A new tool from the Global Cyber Alliance shows where companies and organizations are adopting Domain-based Message Authentication, Reporting & Conformance.
November 20, 2018
Email remains a major threat surface for the enterprise, and the Global Cyber Alliance (GCA) has promoted the Domain-based Message Authentication, Reporting & Conformance (DMARC) protocol as a step toward reducing the risk. The GCA now has released an online tool that shows which domains have adopted DMARC as well as the adoption rate in various regions and industries.
"People want to know the rate of adoption, and who had adopted it, so we came up with the leader board," says Shehzad Mirza, director of operations for the GCA. He's quick to explain that the GCA's DMARC Leaderboard is a work in progress, built on the list of domains that GCA is able to get from partner organizations.
"One partner supplied more than half a million domains, another partner is working to deliver 10 million domains in the near future," Mirza says. "Our hope is to have 30 million domains listed by the end of next year."
DMARC is, at its core, a method for testing and proving the authenticity of an email message. Developed as a standard way to combat the rise of spam, DMARC has a graduated sequence of increasingly rigorous steps to prove that a domain is not being used as a spam relay service.
Most major consumer email services, including Microsoft Office 365, Google Gmail, and Yahoo, already employ DMARC. A DHS directive requires all non-military federal agencies to adopt DMARC spurred adoption, with more than 83% of executive branch agencies meeting the requirement before the Oct. 16, 2018 deadline.
But DMARC adoption in industries and local governments is much lower than that of the federal government, as shown in the GCA's DMARC Leaderboard interactive charts. (Information on some regions is still being updated, however).
The maps and tables show rates of adoption in much of North America and Europe, but several parts of the globe remain nearly blank: "As we get more data the map will change; if we had all the billions of domains, the map would certainly look different," Mirza explains.
Source: DCA
The GCA anticipates that the Leaderboard will be a useful tool for CISOs and other executives eager to convince their executive boards to invest in the technology and implementation for DMARC. "This lets CISOs see that their sector adoption is at a point where they can say to their executive staff that they should move forward with adoption," Mirza says.
Interactive maps can be queried on a number of different criteria, but security concerns prevent GCA from allowing someone to see the entire data set. Mirza says that they have limited the result set to 500 domains at a time to prevent screen-scraping the entire database. If an organization has a legitimate need for all the data, he says, they can submit a request and begin the process of being vetted.
The Leaderboard is, at its core, part of a continuing effort to promote DMARC as a viable solution in email security. "We're trying to do something — we published the DMARC ROI paper last month, and now we have the DMARC Leaderboard," Mirza says.
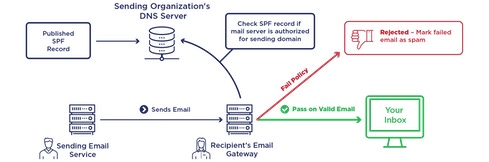
How DMARC Works
DMARC begins with a Sender Policy Framework (SPF) that specifies which servers are authorized to send mail messages from a particular domain. SPF records are stored in an organization's DNS server. When an email message arrives at an organization's email gateway, with instructions to send the message, its originating server is checked against the SPF record. If it's authorized, the message is sent; if not, the message is discarded.
Next on the ladder comes DomainKeys Identified Mail (DKIM), which validates the domain associated with an email message, using a digital signature which, again, is stored in the organization's DNS server. The signature attached to each email message is compared to the stored key; if they don't match (indicating that the message came from an unauthorized server), then the message is not sent.
Both of these steps occur on the sender side of the email transaction. When SPF and DKIM information is shared with receivers - along with information on what the receiver should do if an unauthorized email message arrives - then messages are DMARC-certified.

Source: GCA
Related Content:

Black Hat Europe returns to London Dec 3-6 2018 with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions and service providers in the Business Hall. Click for information on the conference and to register.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


