Verizon's annual data breach report shows most attackers are external, money remains their top motivator, and web applications and unsecured cloud storage are hot targets.
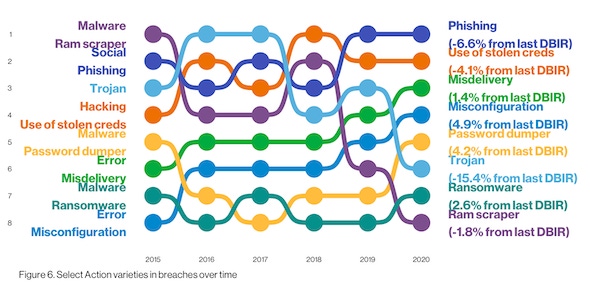
Today's attackers are taking greater advantage of human factors, with more exploitation of errors such as misconfiguration and misdelivery, Verizon's "2020 Data Breach Investigations Report" (DBIR) finds. Errors, along with credential theft and social attacks, made up 67% of breaches.
Researchers analyzed a total of 32,002 security incidents to create this year's DBIR. Of these, 3,950 were confirmed breaches. The majority (72%) affected large enterprise victims; 28% involved small business victims. Seventy percent of breaches came from external attackers; 30% involved internal actors. Organized criminal groups were involved in more than half (55%).
Attackers continue to go where the money is: 86% of breaches were financially motivated, and only 10% were linked to espionage. Advanced threats made up only 4% of breaches overall.
While the "who" and "why" behind most breaches are clear, the "how" presents more variety. Hacking remains a top threat: 45% of breaches leveraged hacking; of these, more than 80% involved brute force or use of lost or stolen credentials. More than 20% involved malware, a category that saw password dumpers as the most common variety, followed by "capture app data" in second and ransomware in third. Most malware is still delivered via email, with some arriving via web services. Office docs and Windows applications remain attackers' malware filetype of choice.
Social attacks were included in 22% of breaches, which Bryan Sartin, Verizon's executive director for global security services, considers a "tectonic change" and reflects attackers' tendency to exploit human mistakes. About a year ago, Verizon experts anticipated a steady three-year increase in human-factor issues like social engineering and credential stuffing. And while malware has declined from 28% usage in last year's DBIR to 17% in this year's, the growth of human-focused attacks is clear and rising, he explains.
"The one thing that really blew up this year is errors, misdelivery, and misconfiguration," Sartin points out in an interview with Dark Reading. "It's a whole other side to the human factor."
Between social engineering and human errors, many of today's problems are people-related. This year's report saw 881 breaches related to internal errors, more than double last year's count of 424. Researchers say this isn't because insiders are making more mistakes; rather, they attribute the increase to improved reporting requirements in new legislation and changes in existing laws.
Errors "win the award for best supporting action this year," Verizon researchers say in the full report. They're now equally as common as social breaches, more common than malware, and are "ubiquitous across all industries." Only hacking remains higher, due to the prevalence of credential theft and abuse, which security experts say should be a top enterprise priority.
"Attackers have amassed a cadre of billions of credentials and that stash seems to get bigger every week," says Bob Rudis, chief data scientist at Rapid7. There is little risk to reusing them, he says, either because businesses fail to notice login attempts or regional authorities "just don't seem to care," and much to gain if a set of credentials works. He anticipates credential theft, which appeared in 37% of breaches Verizon analyzed, will continue to prove popular.
Phishing is the top form of social attack, researchers report. Social scams arrive via email 96% of the time; 3% arrive via website and less than 1% arrive via SMS. The good news is, click rates are lower than previously seen at 3.4%, and reporting rates are slowly rising.
Poking Holes in Cloud, Web Applications
Misconfiguration increased 4.9% from last year's DBIR. Researchers say the increase can be linked to Internet-connected storage found by security researchers and third parties. Indeed, security researchers have become the most common discovery method for error-related breaches: The 2020 DBIR says this is six times more likely than it was in the 2019 report. Cloud misconfiguration was a prevalent issue across industries, according to the DBIR breakdown.
Cloud assets were involved in about 22% of breaches this year. Web applications are a popular vector: 43% of breaches analyzed targeted web apps, more than double the number from last year. The trend is associated with a broader shift of valuable data to the cloud, including email accounts and business-related processes. Researchers say 77% of cloud breaches involved breached credentials, which illustrate the trend of attackers finding a quick route to victims.
"The high percentage in the report concerning web apps as a primary attack vector shows that the average maturity in understanding the importance of DevOps security still has a lot of room for improvement," says Marco Rottigni, chief technical security officer, EMEA, at Qualys. The growing role of security must include a continuous assessment before and after the production stage, he continues, to ensure flaws causing breaches are detected early enough to remediate. Verizon reports SQL injection and PHP injection vulnerabilities are most commonly exploited.
"Manufacturing, healthcare, and financial services were hit very hard by web application attacks this time around," Sartin says. Often the targets are applications built for specific functions. "Custom application often mean unique problems," he explains, noting these are more commonly used in the financial, healthcare, manufacturing, and education verticals.
Related Content:

Learn from industry experts in a setting that is conducive to interaction and conversation about how to prepare for that "really bad day" in cybersecurity. Click for more information and to register.
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




