoint protection measures, such as patching devices frequently, employing systematic configuration and vulnerability management practices, and keeping endpoints updated with antivirus software. Employees should be educated to understand the sophistication with which crooks design their attacks, often using familiarity, business urgency or plain curiosity as drivers.
But these recommendations are only a start. Some endpoints still fall through the cracks of even the best endpoint hygiene programs, and some employees still fall for well-crafted social engineering ploys. Criminals continue to employ attacks that take advantage of unknown, or zero-day, vulnerabilities. With so many potential points of leak or entry, additional layers of protection are essential, experts say. Some of these additional layers could be implemented by rethinking endpoint security, says Anup Ghosh, CEO of endpoint security vendor Invincea.
"Asking users to make security decisions and then blaming them when they make the wrong one isn't a solution to the problem," says Ghosh. Invincea advocates giving users the capability to browse within virtualized containers that would, in theory, buffer their actions on the Web from vulnerabilities in the browser or other applications on the device.
Other experts recommend backstopping endpoint protection with effective network intelligence to detect the kind of "sideways" movement that malware makes through the network after breaking in to a single endpoint.
"Building several different security zones, rather than one blanket solution, and monitoring them closely with daily forensic inspection and data analysis is the most effective strategy," says Vann Abernethy, senior product manager of distributed denial-of-service mitigation firm NSFocus.
Strategies may vary, but the key is to overlap them and to minimize chinks in the armor.
"Companies need to take a layered approach when dealing with these endpoint weaknesses," says Mark Lobel, principal in PricewaterhouseCoopers' security advisory practice. "It is impossible to stop an employee from ever being tricked, but companies can minimize the number of times -- through education -- and identify the impacts as quickly as possible through monitoring and alerting."
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




