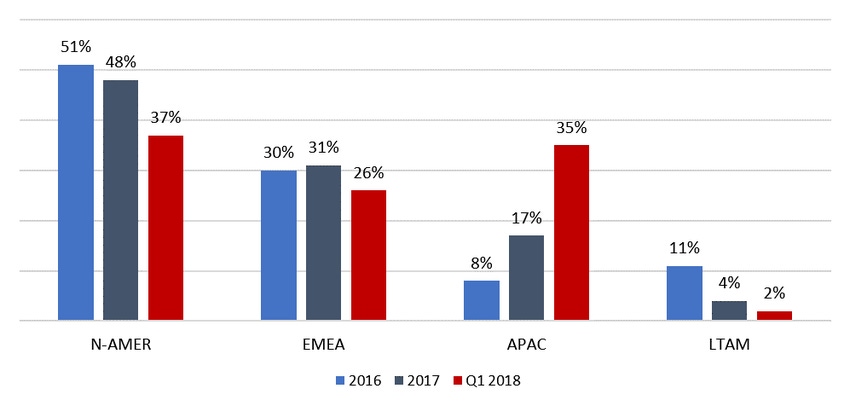
While North American targets have historically been on the receiving end of the majority of DDoS attacks since their inception, that trend changed in 2017.
lan Meller, Justin Shattuck, and Damien Rocha also contributed to this article
In case you haven't noticed, 2017 was somewhat of a milestone in the DDoS industry: it was absent a major world record-setting DDoS event. The bad news is that in 2018, DDoS attacks are slamming back in full force. The number of attacks mitigated globally by F5 from 2016 to 2017 increased by 26%. Q1 historically receives the lowest number of attacks. Based on F5's Q1 2018 attack count, the number of DDoS attacks will exceed 33% growth in 2018.
Taking Q1 2018 into account, the amount of DDoS attacks against targets in the Asia Pacific (APAC) region are increasing faster than any other region of the world. North America (N-AMER), Europe, the Middle East and North Africa (EMEA) have been steadily increasing year over year but did not see the same Q1 2018 growth as APAC.
North American targets have received the majority of DDoS attacks since their inception. This trend changed in 2017 when DDoS attacks targeting North America dropped below 50%, while EMEA-targeted DDoS attacks rose above a third, and APAC grew from 8% in 2016 to 17% in 2017. In Q1 2018, businesses in APAC received almost as many attacks as businesses in North America.
The Q1 2018 attacks are only one quarter in comparison to the annual averages of 2016 and 2017. If attacks against North America decline in Q2, as they have done the past 2 years, the trend of North America declining in overall percentage of attacks received will continue to drop. Attacks against EMEA entities increased in Q2 in 2016 and 2017, indicating there is a good chance EMEA’s percentage of the total will continue to rise, potentially surpassing North American targets for the first time.
Online gaming businesses were the top DDoS target in Q1 2018, followed by financial services and hosting providers. Collectively those industries received 76% of the DDoS attacks in Q1 2018. Web hosting providers and financial organizations have always been top DDoS attack targets, and that trend continued in 2017. Why? Because those two industries directly translate downtime into dollars lost. Therefore, blackmail DDoS attacks is a very lucrative for attacks as paying the ransom is an effective way to stop the pain.
The gap between the traditional top targets and other various industries including technology providers, ISP’s, online gaming, and business service providers is steadily closing. Every year we continue to see a broader scope of DDoS targets with the growth in DDoS-for-hire services at extremely affordable rates, and availability of DDoS tools to the common script kiddie.
DDoS Attacks by Type
UDP fragmented attacks are becoming increasingly popular with DDoS attackers that use multiple vectors in their attacks to “fill up the pipe” by maximizing the packets and fragments being sent through it.
When breaking down the DDoS attacks into volumetric, reflection, or application attack categories, volumetric attacks have always been the majority. Applications, as opposed to the traditional network, are a rising DDoS attack vector. Application attacks are more precise and require traffic scrubbing, versus the typical blocking of unwanted port traffic at the network layer. As the internet moves towards a virtualized application environment, we expect DDoS attacks targeting applications to take a larger slice of the pie in the future.
F5 has already mitigated multiple attacks greater than 250 Gbps in 2018. The interesting thing about these attacks is that it was clear the attackers had done their homework. They knew the prefixes they were targeting as they targeted multiple hosts in the same /24 subnet simultaneously, while constantly changing the target hosts. As mitigations were applied, the attackers continued to target other prefixes. In total, 3 different /24 subnets were targeted.
The top 10 source traffic countries remained the same throughout all attacks, which could indicate that the attacks were launched from the same systems over the four-day period. This type of attack behavior is consistent with IoT devices in which compromises and subsequent attacks go undetected or, in less likely scenarios, compromised systems owned by businesses (that don’t know they have been compromised) and are being used to launch attacks.
The largest source of the attacks came from the US, which is not typical. This is an indicator of a significant number of vulnerable systems (potentially compromised memcached systems or IoT devices) in the US being targeted to launch DDoS attacks from.
With the rise in IoT devices, cloud computing and online databases, more vulnerable systems are becoming available to attackers to launch devastating DDoS attacks than ever before. When defending against modern cyber threats, no business is immune to damaging DDoS attacks. If you cannot afford downtime, get a DDoS strategy in place now so you don’t have to scramble to put one in place while you’re under attack.
Get the latest application threat intelligence from F5 Labs.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




