Explaining risk can be difficult since CISOs and execs don’t speak the same language. The key is to tailor your message for the audience.
On March 7, a bipartisan bill was introduced to the Senate called the Cybersecurity Disclosure Act of 2017. The bill’s purpose is to “promote transparency in the oversight of cybersecurity risks at publicly traded companies.” It adds Securities and Exchange Commission (SEC) requirements for public companies to disclose what cybersecurity expertise is present within the board of directors.
If no expertise is present, then the company must disclose in its SEC report “what other cybersecurity steps” are being done by the board nominating committee. Whether this bill succeeds in becoming law or not, it is a shot across the bow to executives.
With all this going on, it’s likely that boards and executive leadership are going to be buttonholing their CISOs into cyber-risk conversations. Just a few years ago, security professionals struggled for executive interest (let alone support), but now we are in the hot seat for answers. And what a hot seat it is! A recent survey from Osterman Research reveals that 66% of fired IT professionals were terminated for reasons of security or compliance failures. That’s why we need to make sure leadership understands the relevant security issues and how to help mitigate them.
Explaining risk can be difficult since CISOs and execs don’t speak the same language. You need to tailor your message for your audience. We’ve talked about using operational risk to frame the conversation, but there is value in a straight-forward approach as well.
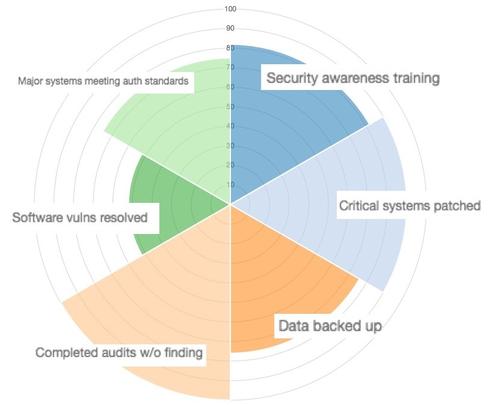
To do this, you focus on the top cyber risks and provide just the information the board needs to know. A good place to start is the state of company culture regarding security. You can produce metrics on alignment to desired security policy with numbers around security awareness training attendance, patching completeness, audit findings, vulnerabilities, incident counts, and backup coverage. You can even make a nice radar chart to show the percentages and quickly make the deficiencies apparent.
Beyond the overall status of the program, you need to explain cyber-risk. Keep it simple and remember this important nuance: many ordinary people don’t realize that risk has two components: likelihood and impact. For example, some people tend to react to catastrophic impacts (What are we doing about Pottsylvanian hacker-spies?) that are rare while overlooking more likely risks like ransomware.
It shouldn’t be hard for you find likelihood data. In addition to industry statistics and open source threat intelligence, you can gather information internally. Sources can include data used to create the radar chart above as well as firewall, intrusion detection, web and mail system logs.
Impacts are easier to talk about, but you need to explain the real potential impacts to your business. Talk in terms of tangible and intangible losses that resonate with them, including:
Tangible costs:
Breach disclosure costs (PII record count x disclosure cost/record)
Customer SLA fines
Revenue loss during system downtime and recovery
Compliance and audit fines
Potential litigation and fines down the road
Incident response costs, including internal resources (OpEx), third party breach experts, required remediation controls, and effectiveness testing
Intangible costs:
Impact to brand (the business puts a value to this—usually found as an asset line item in your financial books)
Current and future customer perception and loss
Loss of business value in acquisition discussions
Competitive advantage loss
The board’s personal reputation and/or job
When presenting likelihood and impact, stick to the simplified High/Med/Low model. Everyone is aware that there are more layers, and most execs would understand a more complex model, but their time is limited. In matters where the risk is high, they will probably press for details.
Lastly, you should never present a problem without a solution. Make sure you have a solid mitigation plan (with proposed budget numbers) to resolve anything rated high risk. Executives will also want clear lines of responsibility. They’ll want to know who’s responsible for remediation, and who is paying. The chances are likely the board has already dealt with high risk non-cybersecurity scenarios before. If you’ve done your job well in explaining, you can sit back and watch them decide. As you are the cybersecurity expert, you should still be prepared to give them guidance or validation.
This might seem like a lot of work but for effective CISOs, it is routine. Risk assessments and reporting with the board should be happening annually, at least. As cyber-risk is better understood and managed, you might need only to present updates if something significant or material happened. This is the ideal position—not only does it mean everyone is sleeping it at night, it means the board trusts you.
Get the latest application threat intelligence from F5 Labs.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




