Updates built for remote employees include an endpoint data loss prevention platform, insider risk management, and double key encryption.
Microsoft today debuted new security, risk management, and compliance tools for its Microsoft 365 platform during its 2020 Inspire partners conference. These updates arrive as organizations reconsider data protection and compliance strategies while they plan for a future of remote work.
Today's announcements include the public preview of Microsoft Endpoint Data Loss Prevention (DLP), Double Key Encryption, new Insider Risk Management capabilities, and communication compliance tools in Microsoft Teams. All are meant to help businesses better protect their data.
"This whole shift to remote work has really increased the need for organizations to re-evaluate their security, compliance, and risk management practices," said Alym Rayani, senior director of Microsoft 365 compliance marketing, in a press briefing. "You have a lot of employees accessing corporate data at times from home computers, or sharing and collaborating in new ways, so that creates more risk and potential for data leaks for organizations."
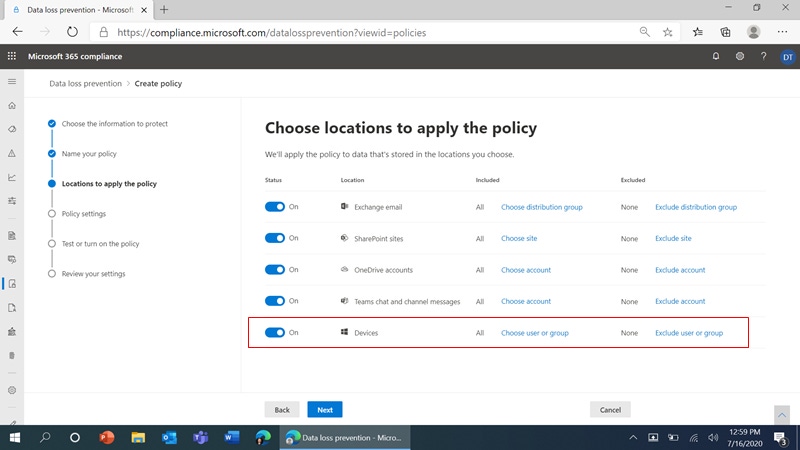
Microsoft Endpoint DLP extends the security measures already offered in Microsoft Information Protection (MIP), a built-in tool that classifies and protects data across Microsoft 365 apps and services including Word, PowerPoint, OneDrive, SharePoint, and Exchange, on-premises or in the cloud. Endpoint DLP brings these classification and security capabilities to endpoint devices, where it identifies and protects data without restricting the use of apps, browsers, or services.
When someone takes a potentially risky action, Endpoint DLP sends an alert with policy tips and guidance to remediate. The experience carries over to third-party apps like Dropbox: If someone tries to copy a file with sensitive data to a personal Dropbox account on Microsoft Edge, they person will see an alert and the event will be recorded and available in the compliance center.
Endpoint DLP is built into Windows 10 and the Edge browser, so companies don't need to install or manage additional software to use it. Users only need to create a DLP policy once in the Microsoft 365 compliance center, then apply the policies to Exchange, Teams, SharePoint, OneDrive for Business, and now endpoint devices. The tool is now available in public preview, Microsoft reports, and it'll be released in a Windows 10 update when it's generally available.
Another risky aspect of remote work is the distractions employees face. Shared home offices, kids taking remote classes, and other disruptions could drive unintentional insider incidents, CERT research shows. To identify and mitigate these risks, Microsoft is building on capabilities introduced in Insider Risk Management, a tool released in February to detect insider threats.
Part of this involves expanding the types of behaviors that could be considered risky. Insider Risk Management will now flag insights across Teams, SharePoint, and Exchange, including sharing folders, files, and websites from SharePoint Online to domains marked "unallowed"; downloading content from Teams; and emailing outside the business to "unallowed" domains.
IRM captures signals from Windows 10 endpoints to provide data on the capture and exfiltration of sensitive information. This may include using the Edge browser to copy files to personal cloud storage, using Edge to download content from an unallowed domain, or transferring files to a network share. Businesses using Microsoft Defender Advanced Threat Protection can see when someone tries to disable MFA or install unwanted software.
Double Key Encryption, a new feature now in public preview, brings stronger protection for mission-critical data. Microsoft 365 already encrypts customer data at rest and in transit. Double Key Encryption lets businesses use two keys to protect their data: one they control and the other stored in Microsoft Azure. Both are required to view data protected under Double Key Encryption. Microsoft can only access one key, meaning it can't access the data.
This added protection is meant to help organizations in highly regulated industries – financial services and healthcare, for example – protect sensitive data, like trade secrets and patents, from cybercriminals. These businesses can add access controls to the Double Key Encryption service, store their data on-premises or in the cloud, or move highly sensitive data to the cloud.
The pandemic has forced employees to communicate electronically, a shift that has implications for regulatory and code-of-conduct compliance. To help businesses address communication risks, Microsoft is making changes to its native Teams integration.
These include the ability to remove Teams messages that violate policy and replace them with a message explaining why it wasn't compliant. New communication compliance roles are meant to help manage roles and responsibilities across different departments, including IT, legal, and compliance. These roles are separated into different categories, including administrator, investigator, analyst, and viewer, with more granular permissions for each role. Teams will now detect repeated bad behavior over time, which lets reviewers prioritize remediation actions.
Related Content:

Register now for this year's fully virtual Black Hat USA, scheduled to take place August 1–6, and get more information about the event on the Black Hat website. Click for details on conference information and to register.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




