Breach disclosures are down, and reported ransomware attacks have also plummeted. Good news -- or a calm before the storm?
August 13, 2020
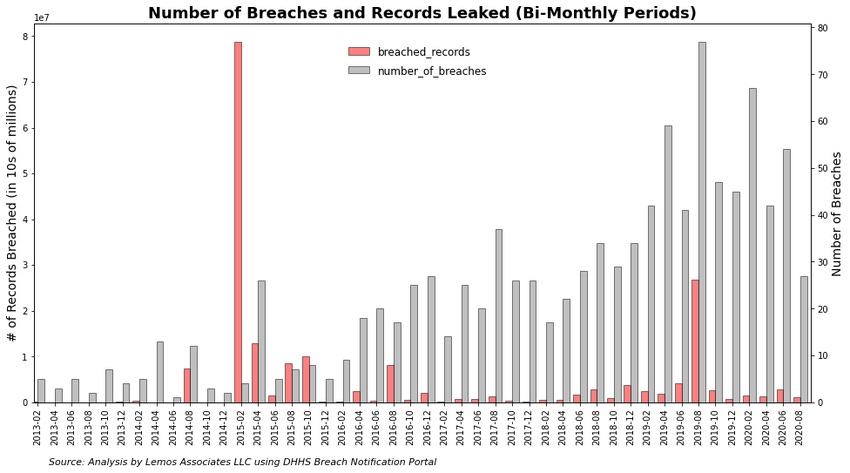
The number of breaches disclosed by healthcare companies to the US government declined slightly in the first half of the year compared with the latter half of 2019, according to a new analysis of the data provided by the US Department of Health and Human Services.
The analysis found the number of breach reports declined 10% in the first half of 2020 compared with the previous six months, and the number of compromised records fell by a stunning 83%. Combined with a previously reported decline in reported ransomware attacks on healthcare organizations, the study suggests healthcare companies are seeing fewer cyberattacks.
The reason for the respite, however, is not clear. The data could suggest that healthcare companies have become more serious about cybersecurity or that cybercriminals have made good on a reported pledge to not interfere with healthcare during the pandemic.
Neither explanation is likely, says Drex DeFord, strategic executive at CI Security, which published the data in a report released today. CIOs have told the company that they are pushing their systems to the limit by having thousands of people work from home, supporting mobile medical staff, and dealing with new suppliers, he says.
"What we are seeing in the breach portal does not feel very consistent with the disruption of sending people home to work, adding a lot of IoT, connecting a lot of new medical devices, and connecting to a lot of new suppliers because you can't get an adequate supply of PPE," DeFord says. "There are a lot of things in there that lead us to believe that there should be more cybercrime and more breaches than are being reported."
Yet breaches are not the only type of attack that declined in the first half. Ransomware targeting healthcare organizations also plummeted, dropping by nearly a factor of 10, from at least 764 incidents in all of 2019 to 41 reported incidents in the first half of 2020.
The surge in 2019 came because cybercriminals found fertile ground for ransomware in the healthcare organizations' vulnerability to phishing attacks and network exploits, and because the organizations could not suffer much downtime to their operations, security software provider Emsisoft said in its 2019 report.
"Ransomware incidents increased sharply in 2019 due to organizations' existing security weaknesses and the development of increasingly sophisticated attack mechanisms specifically designed to exploit those weaknesses—combined, these factors created a near-perfect storm," the company stated.
Emsisoft's latest report on ransomware in the first six months of 2020 does not directly attempt to explain the decline in attacks, except to say: "Between January and April 2020, the number of successful attacks on public sector entities decreased month-over-month as the COVID-19 crisis worsened."
Distributed denial-of-service (DDoS), however, is one type of attack that has apparently increased. Network security firm NetScout has seen a 25% increase in DDoS attacks in the first half of 2020 compared with the same period a year ago, the company said. The increase in use of telemedicine during the pandemic may make doctors' offices and hospitals a larger target, says Hardik Modi, assistant vice president of engineering for Netscout's threat and mitigation products.
"The provisioning and delivery of healthcare has undergone a sea change during the COVID period, with a large growth in the use of telehealth," he says. "The increase in prominence of such services tends to attract the attention of the criminal element on the Internet, whether for ransom/extortion campaigns or sheer nihilism.”
Dark Reading's own analysis of the US Department of Health and Human Services data shows the number of breaches has declined on average by about 3% in the first half of 2020 compared with the previous six months. In addition, outside of a few major breaches — such as the leak of records by the American Medical Collection Agency that its clients, such as Lab Corp. and Optum360, recorded in July 2019 — the overall number of compromised records remained fairly steady.
The decline in breaches noted in the CI Security report could also be because healthcare firms are not reporting ransomware as a breach or because the organizations do not have the visibility to track threats in their newly distributed workforce. The latter issue could mean attackers have infiltrated networks, but they are doing reconnaissance rather than immediately attacking, says CI Security's DeFord.
"We are looking at the second half of 2020 and considering the amount of dwell time we see with cybercriminals in typical corporate networks," he says. "Our feeling is that they are doing a lot of exploration before they decide to set off ransomware, so we think the second half of 2020 is going to be rough."
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




