Companies struggle to maintain PCI compliance within a year of meeting it, according to a new payment security report by Verizon.

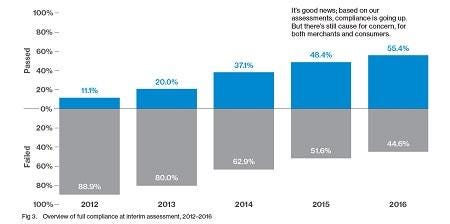
The number of businesses achieving full compliance with their annual Payment Card Industry Data Security Standard (PCI DSS) review reached a record 55.4% last year, but nearly half of companies fall out of compliance within a year, according to the Verizon 2017 Payment Security Report released today.
Even more telling: in all of the nearly 300 payment card data breaches that Verizon investigated in 2010 to 2016, the businesses hit were not fully PCI DSS-compliant at the time of their breach.
"There has been a year-over-year increase in the number of companies that are able to meet the first initial interim validation [first attempt] and that's great news. But is that good enough?" says Ron Tosto, global manager of the Verizon PCI Advise and Assessment Services. "We know that a number of these companies are not able to stay in compliance and only make it to the nine-month mark."
 [Source: Verizon 2017 Payment Security Report]
[Source: Verizon 2017 Payment Security Report]
Nearly half of companies reviewed by Verizon's qualified security assessors last year failed to reach full compliance in the initial review.
PCI DSS is comprised of 12 security requirements that businesses are expected to comply with if they accept, process, or store payment card information. And within each of these requirements, there are specific security actions that need to be performed, otherwise known as controls, to remain in compliance. There are over 200 controls in total, and PCI DSS regularly revises them, potentially making it difficult to remain compliant.
Although there are no federal laws that require companies to comply with PCI DSS, banks and the payment card brands such as, Visa, Mastercard, American Express, and Discover, as well as some states, enforce the requirements and will levy fines and penalties for non-compliance. The Payment Card Industry Security Standards Council (PCI SSC), meanwhile, is responsible for managing the standards.
Degree of Difficulty
The report found that nearly half of the companies that pass compliance will fall out of it within a year or sooner. Companies have 60 days from their initial review to become compliant. Once that is achieved, they receive a final PCI DSS compliance report, which must be revaluated again 12 months later.
"Compliance is incredibly challenging because you never fully arrive. It's a process that must be managed day in and day out. It requires that everyone in the organization own their part in security, which integrates with how they get their job done." says Dawn Koenninger, a vice president at SOLE Financial, which manages a payroll card program and is currently PCI DSS compliant. "Not easy to do when you're in high growth mode. You must have buy-in at all levels, but most importantly from the top."
The security testing requirement in PCI DSS continues to top the list of requirements that are difficult to comply with. Only 71.9% of companies are able to fully comply with this requirement when initially evaluated, Verizon found. This requirement calls for vulnerability scanning, penetration testing, use of intrusion detection, and file integrity monitoring.
"To be effective, testing has to be on a routine basis and follow any major change to an operating environment. Following the companies have to understand the findings, remediate the issues, then retest the environment," Tosto says. "Common mistakes include missing periodic testing, taking action to correct security issues found documented in the test report, and not validating the security issue correction with a retest."
Some companies don't fully grasp the differences between the types of testing within Requirement 11 of the PCI DSS, he notes. He recommends companies fully understand testing and develop testing control effectiveness using the Pin Security Requirements (PSR) as a guide.
PCI DSS's requirement #6 - develop and maintain secure systems - and requirement #12, maintain a policy that addresses information security for all personnel, ranked among the second most difficult to achieve full compliance, with each only garnering success among 77.7% of the companies initially evaluated.
Companies that failed their initial compliance review last year were also missing more controls than in the previous year, the report found. Companies were missing an average of 13% of the controls overall last year, whereas the previous year it was 12.4%.
Source of the Pain
Meeting PCI DSS requirements is like training to be a long-distance runner, Tosto says: "A runner doesn't show up to run on day one, they practice," he says.
But he notes there are common challenges companies face to make those "practice" sessions happen. A shortage of IT security workers, an insufficient security budget, and an absence of a process to keep the maintenance of the requirement controls in place, are the three main contributors that make it challenging for companies to meet and maintain PCI DSS compliance, Tosto says.
Troy Leach, chief technology officer of the PCI Security Standards Council, agrees those three challenges can trip up a company in their compliance efforts, especially the one when it comes to developing a maintainable process.
When the person heading up a business' PCI compliance process leaves the company, for example, that can disrupt compliance, he says, as can a merger. A documented process should be put in place, he notes.
"Your people and technology may change, but if the process remains the same, it will not have as great of an impact," Leach says.
Avivah Litan, a Gartner analyst, says budget and funding to fulfill the PCI DSS requirements weigh heavy on the minds of CISOs. "When I talk to CISOs in the hotel and restaurant industries, they are frustrated they can't get the CEO's support," Litan says. "They [CEOs] say, 'why fund it when we haven't had a breach?'"
Verizon's report shows that IT services achieved the highest level of compliance, with 61.3% hitting the mark during evaluation process, followed by financial services, 59.1%; and retail, 50%. Less than 43% of the hospitality industry, which includes hotels, was compliant.
Litan says PCI DSS compliance should fall on the payment card brands and banks - not on merchants. "The standards are unrealistic for merchants to meet because this is not their business and core competency," she says. "It should fall on the banks to develop a secure system."

Learn from the industry’s most knowledgeable CISOs and IT security experts in a setting that is conducive to interaction and conversation. Click for more info and to register.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




