
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
Some have even left behind commercial software and migrated to open source or in-house homegrown applications. <a href="https://www.darkreading.com/edge/theedge/appsec-concerns-drove-61--of-businesses-to-change-applications/b/d-id/1336934" target="new">Continue for synopsis</a> or read <a href="https://www.informationweek.com/whitepaper/cybersecurity/security-monitoring/how-enterprises-are-developing-and-maintaining-secure-applications/413993" target="new">full research report</a>.
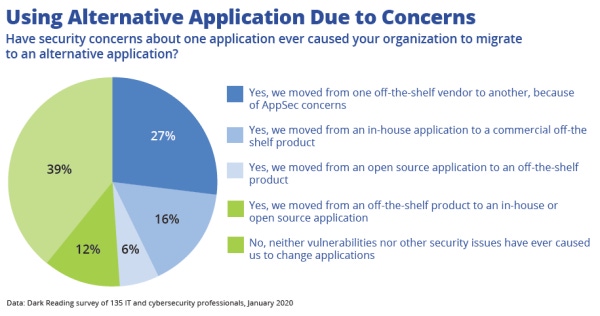
The marketplace is beginning to pinch the software industry for application security failings and complications, according to a new Dark Reading study.
Sixty-one percent of respondents to the survey, released today, stated that security concerns about one application have caused them to migrate to an alternative. Twenty-seven percent swapped one commercial off-the-shelf (COTS) application for another. Others migrated over to a COTS solution, leaving behind either open source (6%) or in-house developed (16%) tools. However, 12% dropped their commercial software altogether, in favor of either open source or in-house developed apps.
Why the changes? Some of the reasons are familiar.
For example, internal dev teams may be poorly trained on secure coding and be liable to run into business conflicts with their counterparts in the security department. When asked to name the biggest risk to appsec, the No. 1 answer was "developers untrained in security," cited by 38% of respondents. This worry persists despite a majority of respondents giving positive reviews of the relationship between these two teams.
And, of course, commercial software vendors' security records vary widely; while one may have a large dedicated security team, supported by a bug-bounty program and a reliable process for issuing patches and updates, another may have none of those things and leave bugs unfixed for years. Similarly, open source communities vary in the kind of support they provide.
Some reasons, however, are less familiar. Recently, new security challenges have arisen to further complicate the choices that businesses make about applications.
For example, this year the United States, citing national security concerns, prohibited the use of technologies from Chinese tech giant Huawei, as well as surveillance technologies from other Chinese companies. In 2017, the administration ordered the removal of Kaspersky Lab cybersecurity tools from all federal systems for similar reasons.
Meanwhile, attacks exploiting vulnerabilities in open source code libraries have increased -- and while that might initially make open source applications appear less attractive, these components are also frequently used by internal development teams and commercial software vendors alike. Fortunately, most respondents have a process in place to repair vulnerabilities in open source software components, though 21% admit to being "completely at a loss."
Read the complete report, "How Enterprises Are Developing and Maintaining Secure Applications," here.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

