Enterprises need to recognize that remote access and other pandemic-related security challenges cannot be fixed with buzzwords or silver-bullet security tools.
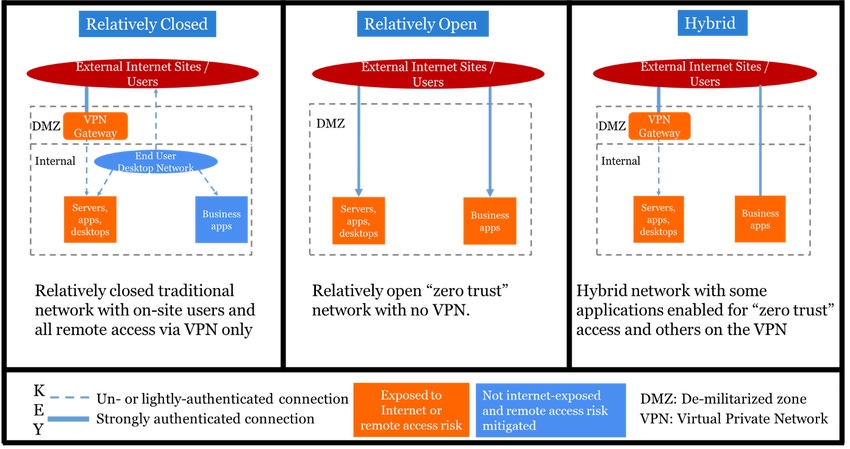
As businesses operate under the COVID-19 shutdown, they undergo forced digitalization. Many people are teleworking, exponentially expanding remote access loads. Organizations also experience disruption to the supply chain, business continuity/disaster recovery (BC/DR) issues, and ramped-up cyberattacks. How well they are able to navigate the new abnormal depends on where they fall in the network security continuum between a relatively closed or relatively open "zero-trust" environment.
Figure 1 above illustrates three network security scenarios:
Relatively closed prepandemic IT environment with main security zones of trust. Users may be strongly authenticated by the VPN, but internally to the network both users and services tend to be trusted with minimal (e.g., password-based only) authentication.
Relatively open IT environment with no VPN and minimal perimeter layers. All access to applications and services gets strongly authenticated via services such as Google Authenticator or cryptographic mechanisms.
Hybrid environment including elements of both the relatively open and relatively closed models.
Expanding Remote Access
Businesses that had robust remote access and/or cloud security strategies before COVID-19 have found it relatively easy to ramp up teleworking. They can run many business applications as is and open up access rapidly to many others. During one of the interviews I conducted for my upcoming book, Rational Cybersecurity for Business — after the COVID-19 shutdown — a chief information security officer (CISO) from an asset management firm told me:
We'd done a tabletop exercise two and a half years ago to uncover weaknesses in remote working and fix them. This exercise was focused on the potential requirement to evacuate offices and keep the business running in the event of an active shooter scenario. We needed to define:
How do we communicate?
What critical systems would we need?
Would team members have the equipment required to work at home? (We even looked at seemingly minor issues, such as whether users have headsets.)
Architecturally, we had to make security decisions about which systems, or security zones, to keep behind the VPN and which to make accessible through the Internet. We implemented a zero-trust architecture and started to move some applications to the cloud. That really helped reduce the load on the VPN.
Although COVID-19 has been a completely different scenario, the remote access challenges are similar. Being prepared in advance has made the disruption much less painful for us.
It's Never Too Late, but…
Other businesses, whose time to prepare in advance has passed, must set themselves realistic expectations. If staff predominantly worked from the office on desktops before the lockdown, organizations may lack the budget and infrastructure capacity to swiftly roll out notebook computers to everyone. Such businesses will need to start, formalize, or expand a bring-your-own-device (BYOD) program as well as a remote access expansion project. Otherwise, they'll be opening up business applications to potentially compromised home devices. It's also important to adapt network architecture to this new way of working.
Look at the use cases below to determine which systems can be exposed to BYOD, remote access, and Web access.

Source: Dan Blum
Zero Trust Is Not Always the Answer
In its most simple description, the zero-trust security architecture holds that all network access should be appropriately authenticated and that the access must never be granted based on device network location alone (i.e., being inside a "trusted zone"). With a capability for strong authentication in place, one can — in theory — safely take down some of the perimeter layers in the relatively closed scenario from Figure 1.
However, zero trust isn't suitable for use cases where staff are working on home computers absent an effective BYOD program that may include endpoint health checks, user awareness training, corporate-provided endpoint security software, and legal agreements. It isn't appropriate when the target applications or systems cannot defend against cyberattackers attempting to exploit direct access. When applications haven't been hardened or isolated commensurate to the risk they create, exposing them to direct Internet access is unwise.
By analyzing use cases similarly to what we see in Figure 2 rather than attempting to force-fit VPNs, zero trust, or any other one-size-fits-all approach, a company could do the following:
Start to get its feet wet with zero-trust access to lower risk assets
Use selected groups of staff members to pilot BYOD solutions in return for higher levels of access to employee intranet informational applications
Load up the VPN only with applications, such as the call center, that pose more risk
Augment or replace the VPN with solutions better suited to the highest risk use cases, such as privileged account management (PAM) tools
Although the zero-trust principles may seem suited to the challenges of our time, proceed with caution. Even Google's BeyondCorp initiative — a poster child for zero trust — took two to three years and a major investment to accomplish. Enterprises just starting now need to recognize that remote access and other COVID-19 security challenges cannot be fixed with buzzwords or silver-bullet security tools. Instead, they demand a risk-based focus and careful attention to network security and identity and access management (IAM) architecture.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's featured story: "Biometrics in the Great Beyond."
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's featured story: "Biometrics in the Great Beyond."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




