Mandiant calls out People's Liberation Army Unit 61398 as the APT1 group responsible for cyberspying against multiple industries; Dell SecureWorks discovers new victims of APT1/aka the "Comment Crew," "Comment Group"
February 19, 2013

Finally, convincing evidence of a long-suspected Chinese military link to cyberespionage against U.S. firms: A prolific and especially persistent cyberespionage group out of China has been tied to the People's Liberation Army and has been behind attacks on a minimum of hundreds of companies across 20 major industries mainly in natively English-speaking countries.
A comprehensive report published today by Mandiant based on its investigations into around 100 APT-based breaches, including attempts on the security firm itself, exposes characteristics of the so-called APT1 group, which Mandiant believes is part and parcel of China's secretive People's Liberation Army Unit 61398. Unit 61398 is located in Shanghai in the same area where Mandiant has traced APT1's hacking activities, including two of four networks that also serve Unit 61398's location in Pudong New Area in a 12-story building built in 2007.

The building in Shanghai where Unit 61398 is based, according to Mandiant. Source: Mandiant report, Image Copyright 2013 city8.com
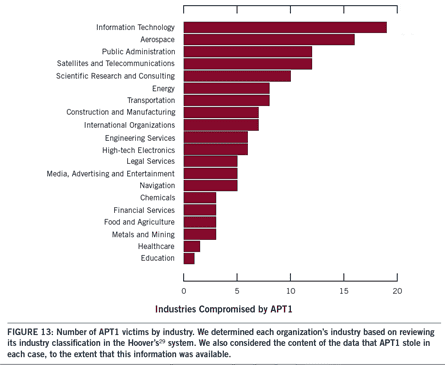
According to Mandiant, the APT1 gang—aka the Comment Crew or Comment Group--is one of the most active and has stolen hundreds of terabytes of data from a minimum of 142 organizations and can simultaneously pilfer data from dozens of victims at the same time, and has waged some of the most widespread cyberspying campaigns when it comes to the variety of industries it has targeted, including information technology, aerospace, and energy. But this is just one of 20 APT groups that Mandiant tracks—there are plenty of others, demonstrating just how pervasive this threat really is today.
"There are a lot more out there. We think there's more about APT1 even than we presented, but APT1 is the most widespread group in terms of the [various] industries" it targets, says Richard Bejtlich, CSO at Mandiant. "And there are definitely other [Chinese APT] military groups.
"This is the shopping group that gets as much as it can from lots of different targets," he says.
Researchers at Dell SecureWorks, meanwhile, also have been tracking the same hacking group for some time now and sinkholing its traffic: They revealed today that they recently discovered that a major U.S. university had been compromised by the APT1/Comment Crew group, as had a U.S. Defense contractor and an energy firm.
The university had been infected for two and a half years, says Silas Cutler, a security researcher with Dell SecureWorks, a long timeframe that's characteristic of this spy group. "We reached out to [the university] and successfully began working with them and identifying malware that was used and traced it to the Comment Crew group. We took that back to the sinkhole and identified a Defense contractor and an energy company" that also had been victimized by the group, he says. Turns out the university had been working on a research project that was related to some obvious interests of the Comment Group, says Silas, who declined to provide more details on the findings at this time.
China long has been considered the biggest culprit of cyberespionage operations against U.S. government and commercial businesses, a worst-kept secret that became very public when Google first 'fessed up to being breached by Chinese hackers back in 2010. Although Mandiant says the Chinese APT group behind the attacks on Google, Adobe, Intel, and other major corporations in Operation Aurora was not the handiwork of APT1, the APT1 group was behind a spear-phishing attack against Digital Bond, and could be behind the Shady RAT attacks.
SecureWorks' Joe Stewart says based on his research and the indicators of compromise released by Mandiant today, he can confirm that this group indeed executed the Shady RAT attacks, and was tied to the RSA breach, as was a second large APT group out of Beijing that at times appears to work with APT1/Comment Crew. "We found connections with them, reuse of malware, infrastructure. We are pretty confident they are all under one umbrella: It almost seems these groups are in competition with each other," Stewart says. But SecureWorks stops short of confirming any Chinese government ties between those two groups, he says, because it can't definitively confirm or prove that connection.
[Researcher uncovers hundreds of different custom malware families used by cyberspies -- and discovers an Asian security company conducting cyberespionage. See Scope Of APTs More Widespread Than Thought.]
Jeffrey Carr, CEO of Taia Global, said in a blog post today that while he agrees that China engages in cyberespionage against the U.S., he isn't convinced that APT1 is part of the Chinese military, either. "Mandiant simply did not succeed in proving that Unit 61398 is their designated APT1 aka Comment Crew," he says.
Most experts concur that China indeed is the biggest offender when it comes to cyberspying. According to one source with insight into these attacks who requested anonymity, China is an obvious adversary in this case because "on a scale, their attacks are just super-simple and so large, they stand out."
According to the new Mandiant report, the APT1 group is known for gaining a foothold into the victim organization's network, and coming and going over months or years in order to grab technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, and emails and contact information from top-level officials at the victim organizations.
In one case, the group was inside a victim's network for four years and 10 months. Its average infiltration time is a full year in most victim sites. In other eye-popping statistics from Mandiant, the company watched APT1 steal 6.5 terabytes of compressed data from one victim organization over a 10-month period, and in January of 2011 alone, the group hit 17 new victim organizations from 10 different industry sectors.
Next Page: China Telecom Provides Special Fiber Optic Network
The group uses a couple of trademark tools of its own for stealing emails, GETMAIL and MAPIGET, and its server infrastructure encompasses more than 1,000 servers. Mandiant estimates that the group could have hundreds or thousands of operatives, and that require support from linguists, open source researchers, malware writers, and experts who ship stolen information to the requestors.
Mandiant found that China Telecom had installed a special fiber optic network for Unit 61398 for national defense purposes, and like most APTs, APT1 starts most of its targeted attacks with a convincing-looking spearphishing email that includes an infected attachment.
The company today released more than 3,000 telltale indicators of APT1 infections—domain names, IP addresses, and MD5 hashes of malware, as well as sample indicators of compromise that include more than 40 malware families, 13 encryption certificates used the group, and a videos showing some real attacks by the group.
Mandiant also revealed details on three members of APT1, including one who writes malware for unit who appears to be a big Harry Potter fan based on his authentication security questions, and another who goes by "Ugly Gorilla" and has a penchant for signing his malware with his trademark hacker handle. Another hacker who goes by "SuperHard” revealed his physical location was the Pudong New Area of Shanghai.
click image for a larger version
Source: Mandiant
Given China's heavy monitoring of Internet use, it's "highly unlikely that the Chinese Government is unaware of an attack group that operates from the Pudong New Area of Shanghai," the Mandiant report says. "Therefore the most probable conclusion is that APT1 is able to wage such a long-running and extensive cyber espionage campaign because it is acting with the full knowledge and cooperation of the government. Given the mission, resourcing, and location of PLA Unit 61398, we conclude that PLA Unit 61398 is APT1."
The "APT1: Exposing One of China's Cyber Espionage Units" report is available Website here for download.
Have a comment on this story? Please click "Add Your Comment" below. If you'd like to contact Dark Reading's editors directly, send us a message.
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


