
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
What's it going to take to prod organizations to implement a post-quantum security plan? Legislative pressure.
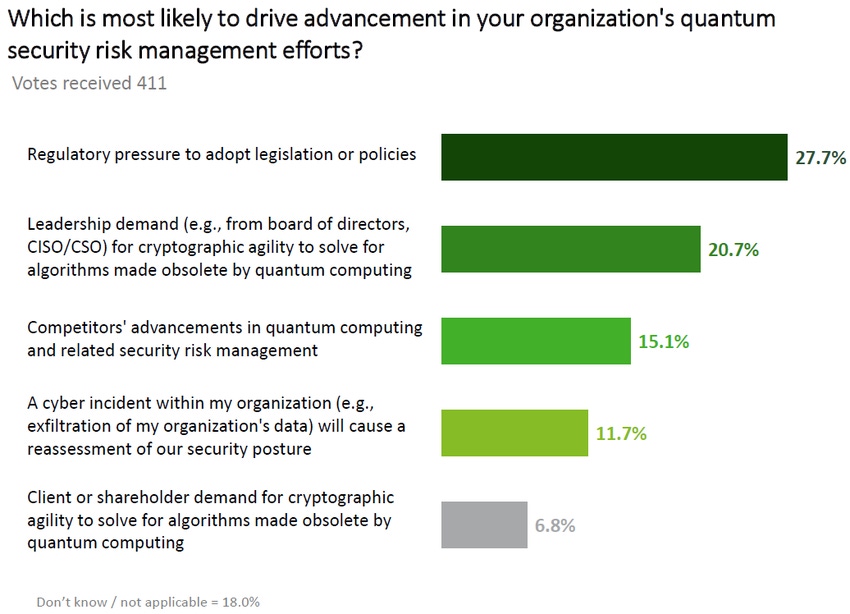
Security professionals might need a little help motivating themselves and their organizations to implement measures to counteract the threats inherent to quantum computing. According to a recent survey from Deloitte, enterprises say without external pressure, they won't be pushing forward their plans to implement precautions.
When asked what will drive their organizations to step up its quantum security risk management, over one-fourth (27.7%) said regulatory pressure, followed by one-fifth (20.7%) who cited pressure from the board of directors or the C-suite. The rest of the answers cascaded down accordingly: responding to competitors' pressure (15.1%), embarrassing internal incidents (11.7%), and customer or investor concerns (6.8%).
Because changing the way an organization handles data is a major decision, it makes sense that security staffs want the higher-ups to take responsibility for any change in direction. Perhaps to accommodate this desire, US President Joe Biden issued a pair of presidential directives in May 2022 to establish a national policy on what he called quantum information science, or QIS. Combined with NIST's recent approval of four post-quantum cryptography algorithms, these could provide the added push organizations need in order to get started combating a threat that is five to 10 years away.
The Deloitte survey asked about attitudes among organizations that were already considering the benefits of quantum computing. Responses showed that just over one-quarter of respondents had conducted a quantum risk assessment, with another quarter planning one in the next five years. About half of the respondents considered their organizations at risk for harvest-now/decrypt later (HNDL) attacks, in which encrypted files are stolen and stored until the technology to crack the encryption comes to market.
The scale of the potential threat to current computing practices is reminiscent of the Y2K bug, a database shortcoming that stored years as two-digit fields instead of four digits, the implications of which created both a popular panic and concentrated effort across industries to head it off. The preemptive policies from the US, as well as activities in the European Union, may bear fruit in pressuring corporations and governmental entities to institute post-quantum cryptography (PQC) and other protective measures. Boards of directors and company executives might find reassurance as government efforts progress and less-disruptive ways to begin the switchover emerge.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

