I used to think the heyday of phishing had passed. But as Symantec notes in its 2014 Internet Security Threat Report, I was wrong!
Symantec just recently released its Internet Security Threat Report for 2014. It’s a review of 2013’s threats, a comparison with earlier years, and a look into the crystal ball for the current year with a nod to the direction of trends beyond that.
You can get your own copy here, but be warned that it’s 98 pages (in pdf format) and is not a quick read. Set aside a couple of days to fully digest it.
I wouldn’t think about trying to summarize it for you, there’s that much information. But I was taken with one section, which demonstrates how old, successful schemes can be recycled.
It’s the section on phishing. Now I’m old enough, and been around in the industry long enough (over 30 years now), that I still think of phishing as a recent addition to the criminal’s arsenal. But, as Symantec reminds us, phishing has been around since the early part of this century, easily 10 years or more. In terms of the threat landscape it’s definitely old-school. Or maybe the better term is tried-and-true. Symantec notes that the number of phishing attempts via email increased in 2013 over 2012, from one in 414.3 emails per day, to one in 392.4, a 5 percent increase.
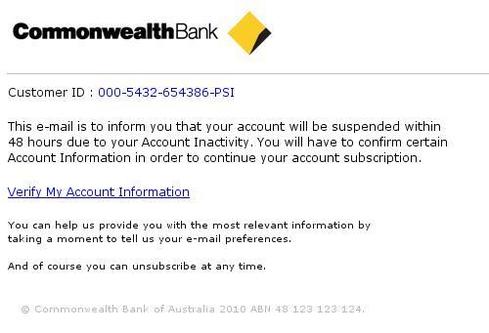
Traditionally -- and it feels odd to speak of “traditional” phishing -- the attack took the form of a notice from your bank, like this:
Clicking the link took you to a web page that looked remarkably like the bank’s own login page. Once you filled in the information requested, the bad guys had full access to your account, and usually more.
The saving grace for most people was that, usually, the bank identified in the email wasn’t one with which you had an account. And we quickly learned to “sandbox” any links in those emails by examining them, or typing the bank’s URL into our browser to see if it really had limited our access. I guess that’s why I’d thought the heyday of phishing had passed. But, as Symantec notes, I was wrong. They write:
Over time, phishing attacks have expanded in the scope of their targets from not only banks, credit unions and other financial institutions, to a variety of other organizations. The social engineering involved has also grown more sophisticated in recent years and recent examples include phishing for online accounts of customers of domestic energy companies and loyalty card programs. More energy utility companies are encouraging their customers to move to paperless billing, enabling an attacker to retrieve utility bills. They can potentially use these bills in the money laundering process such as in creating a bank account in someone else’s name and using the online bill as proof of identity.
This has sustained, and even increased, the amount of email phishing in the past year but probably the biggest growth factor, according to Symantec, is social networking:
Many of these phishing attempts consist of fake login pages for popular social networks. In addition to just spoofing login pages of legitimate sites, phishers began introducing baits relevant to current events to add flavor to the phishing pages. Celebrity promotions, popular community pages, social networking applications, and other related material were introduced into phishing sites as bait.
Just one example: A fake charity site for relief of some disaster (earthquake, tsunami, hurricane, fire, etc.) or “humanitarian” organization could easily harvest your bank or PayPal credentials in the name of giving a donation. And getting you to go to these fake sites and cough up your login details had the added benefit (to the criminals) of allowing them to push malware onto your computer, turning it into another bot on their network ready to push out hundreds of thousands more phishing emails. It just goes on and on.
What can you do? Educate users to not click on a link in an email. Even better, see if your email server software will allow you to disable links in the emails (and turn them into text URLs). And remember to tell them that very few English majors send phishing emails -- if the grammar is bad, then the purpose is bad. And you can take that to the bank.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




