Enterprises vastly underestimate the cyber risk from digital connections to vendors, suppliers, agencies, consultants -- and any company with which employees do business.
As more details emerge about the recent mega breach affecting CVS, Costco, Walmart, RiteAid, and Tesco, security experts are zeroing in on an often overlooked element in a company’s cyber defenses: its business partners.
The common thread between these companies is a third-party vendor called PNI Digital Media that provides photo processing websites and services for 19,000 retail locations. Similar to the massive 2013 Target breach in which hackers gained access to the company’s network via an unsecured heating and cooling vendor, it appears hackers leveraged trusted digital connections PNI had to these retailers to compromise their systems.
This recent data breach that began with PNI puts an often-neglected but ubiquitous area of exposure under the spotlight: the partner environment. Enterprises vastly underestimate risk from business partners, which can include vendors, suppliers, agencies, consultants, and any company with which employees do business. One common example is an airline that has a trusted digital connection to a company’s employee travel portal. While many companies perform in-depth analyses of their cybersecurity posture and harden their own internal systems against attack, the scale of connections to business partners and their risk is often unknown.
Consider the behavior of all your organization’s employees online, and then add to that surface area all of your company’s business partners. Even companies with the strictest security and data governance requirements deal with vendors who pay much less diligence to security. This is compounded by the ease of connecting to partners via cloud services.
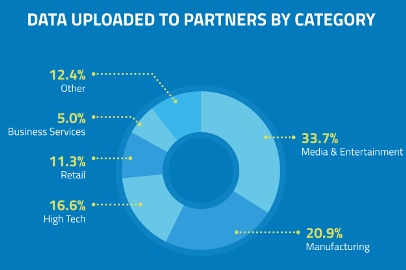
Skyhigh recently analyzed the partner ecosystem for 400 large enterprises. We identified the cloud as the hub by which modern businesses connect and exchange information. This shouldn’t be a surprise; when was the last time you used a fax machine? The sheer volume of connections, however, is astounding: The average enterprise connects to 1,586 partners via the cloud. This figure is a key data point validating the rapidly maturing cloud economy, but it also points to a vector of attack that many organizations today may not be equipped to defend against.
To quantify the risk of these connections, we found that 8% of partners were high-risk. This seemingly reassuring statistic is misleading. Companies sent a disproportionally large amount of data to high-risk partners, with this 8% minority receiving 29% of all shared data. The horror stories among this risky bunch are (almost) enough to make CISOs pull out the fax machine and the USB drive again. We found an partner airline that had 9,717 login credentials for sale on the darknet and 209 devices infected with malware; an advertising agency had 1,565 compromised identities for sale across 29 darknet sites. The risky partners include businesses that potentially deal with sensitive data. The provider of financial services technology had 1,216 compromised identities for sale on the darknet. All three of these businesses had websites still vulnerable to POODLE.
Certain types of partners are particularly dangerous liabilities for enterprises. The nature of PNI’s business highlights the value to hackers of a foothold within a B2B vendor’s network. Large enterprises dwarf PNI in organizational size and security infrastructure, but a breach at a B2B company can also affect its customers’ customers.
Analysis of enterprise cloud usage points to a trend of “super partners” – specifically 58 businesses that act as major cloud hubs. Companies in this tiny minority are extremely “popular” with each super partner connected to over 50% of enterprises. This means a breach within one of these companies could put a large number of enterprises at risk. Worse, the group is less secure than the general partner environment, as 12.5% of super partners are considered high-risk.
While many question the inherent security of the cloud, the risk from business partners shows how factors outside the security capabilities of cloud providers can impact the threat landscape for many organizations. In fact, much of the threat to data in the cloud can be attributed to the enterprise itself, through risky user behavior or insider threat. But what I consider the true security blindspot is the prospect of exfiltration of corporate data through unsanctioned cloud services or high-risk usage by employees of sanctioned, secure cloud services like Box and Office 365.
Cloud services enable thousands of organizations to share data and collaborate, revolutionizing the way we do work. A new way to work warrants a new security model. Expect a shift to data security as companies become aware of the extent of enterprise cloud adoption and the concomitant webs of cloud traffic.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




