Endpoint security is hardly dead, and claiming that it is oversimplifies the challenges corporations face now and in the not-very-distant future.
I got an email from my car the other day, informing me about its need for service. As a security professional, I found it unsettling, not surprising, but unsettling. What’s my car doing on the Internet, anyway? What are the possible implications of that?
Security practitioners within corporate IT are rightly focusing on the emerging risks presented by laptops, tablets, and smartphones when used by employees and contractors in the course of doing business. But other trends are developing all around us that challenge the foundations of our security assumptions.
For example, while worrying about employee behavior at work, we can lose sight of the fact that computing is becoming part of daily life in such a way that it’s nearly impossible to separate "work" and "personal" activities and devices. The concept of a corporate boundary is dissolving as computing and communication endpoints embed themselves in a growing number of devices like thermostats, medical devices, my car, and, in the near future, my clothing. These trends have profound implications for the security industry.
In anticipating our future reality, we only have to look at the recent past and the wide uptake of smartphones. People started bringing them into their workplaces -- spurring the BYOD trend and broad adoption of smartphones in business.
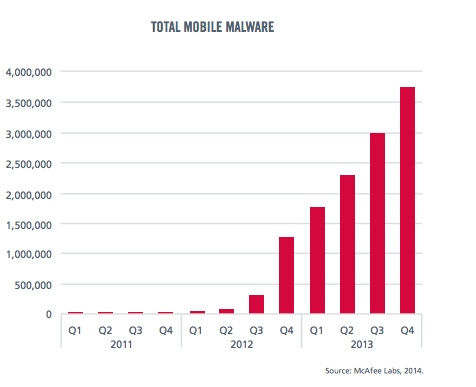
The cybercrime industry was quick to respond. Where mobile malware was once the frontier for malware innovators, today it’s almost a mainstream delivery mechanism. Mobile malware grew 197% between Q4 2012 and Q4 2013, according to McAfee’s Q4 2013 Threat Report.
The death of endpoint security? Not yet
As more devices join the universe of computing endpoints, we should expect a similar uptick in exploits and malware. The endpoint will always be an attractive target for those who seek to intercept or steal information or infiltrate networks.
Given the scope of the problem, it’s fashionable nowadays to claim that endpoint security is ineffective. Endpoints are often considered the weakest link in the security infrastructure, because they are furthest from any central control and there is generally a human using them.
But to claim that endpoint security is dead is to oversimplify the challenges corporations currently face. Now more than ever, endpoint security has a critical role to play in ecosystems that protect highly diverse corporate computing environments against complex security problems.
Layered defenses, but across multiple dimensions
Despite what any security vendor may wish you to believe, there’s no single way to secure either your personal data and identity or corporate systems and data. While layered defenses have been a best-practice in corporate security for many years, in today’s increasingly complex security environment we need to expand our thinking to layers across many dimensions. Specifically, security requires holistic approaches that span people, infrastructure, data, and applications.
People: The boundaries between personal and professional online activities and identities are blurring. Corporate security measures must accept this reality and support people with everything from online identity controls to simplified, embedded processes, making secure computing as easy and transparent as possible.
Infrastructure: Corporations are very adept at securing traditional infrastructure elements such as desktops, laptops, and servers. The security and policies applied to these devices may not be effective with devices as diverse as phones, tablets, wearables, and the Internet of Things. Security controls and measures need to become more intelligent and integrated in order to secure the ever-expanding universe of endpoints and devices.
Data: Pervasive computing capability means that data is highly nomadic. As network boundaries erode, you need to put controls around the data itself. In addition to access and authentication controls, companies must track and audit where sensitive data travels, while empowering people to collaborate and be productive.
Applications: Security isn’t something that can be tacked onto an application at the end of its development. Even in an environment with significant time-to-market pressures, application developers need to be part of the holistic approach to security, delivering vulnerability free software that considers the implications of sensitive and/or regulated data.
Security for the way we live
The biggest shift I see in the industry is that we need to move beyond thinking of security as a set of extra steps, processes, or systems built around our computing environment. As computing becomes more pervasive and embedded, often unseen, in our daily lives, we need to design holistic approaches to security that match the way we live and work.
It’s an exciting time to be in the security industry. There won’t be just one single answer or solution. Many players will be involved in a holistic, systems-based approach to security. And the environment will continue to evolve, as endpoints expand and innovative new technologies enter both our business and personal lives. Security practitioners and developers will be challenged to be innovative and collaborative in adapting to the constantly evolving threat environment.
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




