What cybercriminals now charge for stolen identities, counterfeit identities, hacking tutorials, DDoS, and other services.
December 15, 2014
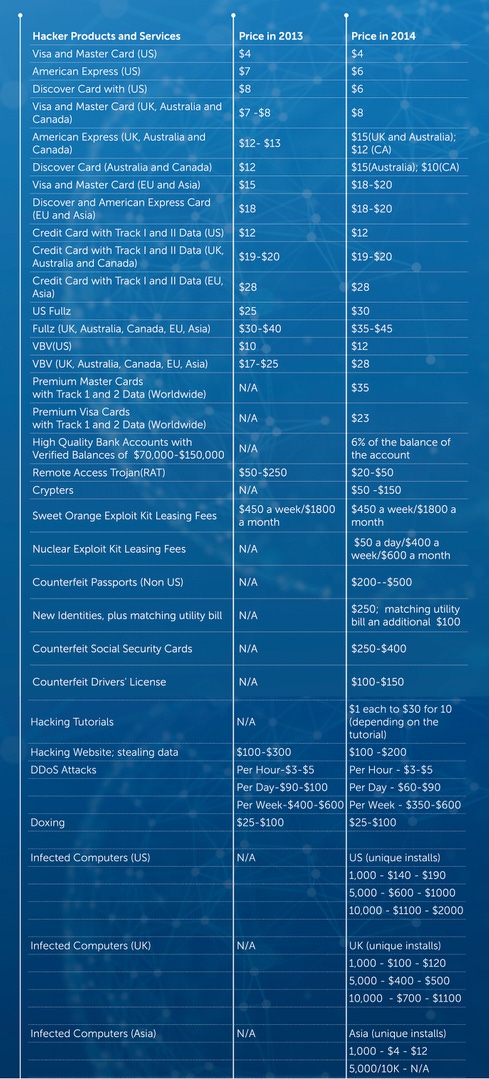
One year after the cybercrime underground slashed the price of a stolen identity by as much as 37% due to a glut in the black market, the price tag for a pilfered ID has inched upward again.
Researchers at Dell SecureWorks published their latest report on the underground hacker market today. Counterfeit identities are the new hot product to support fraud -- new fake identity kits, passports, Social Security numbers, utility bills, and driver's licenses. A new identity, including a working SSN, name, and address, goes for $250, and for an additional $100, you can get a utility bill for ID verification purposes when perpetrating fraud, the researchers found.
Stolen IDs are cheaper than phony ones, but a bit pricier than last year. A "fullz" -- as a stolen personal identity is known in the underground -- now goes for $30 in the US, up from $25 last year. A fullz in the UK, Australia, Canada, Asia, and the European Union is priced from $35 to $45, up from $30-$40 in 2013.
Meanwhile, the massive volume of stolen payment cards up for sale in the wake of an epic year in retailer data breaches has led to more nefarious vendors of stolen and counterfeit identity information trying to make a buck than ever, according to Dell SecureWorks. As a result, more of these vendors emphasizing customer service, with 100% guarantees on stolen information they're selling, for example. One seller promises to replace all "dead" stolen credit cards.
"The market almost mimics a real [and legitimate] one," says David Shear, network security analyst with Dell SecureWorks. "When you buy, they guarantee it will work up to a certain amount, [for example]. They are going out of their way" to differentiate based on customer service. Among some of their offerings are frequent buyer discounts and a more professional-looking presence.
The bad guys also are offering more services to their customers, such as tutorial services on how to hack and commit fraud. Among the services: basic carding, cashing out fullz, ATM hacking, and successful online banking fraud. The tutorial manuals are priced anywhere from $1 to $30.
Premium credit cards -- platinum and gold cards, for example -- can be purchased in bulk. One vendor offers a package of 10 cards at $13 apiece and up to 2,000 cards at $9 apiece. A single premium payment card can go for as much as $35. That same site says it has 14 million US credit cards for sale, plus hundreds of thousands more from other countries.
"I was surprised they said that. Most don't tell you how many cards they have," Shear says.
The price of a remote access Trojan (RAT) has dropped dramatically this year, from $50-$250 in 2013 to $20-$50 this year -- mostly Darkcomet, Blackshades, Cybergate, Predator Pain, and Dark DDoSer. Why the major price cut? The researchers believe it's due to the number of free RATs available in the wake of RAT source code leaks, which has driven the price point down.
[New report unearths what cybercriminals are charging for stolen identities and hacking services, such as DDoS and doxing. Read Glut In Stolen Identities Forces Price Cut In Cyberunderground.]
Bad guys buying bots can purchase a package of 5,000 compromised machines in the US for between $600 and $1,000. That's pricier than a UK bot package, which goes for $400-$500; the difference is likely due to the higher volume of financial site access of US machines.
The credentials to a "high-value" bank account with a balance of $70,000 to $150,000 can be purchased for about 6% of the balance amount in the underground. So that's $4,200 for access to a $70,000 bank account, the researchers found.
Interestingly, the report says there weren't many doxing services this year like there were last year. The ones that were offering services do so for $25-$100.
Here is a look at the underground pricing SecureWorks found:
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


