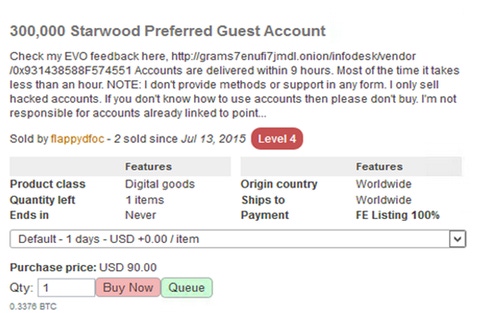
In the month of July alone, hundreds of hospitality-related goods and services were offered for sale on the Dark Web including big names like Wyndham, Marriott, Hilton and Starwood.
Plagued by pervasive cyber defense immaturity and a baffling lack of urgency around prioritizing cyber and data security concerns, the hospitality sector -- Orbitz, Expedia, Trivago, Kayak, Hotwire, Hotels.com, Groupon -- among others across both big and small chains, is low-hanging fruit for traditional cybercrimes.
Add to this the threats coming from the near total blind spot, the Dark Web, and you’ve got a recipe for real problems that hit home with hospitality’s most essential element: paying customers.
While this all may sound a little unbelievable to consumers, it’s de rigeur in the Internet’s black market, The Dark Web, traditionally thought of as a busy place for illegal drugs, ill-gotten prescription pharmaceuticals, pornography, and politically subversive activities -- the haven of hacktivists and criminals, drug addicts, and sexual deviants.
For those like myself who study the Dark Web and collect its data, it’s a lot more than this - and it’s evolving quickly.
In any given week on the Dark Web, you can find all manner of things offered for sale or trade that affect a hospitality company’s cyber strategy, their tactical defenses and much more. More importantly, the things regularly offered for sale have real impact on the bottom line: financials, reputation, customer loyalty, and brand -- things that can lead to millions in real dollars being lost or stolen, erosion of customer confidence, litigation costs, and theft of intellectual property or trade secrets.
How serious are the effects? In August, the Federal Trade Commission won a monumental legal victory over Wyndham Worldwide Corporation, one of the biggest players in hospitality. The upshot of the case means that companies can now be held responsible for poor security practices that lead to a data breach.
Here are a few samples of hospitality-related items that can be found on the Dark Web on any given day:
Sensitive customer data and corporate documents
Access points inside networks, web, and mobile applications
Hijacked loyalty program accounts from unsuspecting customers
Fraudulent membership points/balances/voucher codes
Hotel network/Wi-fi exploits
Software vulnerabilities for common hotel point-of-sale systems
Phishing campaigns aimed at major chain customer bases
Fraudulent websites designed to lure hotel customers
Crimeware instruction in “how to” do fraud
All of the above for hire/as-a-service
In the month of July alone, there were hundreds of hospitality-related goods and services for sale. Big names like Wyndham, Marriott, Hilton, Starwood as well as smaller regional, budget, and boutique properties.
Why hospitality is such a big target
To cybercriminals, hotels, motels, casinos, resorts, and their ancillary support businesses are like an eternal spring. There are hundreds of millions of customers staying and paying at any given moment. Hospitality is also one of the largest adopters of technology in the business world. Web and mobile apps abound as does the data they trade in. That means networks and accounts and data are everywhere, from Wifi to point-of-sale.
All these moving parts means the threats are infinitely long. When you take the volume and variety into account that means functions like cyber defense and fraud prevention are even harder to do effectively (or at all in some cases).
Much like companies in other sectors, hospitality acquires and implements cybersecurity in a mostly traditional way. They look at what others are buying, who they’re hiring and then do the same. Firewalls, IDS/IPS, SIEM and all the traditional “defense-in-depth” approaches are common.
The problem with hospitality, like others in less frenetic industry sectors, is that these defense strategies aren’t effective against a multi-dimensional and constantly evolving threat landscape. In fact, due to hospitality’s unique data and volume issues, as well as its inherent need to stay competitive via customer conveniences and volume-driven cost controls, traditional cyber practices are a kind of Maginot Line of defense: they seem real and big enough, but in reality, they are superficial and easily circumnavigated.
Across the sector, the big and the small companies suffer from myriad challenges:
Only the top 1% of sector companies possess adequately mature cybersecurity functions
Customers, customers, and more customers
Veritable worlds of data in motion and at rest
Technology everywhere
Very little use of big data analytics
Understaffed, overworked and no real budget
Prioritization of customer conveniences over security
Threat “tunnel vision;” watching the front doors, back doors wide open
Little-to-no comprehensive cyber intelligence to inform defense tactics
No dynamic mapping of risk profiles to cyber threats
Insignificant cybersecurity budgets vs. the size of the threat
It’s a recipe for disaster even without the “out of the blue” threats posed by the Dark Web. And just as with the real Maginot Line in World War II, the Dark Web represents a set of threats that are largely unexpected, with unforeseen tactics coming from all the least expected angles.
Why the Dark Web is such a significant threat

Trending Dark Web cybercrime effects in the hospitality sector, last 90 Days Image Source: SurfWatch Labs Analytics
Most companies traditionally prioritize tactical cyber defenses above all else and ignore any kind of formal intelligence gathering. That’s like spending all your defense budget building a big wall around your fort not knowing your enemy has airplanes or tunneling machines too.
This is particularly true in the case of Dark Web threats. Since most companies don’t gather or use intelligence even against “traditional” cyber threats like malware and viruses, Dark Web threats like insider access being monetized for further attack and exploit are all but invisible.
Dark Web threats can also be considered “active.” It’s one thing to know about a certain kind of malware on the rise against your industry, but another to know someone’s selling access to customer credit card data being harvested from a point-of-sale terminal inside a specific resort. IT can investigate the possible presence of malware, but it can't immediately act on the point-of-sale issue and fix the hole.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




