There are good reasons why the Kill Chain is being used by some of the most successful information security teams around. Here are three.
I first learned about the Kill Chain when I was working with the organization known as the Defense Industrial Base, made up of the largest US government contractors. I recall a briefing we had on the KC, and when I went back to work the following week, I was frantically drawing the KC model on my whiteboard and exclaiming to co-workers that it was the greatest thing ever… but I didn’t know why.
The reality was, we were in our infancy as a security operations center and incident response team, let alone as a security organization hit with the new realities of the cyberworld. As such, we were just learning what others, like Lockheed Martin, had considered fundamentals by that point. It would be a couple years later, when I had moved on and my current team was looking to evolve our internal SOC and IR processes, that I truly saw the power of the Kill Chain. Let’s discuss three awesome ways to use the KC.
Detection
When it comes to enterprise detection, the Kill Chain is useful for understanding what your capabilities are, as well as your gaps in coverage by tools and threat actors. Simply put, not all detection tools are able to detect on all indicator types, nor are they able to cover all steps in the KC.
Step 1: By first laying out all of the indicator types by KC phase, you begin to paint a useful picture.
Step 2: By identifying which indicators can be used by each tool, by KC phase, you understand the capabilities of each tool.
Step 3: Aggregating together your detection tools will give you a holistic view of where your gaps lie or, in many cases, overlap. For example, you may find that your organization is only capable of detecting adversaries during KC7 Actions on Objectives and/or perhaps have zero visibility into KC3 Delivery. Among other things, understanding your capabilities at such a granular level can help you focus investment spend properly.
Step 4: Finally, by performing the same exercise by threat actors, you can better understand the visibility gaps and seek out intelligence to successfully plug those gaps.
Post-Incident Analysis
I’ve seen many different flavors of post-incident meetings over the years. Most are nothing but organized chaos where countless things are thrown around, and a decision is made to purchase some technology perceived as a panacea so that the incident won’t happen again. While some usefulness may come of that meeting, where I’ve seen post-incident reviews excel is by leveraging the Kill Chain model to systematically break down the attack. Using the KC as a framework to answer questions as to how the attack played out, and dissecting each step for what the adversary did and why it worked, may provide a wealth of understanding of the attack, the actor, and what should be done afterwards.
Communication
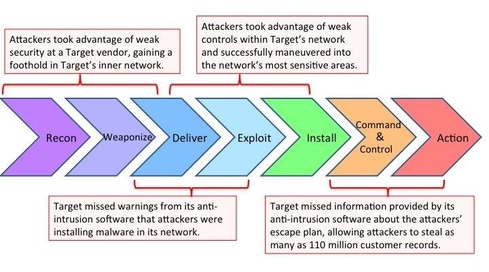
Have you ever tried to explain to the C-suite how an attack happened? It can be challenging. However, the Kill Chain offers a simple and powerful way to look at a very complex situation and tell a story. In a world driven by PowerPoint presentations, you can easily explain the concepts of the KC in terms that everyone will understand, without getting technical, and follow a linear approach to explain the details of the attack to your audience. While I don’t fully agree with the example below, here is a real-world use case that shows how powerful the KC can be to explain the complex Target breach to US Senators, an audience that would have very little technology background.
Detractors
Detractors of the Kill Chain (see {doclink 1317542}) will generally state two things: It can’t be used to look at issues other than external attacks, and since a lot of things happen during KC7 Actions of Objectives, it is too broad. While technically correct, the Kill Chain provides a solid and proven framework that can be augmented to fit different use cases. In the case of an insider breach, an employee would perform internal “Reconnaissance,” “Exploit” control weaknesses, possibly “Install” software, and most definitely look to achieve the “Actions on Objectives.” As for the argument that KC7 is too broad, I’ve seen teams take liberties with KC7 and enhance it with a few sub-steps for even deeper granularity.
There is a reason the Kill Chain is being used by some of the most successful information security teams around. It is a powerful tool for any security organization that is able to harness its true potential and resolve highly complex attack scenarios. Like any tool, though, it can and should be modified as appropriate to fit an organization's specific needs.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




