Here are seven ransomware variants that can creep up on you.
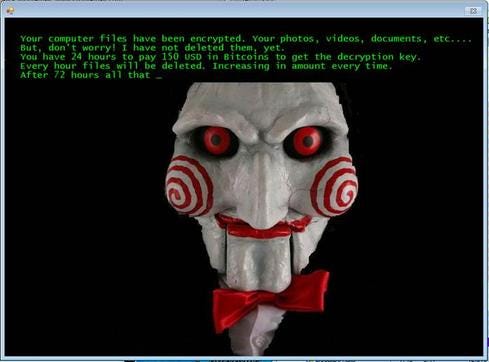
As the season of evil witches, ghosts, goblins, and ghouls approaches, it’s time to be on guard. But security managers face scary prospects year-round, especially as new strains of ransomware escalate. And ransomware variants are getting more pervasive - and creepier - than ever.
The FBI says that from Jan. 1, 2016 to June 30, 1,308 ransomware complaints have been reported, totaling $2,685,274 in losses.
And it appears that the ransomware “business” will continue to grow for cybercriminals. Ed Cabrera, chief cybersecurity officer at Trend Micro, says his research team tracked 29 ransomware families last year, and this year is on pace to track well more than 100 variants.
"These ransomware attacks are much different than traditional data breaches in that they go right after the victim," Cabrera says. "It's not like in the past where data was exfiltrated and sold to other criminals."
Most of these ransomware variants encrypt a person’s machine and try to extract a ransom, typically several hundred dollars. What keeps security managers up at night is that ransomware has made its way to the enterprise. The $17,000 ransom paid by Hollywood Presbyterian Hospital earlier this year is of particular note. But new variants attack entire databases and servers – and they now use familiar chat features to make it easier for the victims to pay the ransom.
As a cautionary tale for the season, here are seven of the scariest ransomware variants. This list is based on a consensus drawn from interviews with Trend Micro's Cabrera; Chris Day, CISO of Invincea; and Bryan Lee, threat intel analyst for Unit 42 at Palo Alto Networks.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




