While IT security pros may still find themselves defending their roles, they're also in a good spot when it comes to compensation, with a median base salary bump for staffs up a tidy $7,000 this year, according to the new The InformationWeek 2012 U.S. IT Salary Survey: Security
March 30, 2012

See the entire report on InformationWeek Reports
The 2012 InformationWeek Salary Survey shows that security is one of the hottest sectors of the IT job market. But discussions with IT security pros suggest that they are, for the most part, considered a necessary evil by the rest of their organizations.
Even with the harsh glare of high-profile data breaches--recently intensified by the Anonymous hacktivist collective--IT security professionals often find themselves having to defend their group's mandate of defending the organization. Their efforts are often construed as a disruption to business operations, rather than a strategic element. "I feel like Don Quixote sometimes," says a senior information security analyst with a community college district. "There's lots of cooperation and collaboration with IT, but [some in the organization] think I'm a pain."
He says the vulnerability assessment and penetration testing he does to check for security holes are seen as disruptive to operations, and he's often restricted to running these tests on holidays. "I get flak for pointing out they have a problem," he says.
In one case, for example, he was chastised when an unpatched and misconfigured device knocked several switches offline during a vulnerability assessment. "The reality was that the switch was not patched, and it was vulnerable because it was misconfigured," he says.
Even with the issues IT security pros sometimes endure in-house, this year's numbers again show they are in a good spot when it comes to salary and overall compensation. IT security specialists command higher salaries than general IT security professionals, and they feel better overall about their job security than others, according to our InformationWeek 2012 U.S. IT Salary Survey.
Even so, only half of the security pros who responded to the survey said security has "crucial" status across all levels of manage- ment, with 31% saying it's crucial in some business areas of the organization.
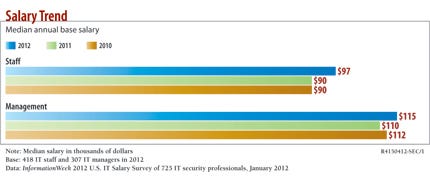
The median base salary for IT security pros rose in 2012. The median base salary for security staffers was $97,000 this year, up from $90,000 in 2011; the median base salary for managers was $115,000 in 2012, up from $110,000 the year before. That's higher than the overall IT median salary of $85,000 for staffers and $108,000 for managers, according to this year's report.
Overall compensation--salary plus bonuses and other cash payments--put the IT security staffer's median overall salary at $103,000, up from $97,000 the year before, and the IT security manager's median overall compensation at $127,000, up from $122,000. That's also higher than the overall median IT compensation of $90,000 for staffers and $116,000 for managers, according to the survey data.
IT security requires a different mind-set than other IT careers, and it can be both stressful and rewarding, says Todd Ryan, IT architect for mobility and information security at electronic design automation firm Cadence Design Systems. "You are generally viewed as paranoid and not an enabler of new technology, when the truth is we are trusted with protecting the organization--and that comes with great responsibility," Ryan says. "An attacker only needs to be lucky one time to be considered a success; a security professional may protect the organization for years, and if an attacker breaches the company one time, you may be viewed as a failure. That being said, I think the role is highly rewarding from a compensation and job satisfaction perspective."
Security jobs are hot for several reasons, starting with stringent compliance regulations and increasing concerns over protecting sensitive customer and corporate information. There also is a shortage of talent in the IT security area, which puts those with skills and experience in high demand. Several security pros who participated in the survey say they regularly get offers for positions in other organizations. "I think that, overall, the IT security field is white-hot from a recruiting and need perspective for employers," Ryan says.
We don't expect this demand for security talent to decrease any time soon, especially given the consumerization of IT and the security issues that come along with the bringyour- own-device model, several cybersecurity legislative efforts under way, increasing threats from cyber espionage adversaries gunning for intellectual property, and groups such as Anonymous that are posing a very visible threat.
Most IT security staff who responded to the survey have a high degree of job security and satisfaction with their positions. Half say they feel "very secure" in their jobs, 42% say they feel "somewhat secure" and only 8% say they feel "insecure" about their positions. That's a higher percentage of job security than among IT staffers overall, where 40% of all IT staffers feel "very secure" about their jobs, 48% are "somewhat secure" and 12% are "insecure."
The story is similar when comparing IT security managers with IT managers overall. Some 44% of security managers feel very secure, 49% feel somewhat secure and 7% feel insecure. While 46% of overall IT managers feel very secure about their jobs, 45% feel somewhat secure and 9% feel insecure.
Despite the way others in the organization perceive them, security pros seem slightly happier at work than other IT pros. "I have a great job," says a cybersecurity coordinator with a utility company. "Soon it may become more hectic and stressful, but for now, it's great."
According to the survey, 55% of IT security managers say they are satisfied with all aspects of their jobs, while 16% are very satisfied. Some 23% are neutral about their jobs, while 5% are dissatisfied. The numbers are similar for IT security staff, with 47% saying they're satisfied, 19% saying they are very satisfied, 24% saying they feel neutral and 8% saying they feel dissatisfied. By contrast, 49% of overall IT managers say they feel satisfied with their jobs, 18% feel very satisfied, 21% feel neutral and 10% feel dissatisfied. For overall IT staffers, 46% feel satisfied, 16% feel very satisfied, 24% feel neutral and 12% say they feel dissatisfied.
Gender Gap Prevails
Women are still the minority in security, and they tend to draw lower salaries. Of the security- focused respondents to our survey, 12% of staffers and 9% of managers are female. The numbers aren't much higher overall in IT, with women representing 13% of staff and 12% of IT management respondents.
Men still make more, but it appears that women's salaries may be gradually catching up. In security, female staffers drew a median base salary of $95,000, up from $87,000 last year. Their male counterparts made $97,000 this year, compared with $90,000 last year. Female security managers' median base salary was $110,000, up from $108,000 last year, and male security managers' base salary was $115,000, up from $110,000.
A female corporate security manager says the salary gap is actually quite small given how far women have come in the business world in such a short time. "I don't think we have the confidence to ask for what we want," she says. "Women are often uncomfortable asking for salary raises. Men are better at that."
Elise Murphy, security administrator at Loyola University Chicago, says she's hopeful that salaries are gender-blind, but she also speculated on whether part of the shortfall is due to bargaining skills. "I hope that salaries are becoming more based off performance and experience than gender," Murphy says. "However, I wonder if maybe men are just better at salary negotiations."
One of the most hotly debated topics in the IT security field is the relevance of certifica-tions. The data in this year's survey again show that security certifications are in demand and that those who hold them tend to get paid more. Nearly 70% of the IT security staffers in the survey hold some type of security certification, such as CISSP (Certified Information Systems Security Professional), CISA (Certified Information Systems Auditor), or CISM (Certified Information Security Manager). Seventyseven percent of managers hold at least one security certification.
In terms of pay, staffers with security certifications command a median base salary of $99,000 and total compensation of $104,000, compared with $93,000 and $100,000, respectively, for staffers who don't get certified. The management level is similar, with certified managers earning a median base salary of $119,000 and a total compensation package of $132,000, compared with uncertified managers, who have a median base salary of $105,000 and a median total compensation of $120,000.

"Certifications definitely still benefit people in terms of salary, even though the skills they are teaching are not directly applicable, and there isn't always a one-to-one correspondence," says a security manager who holds a CISSP. "It's sort of a good indication that someone has the basics down and is motivated to get that cert. ... All else being equal [with job applicants], I'll take the one with the cert."
Loyola's Murphy says certifications are "very, very important" for management-level positions. "It seems that many employers won't even look at your résumé without at least one certification," she says. "I am currently working on my EnCE [EnCase Certified Examiner– Forensics] because we have to have a forensic- certified member on staff." She adds that she also will soon be working on a Global Information Assurance Certification.
Cadence's Ryan, who holds CISSP, CompTIA Security+ and CCSA certifications, says that not only do many jobs require certifications, but that accreditation also garners respect. "Certifications are a key in the security field," he says. "Many jobs actually require certain certifications, and certain certifications give you respect in the industry due to the level of knowledge and commitment required to obtain them."
Security pros are split on whether their career paths and salary advancements are as promising as they were five years ago. Among staffers, 48% say they're not as promising, while 42% say they are and 10% aren't sure. Managers are a bit more optimistic, with 48% saying they're as promising as they were five years ago and 47% saying they're not. About 5% are unsure.
Kevin Fred, a senior information security consultant, says the security field has a more promising outlook than other IT specialties. "The future looks better for security folks than in other aspects of IT," says Fred, who notes that he's expressing his opinion and not that of his employer. He says it's only a matter of time before a big cyber attack hits the United States, which will put information security front and center. "I think that when this happens, there's going to be a massive shift in the realization of the [general public] in what this information security world means," he says.
Which leads us to the one very surprising finding from the survey: Only 13% of the IT security pro respondents say their organizations were hit by a serious data breach or compromise in the past 12 months.
This number does not align with many other studies, which show that a majority of organizations have been hit. So why the discrepancy? It's unclear if the word "serious" narrowed the affirmative answers, but some security pros say organizations may not know they've been hit. "As more companies put in more infosec controls to prevent this--DLP [data leakage prevention] plays a big part here--they will start to see what is really happening that they didn't know before. Then there will be more reportable incidents," says the female corporate security manager.
SYNOPSIS:
Survey Name: InformationWeek 2012 U.S. IT Salary Survey: Security
Survey Date January 2012
Region United States
Number of Respondents 725 IT security professionals in 2012, including 418 IT staff and 307 IT managers.
Purpose To track IT salary and compensation trends from the perspective of those on the front lines, InformationWeek conducts an annual U.S. IT Salary Survey. Now in its 15th year, it's the largest employeebased IT salary survey in the country. Last year, 18,201 full-time IT professionals completed the Web-based survey. This year, 13,880 took part. The goal of this study is to measure various aspects of compensation, benefits, and job satisfaction. This report focuses on the 725 IT security professionals who participated in the survey.
Methodology The survey was designed by InformationWeek and fielded online. The survey was promoted in InformationWeek's daily and weekly newsletters. In addition, email invitations with an embedded link to the survey were sent to qualified IT professionals from InformationWeek Business Technology Network print, newsletter and events databases. The survey was fielded from November 2011 to January 2012.
The information in this report is based on responses from 725 IT security professionals. Unemployed and part-time workers were excluded from these results, as were respondents from outside the United States. This report uses median rather than mean or average figures for salary and percentage salary changes to eliminate distortions caused by extremes at the high or low ends of the responses.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


