As sexy as it is, the Cyber Kill Chain model can actually be detrimental to network security because it reinforces old-school, perimeter-centric, malware-prevention thinking.
Created by defense giant Lockheed Martin, the term “Cyber Kill Chain” has been widely used by the security community to describe the different stages of cyber attacks. It’s a compelling model, easy to understand... and, let’s face it, the name sounds really cool.
However, whenever we look under the hood of the Cyber Kill Chain diagram that graces the Lockheed Martin website, we can’t help but try to scroll down farther than the diagram reaches. Because -- in a year that’s seen successful targeted attacks on consumer-facing giants like Target, JPMorgan, and Home Depot -- it has become clear that the actual scope of today’s cyberthreats extends far beyond that of the Cyber Kill Chain.
Beyond intrusion
Lockheed Martin’s model is intrusion-centric, which was the focus of cyber security when it was created, and is indeed still the focus of (too) much cyber security effort today.
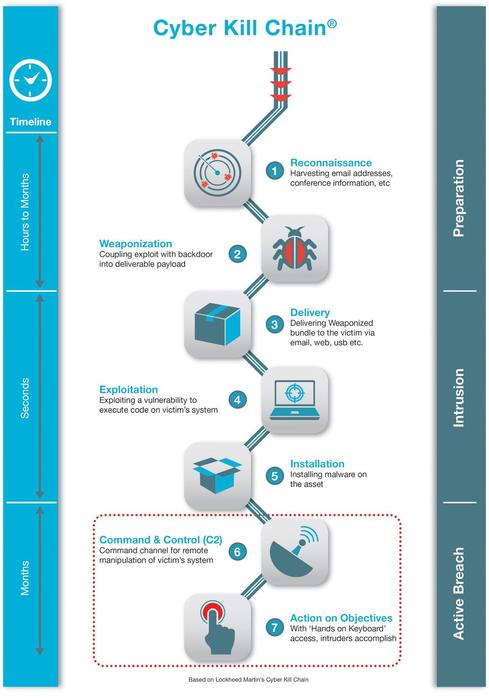
The following is a brief description of its seven steps.
Step 1: Reconnaissance. The attacker gathers information on the target before the actual attack starts. He can do it by looking for publicly available information on the Internet.
Step 2: Weaponization. The attacker uses an exploit and creates a malicious payload to send to the victim. This step happens at the attacker side, without contact with the victim.
Step 3: Delivery. The attacker sends the malicious payload to the victim by email or other means, which represents one of many intrusion methods the attacker can use.
Step 4: Exploitation. The actual execution of the exploit, which is, again, relevant only when the attacker uses an exploit.
Step 5: Installation. Installing malware on the infected computer is relevant only if the attacker used malware as part of the attack, and even when there is malware involved, the installation is a point in time within a much more elaborate attack process that takes months to operate.
Step 6: Command and control. The attacker creates a command and control channel in order to continue to operate his internal assets remotely. This step is relatively generic and relevant throughout the attack, not only when malware is installed.
Step 7: Action on objectives. The attacker performs the steps to achieve his actual goals inside the victim’s network. This is the elaborate active attack process that takes months, and thousands of small steps, in order to achieve.
In fact, steps 1 through 6 of the Chain relate solely to intrusion, which is, as we know from recent attacks, only a very small part of a targeted attack. Along these same lines, the Chain is disproportionate on an attack time scale: Steps 1 through 6 take relatively little time, whereas step 7 can take months.
Further, it’s worth considering that steps 1, 2, and 3 are not relevant from an operational point of view. These are just the documentation of steps an attacker may take behind the scenes, not something that security professionals can directly address or influence.
Then we have the fact that the Chain is completely malware-focused. But malware is only one threat vector facing today’s networks. What about the insider threat? Social engineering? Intrusion based on remote access, in which no malware or payload is involved? The list of threat vectors facing today’s networks is far, far longer than those covered by the Chain.
What we’re left with, after we eliminate non-practicable steps and steps that are too narrow in their focus to maintain broad relevance, is infinite space between steps 6 and 7 (“Command and control” and “Actions on objectives”). And it is in this vast place that today’s targeted attackers are thriving -- many of them invisible to the Cyber Kill Chain paradigm.
The takeaway
We’re not afraid to say it: Over-focus on the Cyber Kill Chain can actually be detrimental to network security.
Why? Because the Cyber Kill Chain model, as sexy as it is, reinforces old-school, perimeter-focused, malware-prevention thinking. And the fact is that intrusion prevention solutions cannot provide 100% protection. A persistent, highly determined, and highly skilled attacker will always find a way in. And once the attacker is past your perimeter, traditional Cyber Kill Chain-style prevention solutions like firewalls, sandboxes, and antivirus can’t help. Once they’ve bypassed these solutions, attackers are free to operate in your network unobstructed.
The answer? If you must use the Chain model, zero in on No. 7. Focus on detecting ongoing attacks -- attackers that have already breached your perimeter -- before the damage is done. Instead of analyzing old malware, deploy a breach detection system that automatically detects and analyzes the changes in user and computer behavior that indicate a breach. These subtle changes are usually low-key and slow, and affect only a small number of computers, but the right analysis and context can flag them as malicious.
Want another point of view on Kill Chain effectiveness? Check out Leveraging The Kill Chain For Awesome.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




