
Enterprise cybersecurity technology research that connects the dots.
Organizations looking to get ahead in cloud security have gone down the path of deploying CSPM tooling with good results. Still, there’s a clear picture that data security and security operations are next key areas of interest.

As an industry, we're now at a point where we don't have to convince anyone that we have a massive digital dependence on cloud technologies and that securing cloud deployments is a key initiative for most organizations. There is widespread availability of cloud security posture management (CSPM) tooling — commercial- and community-driven alike — and CSPM itself is being incorporated into new tooling coming under the heading of cloud-native application protection platforms (CNAPP).
Many cloud security conversations focus primarily on making sure clouds are configured properly, but there is much more to cloud security than that. Much like traditional security is much more than patching, there is more to cloud security than configuration.
As we analyze cloud security trends, we recently collected survey data under our Omdia Decision Makers survey and found interesting results that highlight these conclusions.
The figure below plots responses to the question "What are your top concerns in relation to cloud security?" The bars on the left show the aggregate view (n=186). We can clearly see a major concern with cost of security tooling, then other concerns aggregated together, including security tooling functionality, responding to events, data security, and others.
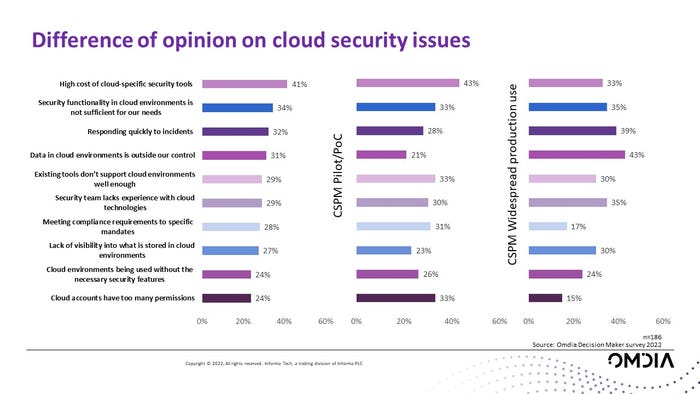
That said, we also segmented the population into two groups based on their response to a previous question about how advanced their deployments of CSPM tools were. Our ongoing industry interactions with multiple stakeholders point to CSPM tools as the type of tool most often associated with "cloud security" conversations, so we chose CSPM deployment experience as a proxy for cloud experience. Statistician George Box is famous for saying "all models are wrong, but some are useful," which we think is relevant here; there's no implication of causation, but some interesting variations show up in the response data.
For those that have what we consider "low" experience with cloud security (n=61) by virtue of having CSPM deployments in the pilot or proof-of-concept stage, concerns around cost are even more pronounced, as are concerns about cloud permissions and a slight bump for concerns about compliance.
For those that have more cloud security experience (n=54) — those that responded that they have deployed CSPM in widespread production use —responses shifted significantly. Now, concerns about data security are much more pronounced, as are concerns about how to respond quickly to incidents, with additional notable concerns regarding the ever-present skills gap in terms of cloud technologies.
Heightened Concerns
Our interpretation of this data is that customers are indeed seeing value from the CSPM tooling for configurations and compliance, but they now have heightened concerns on data security, security operations, and making sure their teams are skilled in cloud technologies. These concerns are already lurking in the shadows, and once CSPM clears the way of handling the more visible security configuration/compliance concerns, these issues come to the forefront.
The responses uncovered here point to interesting directions for future inquiry. It is increasingly clear that data security presents a key area of concern. What are the ways one gets to data? One way is via direct access to the data stores themselves. This is the provenance of cloud configuration (CSPM) and the increasingly popular DSPM (data security posture management) category. Another is getting access via the very APIs provided by the company; this then leads down a path of paying close attention to API security.
For security operations, the path forward appears to include more considerations about how to incorporate cloud security use cases in SOC response flows. Dubbed cloud detection and response (CDR), this is also a promising area of research that we're watching.
For end users, this means being ready to address these categories soon. For vendors, understand that there is much more to customer demand for cloud security than CSPM — or even CNAPP — alone.
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

