The Building Security In Maturity Model is the only detailed measuring stick for software security initiatives, and it continues to evolve.
The Building Security In Maturity Model (BSIMM) is now in its 10th iteration. It continues to evolve as the only detailed and sophisticated "measuring stick" for software security initiatives (SSIs), also known as application or product security programs.
The BSIMM is an observational model. While it's useful for some industry experts and pundits to prescriptively document what worked for them that one time in that one situation, the BSIMM took a different path. The BSIMM observes what's happening in hundreds of organizations and tells everyone how firms are actually spending their time and money to achieve an appropriate level of software security across their entire software portfolio. Since its creation over a decade ago, this data-driven approach has evolved through the analysis of nearly 200 SSIs globally. BSIMM10 represents real-world data from 122 organizations over eight industry verticals: cloud, Internet of Things (IoT), independent software vendors (ISVs), high technology, healthcare, insurance, financial services, and retail.
The BSIMM started in 2008 with a set of 110 activities. Over time, one activity was removed and 10 activities were added. Why? Because that's what we observed in the world of software security. To help everyone understand how frequently each of the 119 BSIMM10 activities are observed across the current 122 firms, we use frequency analysis to sort the activities into levels. Commonly observed activities — across all verticals — are tagged as level 1, while sparsely observed activities are level 3.
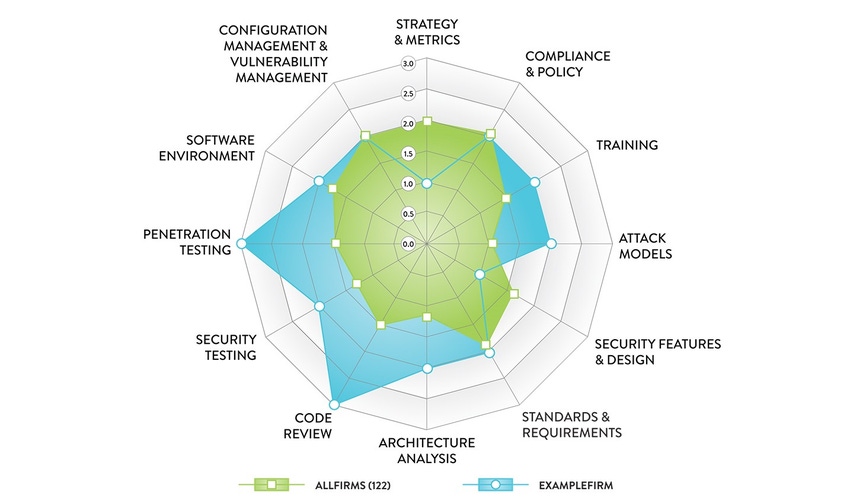
That means we can use a high-water mark diagram such as the one below to illustrate how frequently various levels of activities are observed in firms participating in the BSIMM study as well as in a particular firm. The diagram shows that the current 122 firms are collectively putting effort into more activities in Strategy & Metrics, Compliance & Policy, and Standards & Requirements compared with Attack Models and Architecture Analysis, whereas the ExampleFirm places value on Attack Models, Code Review, and Penetration Testing. This view acts as a proxy for overall maturity but can also be broken down on an industry vertical basis to observe effort across activities and growth differences between various industries.
In highly regulated industries such as financial services, for instance, it's not surprising to see a spike around Compliance & Policy, whereas we typically don't see that spike with ISVs or IoT. Most verticals measured currently within the BSIMM have a good handle on the foundational security activities.
We're seeing some verticals collectively doing more than others in various areas for a variety of reasons. In certain industries, effort in particular activities is driven by legal reasons relating to regulations, statutes, and contracts. In others, customer expectations and preferences, along with perceptions of privacy, may drive which of the 119 BSIMM10 activities are emphasized over others.
Let's take medical device manufacturers as an example. The software built into the monitors and devices produced for hospitals and doctors' offices is going to be out there for 20 years, perhaps even longer. Imagine what software attacks are going to look like in 20 years! Now, imagine doing that 20 years ago and predicting what software security mechanisms would be needed for today. As you can see, this is a very complex problem and different firms in the vertical approach the problem differently.
Different verticals emphasize different security activities based on their different perceptions of risk. We see that reflected in their spider diagrams, which in turn reflects the foundational activities and the more uncommon activities they implement to help build out their particular SSI.
It isn't reasonable to say that Healthcare Company X is more mature than Retail Company Y because this would be like comparing apples to oranges. Why? Because each firm will build the right program for its needs. Even if they are in the same business, a firm doing 30 activities and a firm doing 50 activities might have the same overall maturity relative to their software portfolios. However, we can say that one group of firms within a specific industry vertical does things that seem to be collectively important throughout the vertical, while another group of companies in another industry vertical carries out completely different activities that seem to be important to them. They're not the same things necessarily, and yet there are trends among each industry.
BSIMM10 is the first iteration of the study to formally reflect changes in SSI culture, observed in a new wave of engineering-led software security efforts originating bottom-up in the deployment and operations teams rather than top-down from a centralized software security group. Engineering-led security culture has shown itself to be a means of establishing and growing meaningful software security efforts in some organizations, though it struggled to do so even just a few years ago.
Along these cultural lines, BSIMM data also show that the DevOps movement, along with the growth in continuous integration/continuous development (CI/CD) tooling and digital transformation, is affecting the way firms approach software security for their software portfolios. BSIMM10 includes three new activities for this reason.
In recent years, as organizations have started using DevOps practices that pushed software to the cloud, we're seeing that this is a big change agent in most firms. As DevOps culture and CI/CD toolchains intersect with cloud deployments, we're realizing this is a game-changer in terms of software security. We don't yet understand the full impact as we're still in the early phases of the evolution of these technologies and strategies. Upcoming iterations of the BSIMM will certainly shed more light on what organizations are doing to get from DevOps to DevSecOps and to secure their cloud deployments.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "Account Fraud Harder to Detect as Criminals Move from Bots to 'Sweat Shops'."
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "Account Fraud Harder to Detect as Criminals Move from Bots to 'Sweat Shops'."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




