
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
Increasing sophistication of ransomware attacks might be forcing victims to open their wallets. Click image to read more.
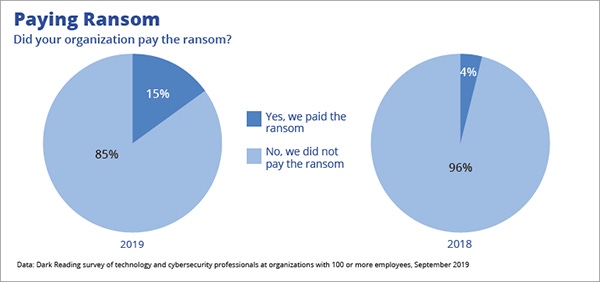

Fewer survey respondents reported ransomware attacks in 2019 than in 2018, according to a recent Dark Reading survey. Yet, the number reporting that they paid an attackers' ransom nearly quadrupled -- rising to 15% of those that had suffered a ransomware attack.
Ten percent of respondents stated that their organization had suffered a ransomware attack (down from 12% in the 2018 study). Of those, fifteen percent said that they paid the ransom, up from just 4% last year.
Ransomware attacks are becoming increasingly severe and sophisticated. As Jai Vijayan wrote for Dark Reading last month:
Some recent developments include growing collaboration between threat groups on ransomware campaigns; the use of more sophisticated evasion mechanisms; elaborate multi-phase attacks involving reconnaissance and network scoping; and human-guided automated attack techniques. ...
In many attacks, threat actors have first infected a target network with malware like Emotet and Trickbot to try and gather as much information about systems on the network as possible. The goal is to find the high-value systems and encrypt data on it so victims are more likely to pay.
If we look at the big picture, we will discover that what is changing is the threat actors' approach to distributing the Trojans and selecting their victims," Fedor Sinitsyn, senior malware analyst at Kaspersky says. If five years ago almost all ransomware was mass-scale and the main distribution vector was via spam, nowadays many criminals are using targeted attacks instead.
On a sunnier note, more companies might be paying ransoms because they have cyber insurers to help them bear the cost of those payments. As the police chief of Valdez, Alaska told Dark Reading after the city fell victim to ransomware, "I can't emphasize enough how much [cyber insurance] saved our community."
Thirty-four percent of respondents to the Dark Reading report said they have insurance specifically for cyber incidents -- double the number reported in 2017 -- and 18% reported filing a claim.
Download the full report, How Data Breaches Affect the Enterprise, here.
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

