JIGSAW locks, threatens, and deletes files if you don’t pay the ransom within 24 hours.
April 19, 2016
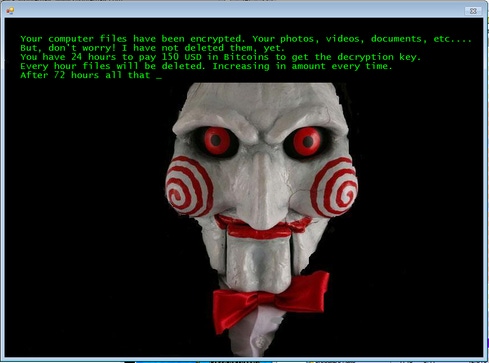
The first thing the victim sees is the creepy image of Billy the puppet from the horror film “Saw” on their computer screen, warning them that they have 24 hours to pay up or their now-encrypted files will be deleted:
The so-called JIGSAW ransomware is the latest twist in the disturbingly rampant ransomware trend, malware infections that lock the victim out of their files and demand payment in Bitcoins – or the files get deleted. What sets JIGSAW apart from other ransomware attacks, besides its horror-flick riff, is the very tight deadline for ransom payment. And akin to how a thriller builds on suspense, fear, and horror, JIGSAW builds pressure on the victim with multiple warnings to pay the ransom or lose his or her data.
“JIGSAW is forcing the hand of the [victim] organization so they are not going to be able to look at backups” or other options to retrieve their data, says Michael Davis, CTO of CounterTack. “It’s forcing them to pay up immediately and sooner” than other ransomware, he says.
Trend Micro researcher Jasen Sumalapao describes it as an exponential attack. “Recent crypto-ransomware families have ransom amounts that grow as time passes, but not with the same increments as JIGSAW. To make matters worse, it deletes a larger amount of files with every hour while the amount to be paid also increases,” he said in a blog post today. “And with the exponential increase of files being permanently deleted, users may be pressured into paying the ransom so they may either save the remaining files, or avoid paying a larger ransom.”
The ransom starts anywhere from $20 to $250.
JIGSAW, aka BitcoinBlackmailer.exe, appears to have been created on March 23, and was first used in attacks a week later. According to researchers at Raytheon’s Forcepoint Laboratories, the author uses the file extension ‘.FUN.’
Fear is a big component of the success of most ransomware attacks. Victims feel trapped and panicked, especially if they don’t have good backups of their data. So many relent and pay the ransom; but there’s still no guarantee they’ll see the data. According to new data from the Ponemon Group, just 38% of organizations have a plan or strategy for handling a destructive malware attack like ransomware or other data destruction methods, and that’s down from 43% last year.
Davis, whose company commissioned the Ponemon study, says the drop reflects a reality check as ransomware became more destructive and pervasive. “There was a little overconfidence last year,” he says. “Ransomware didn’t have the effect then that it had at the end of 2015 and in early 2016.”
The data, which is part of the 2016 State of Endpoint Report, shows how most organizations just don’t have the capability to defend or prepare for a ransomware attack. “This is showing that access control is not [happening] in organizations,” he says. One user getting infected with ransomware shouldn’t end up bringing an entire organization to its knees, he says.
More than half of organizations consider ransomware one of the most harmful attacks today, behind zero-day attacks were number one (71%); followed by distributed denial-of-service (DDoS) attacks (68%); and exploiting an existing vulnerability (53%).

Gain insight into the latest threats and emerging best practices for managing them. Attend the Security Track at Interop Las Vegas, May 2-6. Register now!
According to Trend Micro’s research, JIGSAW infects machines via a file they download from a free cloud storage service called 1fichier[.]com. This isn’t the first time the cloud storage provider has inadvertently hosted malware, either, but the malicious URLs have since been removed from their site. Porn sites also are spreading the ransomware, and JIGSAW uses a different threat for those victims with the message: “YOU ARE A PORN ADDICT.STOP WATCHING SO MUCH PORN. NOW YOU HAVE TO PAY.”
JIGSAW, like many ransomware variants, is not sophisticated nor does it contain any new features that haven’t yet been seen in this type of malware. It’s more about the psychological fear factor, researchers say.
Related Content:

About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


