Customized, targeted ransomware attacks were all the rage.
April 18, 2019
Ransomware attacks may be declining in number but almost every other metric related to the threat is trending upward: higher ransom payments, more downtime loss, and longer recovery time.
Those are some of the findings from a new report from Coveware that studied data from ransomware attacks in the first quarter of 2019. Overall, victims paid more ransom money, experienced greater downtime, and took longer to recover from an attack than ever before.
Much of these trends were driven by an increase in ransomware types such as Ryuk, Bitpayment, and Iencrypted, that were used in customized, targeted attacks on large enterprises, Coveware said.
"Ransomware is no longer a 'one employee clicked an email, and their workstation is encrypted,' type of incident," says Bill Siegel, CEO and co-founder of Coveware.
The majority of ransomware attacks are targeted and require multiple layers of security, access restrictions, and backups to properly defend against. "Also, there is no such thing as being too small to be on the radar for an attack. If you are lax in your security, and don’t continually invest in IT security, it is just a matter of time before you are attacked," he says.
Here are six trends from ransomware attacks so far this year:
1. Ransom demands are getting higher.
The victims of targeted, custom attacks are being asked to pay substantially higher ransoms to get their data back compared to victims of opportunistic attacks. As a result, the average ransom amount paid by victims in cases handled and resolved by Coveware's incident response team jumped 89% from $6,733 in Q4, 2018 to $12,762 in Q1, 2019.
2. Attackers are getting more hands-on.
Instead of automated attacks, threat actors are increasingly staging manual attacks against targeted organizations using compromised credentials, says Oleg Kolesnikov, director of threat research at Securonix. They are specifically targeting high-value systems such as e-mail servers, database servers, document management servers, and public-facing servers.
"In some cases, the ransomware attacks are performed in a semi-automated, operator-assisted fashion, which is not commonly seen with the traditional ransomware attacks," he says. "[This] often makes the attacks much more damaging for businesses."
Researchers believe that the threat actor behind the recent, devastating attack on Norsk Hydro manually copied their LockerGoga ransomware from computer to computer on the aluminum manufacturer's network.
3. Downtime is increasing.
Companies on average spent more time last quarter recovering from an attack than they did in any previous quarter.
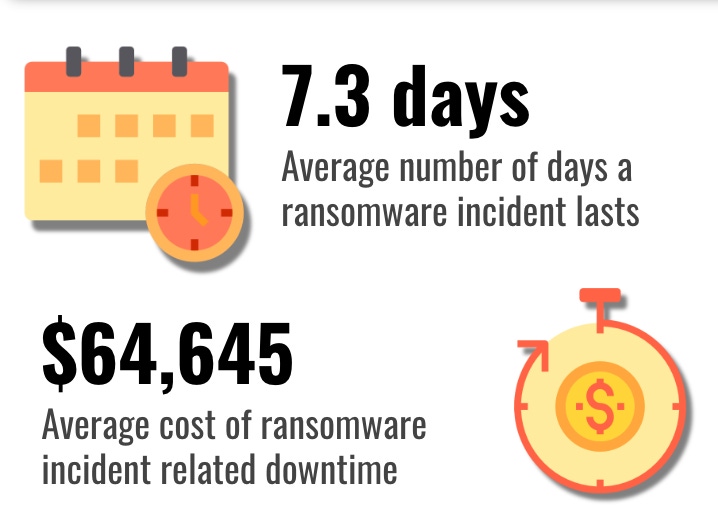
The average downtime following a ransomware attack increased sharply, from 6.2 days in Q4 last year to 7.3 days in Q1 2019. Much of that had to do with increased activity tied to Ryuk, Hermes, and other similarly hard to decrypt malware types, Coveware found. Some ransomware, like Hermes, also caused high-data loss rates compared to other types of ransomware.
Another factor for longer recovery time: an increase in attacks where data backups were wiped or encrypted, according to Coveware.
4. Ransom-related downtime costs are becoming substantial.
A vast majority of ransomware victims fortunately don't end up incurring anywhere near the $40 million in costs that Norwegian aluminum manufacturer Norsk Hyrdo racked up in just the first week following its attack.
But average downtime cost, per attack, per company, was substantial all the same, at $65,645. Costs varied significantly by industry and geography. Companies without cyber- or business-interruption insurance felt the pain the most, Coveware said.
"Downtime is often the most costly aspect of an attack and companies that are part of high velocity supply chains, or that extend high-availability service-level agreements are particularly exposed," Siegel says. Hosting companies are also at risk of their client base walking away if they violate their uptime and availability and guarantees, he notes.
5. Manufacturing companies are now heavily targeted.
No organization is completely safe from ransomware attacks. But entities in the manufacturing sector appear to be getting hit harder than companies in other verticals, says Adam Kujawa, director at Malwarebytes Labs.
"It’s hard to tell if this is intentional or just a result of the kind of security these organizations have," he says. Regardless, for attackers, manufacturing companies present an attractive target, he says. Manufacturers whose operations have been degraded or disrupted by ransomware are more likely to pay a ransom to get things moving again, Kujawa says.
6. Victims that pay up recover their data (mostly).
Security and law enforcement officials strongly recommend that ransomware victims do not pay a ransom to get their data back. Many believe that acceding to a ransom request only encourages more attacks.
Even so, Coveware's data shows that when companies paid up last quarter, they got a key for decrypting their data 96% of the time. That's a 3% increase over the fourth quarter of 2018. On average, victims that paid their attacker were able to recover 93% of their data with the decryption key.
Data recovery rates though tended to vary substantially by ransomware type, however. Victims of Ryuk ransomware, for instance, were generally able to recover only about 80% of their data with the decryption key, while those hit with GandCrab got back almost 100%. The variance had to do with the encryption processes used by different ransomware, faulty decryption tools, and sometimes because of modifications to encrypted files, Coveware said in its report.
Not all who paid received the promised decryption key, either. Some ransomware purveyors, like the group behind the Dharma ransomware family, tended to default often. "Other types of ransomware like Ryuk almost always deliver a decryption tool, but the efficacy of the tool is relatively low," Siegel says.
Related Content:

Join Dark Reading LIVE for two cybersecurity summits at Interop 2019. Learn from the industry's most knowledgeable IT security experts. Check out the Interop agenda here.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




