
Enterprise cybersecurity technology research that connects the dots.
With more staff working remotely, privileged access management (or PAM) has never been more important. Market forecasts, drivers, and trends are explored.
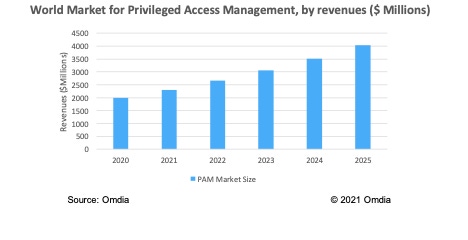
During the pandemic of 2020, a market that performed particularly well was the privileged access management, or PAM, market. With more staff working remotely, PAM has never been more important. In 2020, revenue in the PAM market increased to nearly $2.0 billion. This equals an annual growth rate of around 17% from the previous year. This is an impressive figure, considering the economic and business uncertainty over the last year or so.
Mergers and Acquisitions in This Space: Centrify and Thycotic
In March 2021, private equity firm TPG Capital acquired PAM vendor Thycotic for $1.4 billion. It plans to merge it with Centrify, the other PAM vendor it acquired two months earlier. Centrify will thereby hope to present a serious challenge to PAM market leader CyberArk. PAM technology came into existence around the turn of the millennium to address the growing need for control of privileged access in networked environments.
Its importance has only increased since then, with the sudden expansion in remote working caused by the COVID-19 pandemic and the concomitant boost to cloud adoption combining to make it even more vital to monitor and control privileged access.
Big Guns Like Okta Entering the PAM Space
In April 2021, Okta, a leading vendor in identity-as-a-service (IDaaS) announced its entry into the privileged access management market. A battle royale awaits Okta in PAM, however, for there it will be going up against the clear market leader, CyberArk. The 800-pound gorilla in its own segment, CyberArk has kept a keen eye on Okta's evolution in recent years, including its 2017 acquisition of Stormpath, a provider of user management services aimed at the developer community, delivering the ability for companies to monitor and control their developers' access to application code in the development pipeline and in production. The Stormpath service was then folded into Okta's broader portfolio.
This is also an area that CyberArk sees as a natural extension for PAM, so the entry of a competitor with the heft of Okta was clearly a significant development. Indeed, some industry pundits see CyberArk's acquisition of IDaaS provider Idaptive in May last year as a move prompted at least in part by Okta's encroachment into the developer access space. Now Okta is entering CyberArk's core PAM market, putting the cat even more firmly among the pigeons.
Cloud Permissions Management (CPM) Adds to the Mix
An adjacent segment that may help to grow the PAM market is cloud permissions management (CPM). CPM is technology that discovers all the extant access entitlements within a company's cloud infrastructure, makes recommendations on how they might be reined in, in line with zero-trust security principles, and, where appropriate, automatically takes the curtailment action. CPM aims to address the problem of "permission sprawl," whereby users such as developers, administrators, service accounts, and application permissions accumulate excessive access rights to a company’s applications and workloads in the cloud, often by indirect means, such as simply belonging to a particular workgroup.
CPM is a market segment at a very early stage in its development. This sector initially was made up of small startups, including Cloudknox, Sonrai, Ermetic, and Solvo. This is typical of newly emerging areas of security technology that embody a different approach to a specific problem. However, toward the end of 2020, two much larger tech industry players — namely, Salesforce and CyberArk — launched CPM capabilities within their portfolios. Furthermore, in April 2021, Zscaler became the first major player in cybersecurity to buy a specialist vendor in the emerging market segment of CPM with its acquisition of Israeli CPM startup Trustdome.
Conclusions
The PAM market has a bright future due to remote working, an increase in mergers and acquisitions activity, large players entering this segment, and adjacent segments such as CPM showing good growth potential. The PAM market is projected to show good growth during the next five years, reaching $4.0 billion in 2025 (a CAGR of 15.2%).
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

