KL-Remote is giving Brazilian fraudsters a user-friendly "virtual mugging" platform.
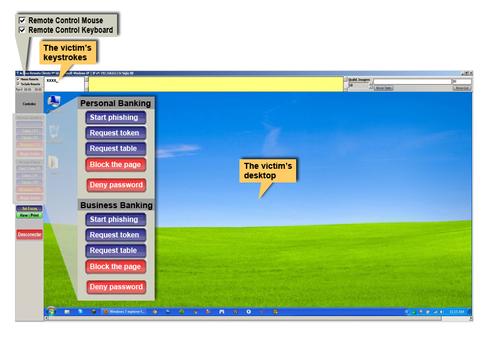
Another user-friendly attack toolkit is on the market, and it's perfect for the budding Brazilian banking fraudster. It's got an attractive, user-friendly interface that includes a "start phishing" button. And it effectively circumvents both two-factor authentication and device identification protections.
IBM Security Trusteer released details today about this KL-Remote, a remote overlay toolkit that performs what it calls "virtual mugging." Unlike banking Trojans, KL-Remote is less automated (because where's the fun in that). It requires attackers to do some manual sleight of hand, but it makes it very easy to pull off.
The toolkit is distributed by being embedded in other malware. It comes preloaded with a list of targeted banking URLs. When the infected user visits one of those sites, the malware operator gets an alert and can then decide whether or not to proceed with an attack.
Here's what the attacker's interface looks like:
As IBM describes it, "during a remote overlay attack, the criminal is virtually looking over the victim's shoulder, watching his or her every move. At some point, the attacker takes direct control over the device without the victim's knowledge."
When KL-Remote goes into action, it first takes a snapshot of the infected user's browser screen and lays it over the real website, preventing the user from interacting with the real site. A quick click of the "start phishing" button begins issuing a series of prompts -- customized for each bank -- stating that the user needs to install a security update, and it tricks the user into entering the password and one-time token.
Once the user enters that data, the tool throws up a waiting message -- one of those usual "installing update, this may take a few minutes" messages. While the user waits, the tool takes control of the infected machine's keyboard and mouse and carries out whatever fraudulent financial transactions the attacker would like with that user's bank account.
The user can't see the activity, and the bank can't tell that the person conducting the transaction isn't the account holder logging in from the usual device.
The attack effectively circumvents two-factor authentication and device identification.
Instead, identifying the fraud would require a combination of detecting malware infection, use of remote access tools, abnormal browser patterns, or abnormal transactions.
For now, KL-Remote is available only in Portuguese, and it is only in use in Brazil. Researchers say it could be adapted to other languages, territories, or industries.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




