
Enterprise cybersecurity technology research that connects the dots.
The Cyber Kill Chain and MITRE ATT&CK are popular reference frameworks to analyze breaches, but amid the rise of XDR, we may need a new one.
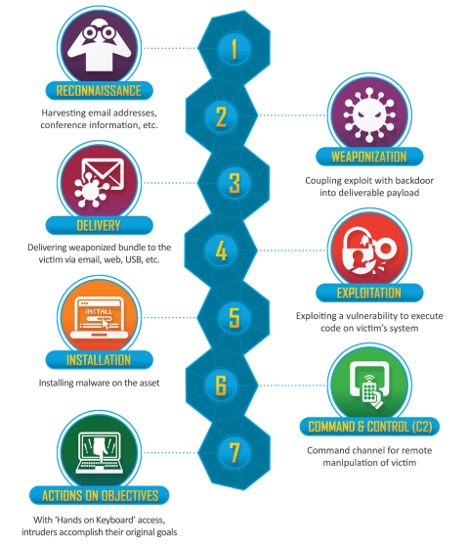
If you work in information security, you will be aware of Lockheed Martin's Cyber Kill Chain and/or the MITRE ATT&CK Framework. Both are attempts to create a common language in which to describe the various stages of an attack, and the tactics utilized by the attackers.
These frameworks were created at a time when it was becoming clear that preventive cybersecurity was no longer viable: Defenders were being forced — by the sheer volume, variety, and speed of new threats — to adopt a "detect and respond" approach, a stance sometimes referred to as "assume the breach."
A Lingua Franca for Discussing Threats and Sharing Intel
The benefits of a framework in this context are clear. Detecting and responding in a timely fashion can be enhanced by sharing threat intelligence, describing an attacker's modus operandi, as well as techniques and tactics that could be used against them.
It's no coincidence that the earlier of the two codification efforts, the Cyber Kill Chain, was created by a defense industry heavyweight and adopts the military parlance used against real-world adversaries in combat.
Lockheed introduced its model for defending customers' IT infrastructure in 2011, describing seven phases of an intrusion, as shown in the diagram below:
The MITRE Corporation is a nonprofit that supports US government agencies in its cybersecurity activities. It is the curator of the widely used Common Vulnerabilities and Exposures (CVE) database.
It began developing ATT&CK (which stands for Adversarial Tactics, Techniques, and Common Knowledge) in 2013, officially releasing the framework in May 2015, with several updates since then.
In the following diagram, on the right are the 11 tactic categories (plus Impact, which is clearly not a tactic but rather a result). MITRE says these categories are derived "from the later stages (exploit, control, maintain, and execute)" of the Cyber Kill Chain, and are designed to provide "a deeper level of granularity in describing what can occur during an intrusion."

Figure 2: ATT&CK for Enterprise . Source: The MITRE Corporation
These frameworks help practitioners in security operations centers (SOCs) investigate threats, exploits, and breaches, and share information with their peers to do so. Framework adoption among enterprises is driven by the usefulness of having a common language to describe what attackers were doing, and in turn more quickly figure out how to stop and prevent those attacks.
Tech vendors also map their products to the stages of a framework, showing how they can help customers address the challenges of detecting and responding to threats.
Perceived Shortcomings of the Frameworks
Omdia has observed vendor mapping to the Cyber Kill Chain taking place through the mid-2010s. More recently, there has been a shift away from the Cyber Kill Chain model, with more companies instead adopting the ATT&CK Framework.
This may be on account of MITRE ATT&CK's nonlinearity, making it more appropriate for red- and blue-teaming: Attackers and defenders can utilize and describe any number of tactics, techniques, and procedures (TTPs) in any order, since genuine threat actors often change their approaches.
Another criticism of the Cyber Kill Chain has been that it does not help to model insider threats, as its initial stages happen outside the corporate infrastructure.
A further issue is that it is more malware-centric: Assume the attacker will find a target, get in, and run malware to achieve an objective. Because introducing malware is difficult to do without triggering an alert, modern attackers instead try to remain as stealthy as possible, launching fileless exploits or leveraging everyday admin tools like PowerShell (the so-called "living-off-the-land" approach). It gets harder to express such attacks with the Cyber Kill Chain.
MITRE ATT&CK, by contrast, is a more modern approach focused on TTPs. It seeks to classify attackers' goals, tasks, and steps; as such, it is a much more comprehensive approach to modeling an attack.
That said, MITRE ATT&CK also has its shortcomings, notably when a security team is using an XDR platform. In an automated detection scenario, defenders might see the symptoms without knowing the exact root cause, such as suspicious user behavior, and such scenarios are harder to fit into MITRE ATT&CK.
A Framework for XDR?
Stellar Cyber, a developer of XDR technology (a detection and response platform designed to discover and correlate threats across endpoint, network, and cloud), argues for the creation of a new framework. It envisions an XDR framework/kill chain leveraging MITRE ATT&CK on the known root causes and attackers' goals but going further regarding other data sources, such as anomalous user behavior.
There is precedent for an individual vendor feeling a need to extend or amend frameworks. FireEye came up with its own version of the kill chain, which put more emphasis on attackers' ability to persist threats, while endpoint detection and response (EDR) heavyweight CrowdStrike uses MITRE ATT&CK extensively but provides a set of nonstandard categories to cover a broader range of scenarios.
Equally, recent years have seen the emergence of something called the Unified Kill Chain (UKC). First proposed by Paul Pols from the Netherlands' Cyber Security Academy in 2017, the UKC combines elements of both the leading frameworks and presenting no fewer than 18 distinct attack phases, which researchers came up with in an attempt to address the perceived shortcomings of both the Lockheed Martin and MITRE models.

Figure 3: The Unified Kill Chain
As the threat landscape evolves, so too must cybersecurity. Attackers' erstwhile reliance on malware (i.e., malicious code) to perpetrate their misdeeds has given way to new techniques. One in particular, so-called fileless malware, leverages legitimate software such as PowerShell, to leave no trace of its actions and hence is more difficult to detect. A framework formulated when malware reigned supreme clearly requires adjustment for the new world of fileless attacks, and Omdia anticipates many other future attack types will necessitate further framework refinements.
Omdia understands Stellar Cyber's desire for a framework that is more appropriate for XDR and looks forward to seeing it when the vendor unveils its proposal for one. However, a proliferation of attack-description frameworks may ultimately defeat the objective that brought them into existence in the first place — i.e. the creation of a common language in which to discuss threats, exploits, and breaches.
In this context, the Tower of Babel remains a cautionary tale.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

