In the past 12 months, 30% of ransom demands topped $30 million, but victims who negotiated were able to drive demands down significantly.
August 12, 2021
The only real question about ransomware trends these days is not whether there has been any let-up in the relentless pace of threat activity, but rather by how much attack volumes, attack scope, and ransom demands increased over a particular period.
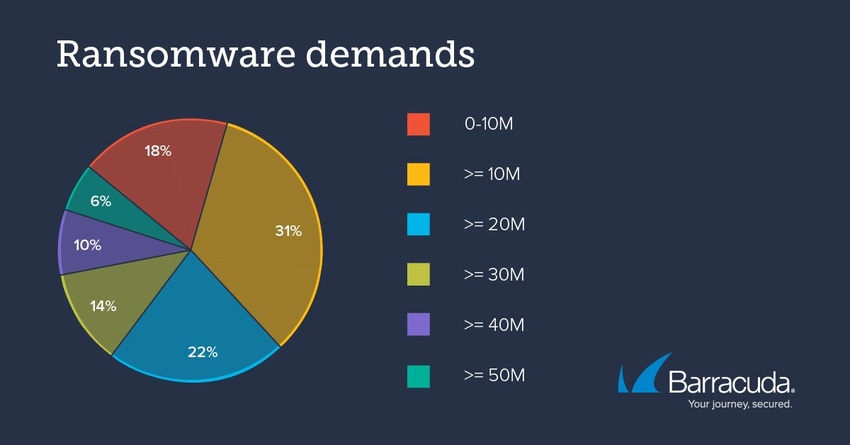
A new report this week from Barracuda offers some fresh insight on all fronts. Between August 2020 and July 2021, researchers from the security firm identified and analyzed a total of 121 ransomware incidents — a 64% increase over the prior year. Thirty percent of those incidents involved ransom demands of $30 million or more; 6% topped a staggering $50 million.
While municipal governments, healthcare, and education sectors continued to be heavily targeted, Barracuda found an ominous increase in ransomware attacks on organizations in previously less targeted sectors, such as financial services, travel, and infrastructure. In fact, ransomware attacks against organizations in these sectors represented 57% of all ransomware attacks that Barracuda analyzed over the past 12 months, compared with just 18% in the prior year.
The security vendor found ransomware operators are increasingly focusing on supply chain attacks, such as those on trusted software vendors and IT service providers, with the goal of compromising multiple organizations via a single attack. The most dramatic example of such an attack in recent months was the one on Kaseya in July, which resulted in ransomware being deployed on several of the company's downstream managed service provider customers.
"These attacks are increasing in sophistication," says Fleming Shi, chief technology officer at Barracuda.
Phishing attacks, where threat actors acquire the victim's credentials, continued to be the most common initial infection vector. "However, in some cases, we see the attackers can target victims based on stolen [and] sold credentials from the Dark Web," Shi says.
Other vendors have also reported a recent sharp increase in the use of banking Trojans and other malware downloaders for ransomware distribution.
Barracuda is among several vendors that have reported a sharp increase in ransomware volumes in recent months. In July SonicWall reported observing a 151% increase in ransomware attacks during the first half of this year compared with the same period in 2020. The second quarter — with nearly 189 million ransomware attacks — was the worst for ransomware that SonicWall said it has ever recorded. Overall, the security vendor counted a huge 304.7 million attempted ransomware attacks in the first six months of 2021 compared with 304.6 million for all of 2020. The attack volumes put 2021 on track to be the worst ever for ransomware, according to SonicWall.
The most notable — and concerning — attacks so far this year include the attack on Colonial Pipeline in May that caused temporary gas shortages across the US East Coast, another shortly after on meat processing giant JBS Foods, and last month's attack on Kaseya.
A Handful of Groups
Barracuda's analysis shows that a handful of large gangs were responsible for many of the ransomware attacks and incidents it identified over the past year. Two of the most prolific were the operators of REvil, which accounted for 19% of all attacks that Barracuda encountered, and DarkSide, the group behind the Colonial Pipeline attack, which accounted for 8% of all attacks.
The Russia-linked REvil, which was responsible for the Kaseya and JBS Foods attacks, went mysteriously offline shortly after the Kaseya incident. Some have speculated the move was likely prompted by pressure from a state entity. In addition, DarkSide — also Russia-based — announced it was quitting operations and made its decryption keys publicly available soon after its attack on Colonial Pipeline, likely for similar reasons.
These developments — and aggressive law enforcement takedowns of groups and infrastructure behind the Emotet botnet and the Egregor, NetWalker, Cl0p, and other ransomware families in recent months — represented some significant victories for defenders, in general. Barracuda also found that when victims were willing to negotiate with attackers, they were able to drive ransom demands down significantly. As examples, the vendor pointed to JBS Foods negotiating its ransom payment down to $11 million from an initial ask of $22.5 million, and German company Brenntag convincing its attackers to accept a $4.4 million payment instead of the $7.5 million they had initially demanded.
"Payment often varies depending on negotiation and actual 'proof-of-data' verifications," Shi says. However, for incidents that Barracuda is aware of, the reduction in ransom amount is significant — in fact, above 50% — when organizations negotiate.
Predictably, even as law enforcement and government made some headway in disrupting major ransomware operations over the past years, attackers have kept evolving their tactics as well.
In a report this week, researchers from Broadcom's Symantec Enterprise Group reported observing leading ransomware groups beginning to use multiple ransomware families — sometimes midway through an attack — to achieve their goals against a targeted organization. In one attack, for example, Symantec says it observed a threat actor that had been using the Conti ransomware family suddenly switch to Sodinokibi (aka REvil).
The goal in switching between ransomware families appears to be an attempt by attackers to increase their chances of success, says Dick O’Brien, senior research editor at Symantec, part of Broadcom.
"Ransomware actors continue to refine their tactics in order to maximize their profits and increase the chances of their attacks succeeding," he says. "From what we can see, it's the more experienced affiliate gangs who tend to switch. Our reason for believing this is that they're groups who've developed their own TTPs and maintain them even if they switch affiliation to another ransomware family."
Less experienced operators often tend to follow playbooks provided by ransomware creators and may be more reliant on a single paymaster, O'Brien says.
Also, predictably, the recent exit of several major ransomware groups — while impactful from a messaging standpoint — has done little to slow ransomware attacks. Symantec, for instance, found that Sodinokibi/REvil's exit has only resulted in a surge in attacks involving LockBit, another ransomware family that threat actors have begun using instead as their choice.
"As long as there is a business in ransomware attacks, there will be successions of the criminal groups," Shi says.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




