Bells and whistles are great, but you can stay safer by focusing on correct configurations, posture management, visibility, and patching.
Here's the scenario: A state-sponsored attacker uses a zero day to breach the environment. This foothold lets him run previously unknown, fileless attacks originating from an exploited process. Fortunately, his evil plan is foiled by our next-generation, AI-powered security tool that detected and prevented it in nanoseconds!
While silver bullets shine brightly, unfortunately, they work mostly against werewolves, not real-life cybersecurity incidents.
I spent a decade in intelligence with Unit 8200 of the Israel Defense Forces (IDF), considered one of the most elite cybersecurity offensive units in the world. After the military, I spent another decade at Check Point Software Technologies, one of the largest pure-play security vendors.
The most important cyber defense lesson I learned in the IDF and at Check Point is that security basics are always more important than shiny new security toys. Why? Because at the end of the day, it doesn't matter how sexy your “next-gen, real-time enforcement cyber death ray” is — attackers will always take the simplest path to breach your cyber defenses.
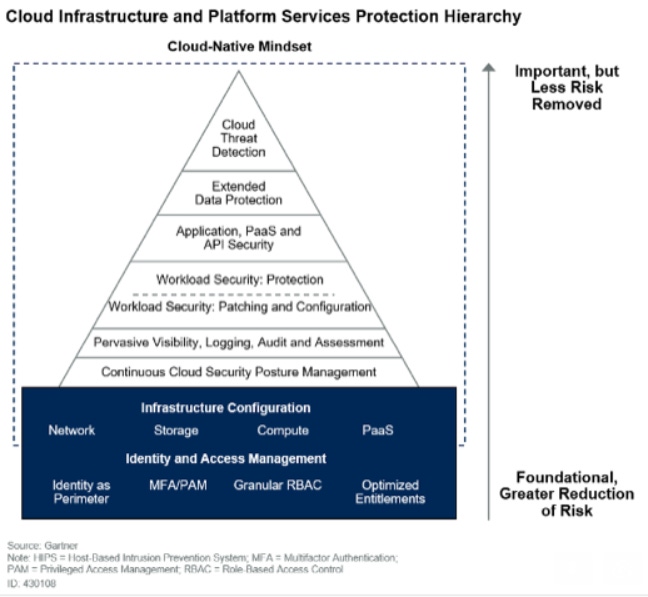
I'm not the only one to have this belief. Security basics are often listed as fundamentals in anyone's cybersecurity pyramid, as illustrated by Gartner's cloud security report visual below.
This fundamentals-first strategy is no surprise to experienced practitioners. Having the correct infrastructure configuration, effective posture management, full visibility to the environment, and patching and configuring are all at the base of the pyramid. Meanwhile, advanced threat detection tools are at the top of the pyramid, indicating that they're Important, but remove less risk. Simply put, good IT hygiene dramatically reduces risk more than quasi-advanced silver-bullet solutions.
Consider these three examples to illustrate why.
Multifactor Authentication (MFA) Versus Artificial Intelligence (AI)
Some vendors preach that they use capable heuristics and AI to detect anomalies and account takeover rather than real user behavior. At the end of the day, all of this AI is based on some basic features: time, geolocation, superhuman anomalies (someone who simultaneously logs in from two or more locations), and similar such measures.
The reality is that machine learning is not a crystal ball. If your users leverage passwords without MFA, such advertised heuristics put them on very shaky ground.
My grandma, who was 90+ years old, knew how to use a VPN to watch streaming episodes not available at her location. Do you really expect an attacker not to look at your user location (readily available on Facebook) and use a VPN to access it from the same place? Because of this threat, a practitioner who deploys MFA can sleep better at night.
Patching vs. IPSes
Intrusion prevention systems (IPSes) function by intercepting traffic, matching it against attack traffic, and blocking the bad traffic while allowing good traffic to pass. This might be so effective that why should we even bother to patch?
In real life, a vulnerability is a bug, which is exploitable in numerous ways. Some exploitation methods appear all too similar to legitimate requests. Meanwhile, IPSes need to distinguish between legitimate and malicious requests within milliseconds. You must maintain a balance between false positives, false negatives, and performance because you can't win all three.
In many cases, this harsh truth means that vendors end up having the sign of a specific attack, and not the vulnerability itself, which means that the attackers can slightly change the code and sneak in. The practitioner who patched the environment shouldn't need to worry about this happening.
Detecting Lateral Movement Risk vs. Actual Lateral Movement
The most common way to perform lateral movement is to reuse privileges in the assets that attackers have a foothold on, such as secrets and credentials stored on breached machines. Vendors will preach that they can distinguish between legitimate traffic and lateral movements — to even automatically block such illicit activity. They'll use terms like machine learning and AI to make their product sound advanced, but these capabilities are very limited.
The product may block well-known malware that performs the exact same sequence in any invocation and hence was "signed" by them — making such products glorified, network-based, signature-matching systems. But because AI and machine learning are based on training, they aren't able to distinguish between legitimate traffic and lateral movement with an accuracy that fully supports runtime prevention.
Moreover, no one knows how these applications work in all scenarios. Are you willing to block traffic just because it hasn't been seen before? Or what about an edge case in the app it's never seen?
On the other hand, managing lateral movement risk is definitely possible. This can be done by analyzing the secrets and privileges stored and associated with any given asset and determining if they're overly permissive. Hopefully, before an attacker reaches these credentials, your security team has had time to analyze and remove such threats, without relying on a silver bullet to dodge an attacker who has already discovered them.
By returning to the basics, security teams can protect their public cloud estates from being breached by their weakest links. These common threats include having misconfigured workloads; being unpatched or running on unsupported operating systems; not using MFA; or protecting against known vulnerabilities and lateral movement risks.
A little IT hygiene goes a long way, and until you get the security basics right, all the fancy buzzword-enabled tools in the world won't protect you.
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




