A major breach can wreak havoc on many aspects of the business. Here are some ways to soften the blow
September 12, 2013


Download the Dark Reading March special issue on Web threats
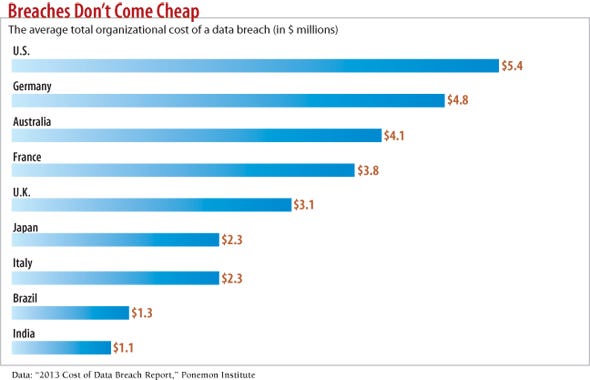
Download Dark Reading's September special issue on the impact of data breachesFor five years now, a Ponemon Institute annual report has tried to put a number on the cost of data breaches. It creates benchmarks for direct costs such as regulatory fines and the cost of notifying customers, alongside estimates of indirect costs such as customer churn and lost business. In 2013, Ponemon pegged the cost of a data breach at $136 per lost record on average across the globe. Ponemon estimated the cost in the U.S. at $188 per record, and $277 per record when the breach came at the hands of malicious and criminal attacks such as outside hacking or insider theft.
Benchmarks have their role, but everyone knows that some types of breaches are far more expensive to companies, such as those that expose intellectual property (IP) such as secret recipes or technological specifications, or that reveal acquisition information prior to a big deal. Manufacturing supply chains could be tampered with in sabotage attempts. Or customer records could be stolen, sometimes from a third-party contractor rather than the organization entrusted with the information.
Factors such as lost IP don't make it into many breach cost estimates because the impact is so hard to measure, and because breaches are often outside regulatory scrutiny and therefore aren't publicly reported. But by understanding hidden or underreported costs, and threats specific to their industries, companies can better plan breach response and recovery, set budgets that fit the risks and reduce the cost of future problems.
The Hidden Impact Of Breaches
IT must contend with its costs of forensics and interruptions that go along with piecing together what was stolen and how. But "hands down, the biggest cost is loss of productivity," says Vinnie Liu, managing partner for security consulting firm Bishop Fox, "not just with the IT team but all the people who are affected by the systems impacted, especially critical systems. It has a domino effect, and it is a huge multiplier effect that happens after a breach."
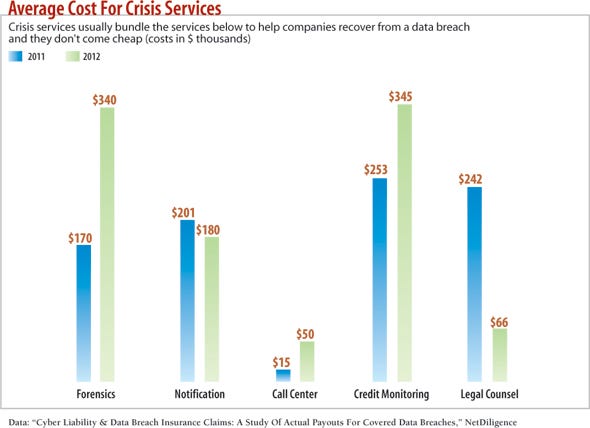
And as Ponemon and others calculate, there are substantial known costs of notifying affected customers and business partners, paying for credit monitoring and identity restoration for victims, and staffing call centers for added customer service calls that all play into the total cost of a breach.
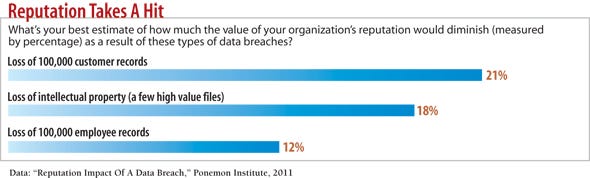
Then there are potential costs for regulatory investigations, litigation, the loss of goodwill and the loss of customers, all of which contribute to the squishy "brand damage" that is impractical to truly measure.
The most commonly neglected cost involves the phenomenon of "organizational thrash," contends Peter Tran, senior director of the Advanced Cyber Defense practice at RSA, the security division of EMC. This is the fatigue factor that hits IT and sometimes other departments after slogging through crisis mode for months after a breach discovery, examining log data, ferreting out the adversary, changing infrastructure, and working with lawyers and communications specialists. Security becomes less effective because IT teams are "burned out, and they're actually less on the ball than before," Tran says.
It's not just the loss of IP such as technical specs that can cost a company dearly. A company is put at a disadvantage if it loses data on how much it is willing to bid on a contract, where it plans to set up new operations or which overseas businesses it plans to negotiate deals with.
Companies also frequently pull back on innovative projects following a breach, particularly in the tech sector, as they try to identify what IP is lost, and how it was taken, before investing more into that work. Putting hard costs on that lost innovation is hard, Tran says, because it's so intertwined with economic and market factors.
Take Early Action
The damage from security breaches tends to increase the longer an attack goes undetected. If the goal is to steal customer data or intellectual property, most breaches start small with a malware foothold on some endpoint, established through a phishing attack or Web-based attack. With a beachhead established, the attacker looks to escalate privileges on the machine, move sideways onto other machines and implant multiple back doors on all the systems the attack touches to maintain persistence. "More importantly, the longer it takes, the more likely an attacker is to find and exfiltrate the organizations 'secret sauce,'" says James Phillippe, leader of threat and vulnerability services for the U.S. at Ernst & Young.
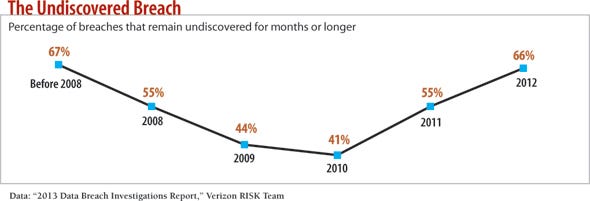
Many compromises today are measured in months, not minutes. The 2013 Verizon RISK Team "Data Breach Investigations Report" found that 66% of breaches in 2012 remained undiscovered for months or more, up from 41% in 2010. And approximately 70% of those breaches were discovered by third parties such as business partners or police, not by the affected organization.
One of the biggest inhibitors to speedy breach detection and response is the lack of visibility and analysis of network traffic, which would allow organizations to connect the dots between seemingly isolated attack symptoms and see them as indicators of a compromised system.
"Many organizations are content to play whack-a-mole when it comes to incident response," Phillippe says. "They clean malware off the host and quickly return it to service. This perceived response only treats the symptom of the issue, the malware."
There are three keys to quickly discovering and responding to breaches, says Phillippe. First, companies need solid asset management to recognize all of the devices on the network and establish baseline behavior, which improves their chances of quickly detecting anomalies.
Second, a well-tuned security, information and event management system is the "heart of a security operations center" and is the engine connecting the dots that show that those anomalies amount to an attack.
Third, threat intelligence services give companies the context to recognize potential attackers. These services offer industry-wide data about attack patterns and trends occurring at other companies so companies can look out for certain indicators of compromise.
Plan For Effective Breach Response
Early detection offers the chance to reduce the cost of a data breach, but companies need a breach incident response plan to take advantage of that knowledge.
"If you have a plan, you'll be ahead of most organizations," says Rick Kam, president and founder of the post-breach response consultancy ID Experts. ID Experts, which has worked with hundreds of IT organizations to help them clean up after breaches, has found that companies that seek its help almost never have an incident response plan. These same IT organizations may have disaster recovery or business continuity plans, but no plan for responding to a big data breach.
According to Ponemon estimates, an incident response plan can help reduce the cost of a breach by as much as $42 per record for breaches involving personally identifiable information. Step one to developing an effective plan is to assess the business impact if a breach were to knock out a critical asset, shut down a key process or expose vital data. "Then determine the actual tactical plans to respond to a number of threats to that element," says Tran.
Similarly, by doing best- and worst-case scenario planning, IT organizations can determine whether response efforts will be centered on gathering forensics to bring an attacker to justice or, more commonly, getting operations back up and running as quickly as possible. "I've seen people go down rabbit holes and waste all sorts of time," Liu warns.
When an incident is discovered, Liu recommends taking a deep breath and reassessing those goals to avoid knee-jerk reactions that can lead to locking all systems down, buying unnecessary software "and just responding too quickly without an endgame."
Some organizations spend too much time trying to attribute the attack to a specific attacker. John Walton, principal security manager at Microsoft, thinks it's worth understanding a company's potential attackers before a breach happens, since that can help prioritize spending and develop defenses. But when a breach incident is in progress, attributing it to a single source shouldn't be a priority.
"Incident response teams can focus too much effort on trying to understand the adversary or trying to ascertain who it is," Walton says. "That can take away a lot of resources and valuable time [from] doing other recovery efforts."
In addition to deep breaths, documentation and testing also are important.
A breach response plan should lay out procedures and processes for containing a breach, putting the forensics plan into action, and communicating your breach plan to partners and customers. It should also identify which experts will be carrying out those processes, says Melissa Ventrone, an attorney who works as an associate in the data privacy and security group at the law firm Wilson Elser. A team of technology, legal, forensics and crisis communication experts should be formed in advance and review and practice the plan. "Policies are only as good as the people who abide by them and follow them and test them and make sure they work," Ventrone says. "The time to learn whether or not your documents are in place, or whether you can follow policies, is not during an emergency."
There's a balancing act here: Organizations should conduct breach management exercises at least once a quarter, says Tran, but he recognizes the risk of overtraining staff and causing fatigue. To avoid "organizational thrash" that may follow an actual incident, Tran recommends cross-training, so that the team can set up a sane work rotation during a crisis.
"A common pitfall in operations is you leave folks in place in their jobs way too long," he says. A forensics expert working 12-hour days examining log data will burn out quickly without some kind of backup staff. "There needs to be enough relief pitchers out there."
The Breach Advantage
While incident response plans are built to help organizations get back to normal quickly after a breach, IT teams should recognize that a major security failure likely will change the company and how it thinks about security. "Your whole outlook changes," says Lucas Zaichkowsky, an enterprise defense architect at security firm AccessData.
These changes can be good or bad. Bad changes such as lost revenue, brand damage, customer churn and competitive damage can be limited through effective planning. Minimizing the damage can also prevent bad change related to a company becoming overly cautious and pulling back on innovation. Good changes, based on lessons learned from the breach, should be maximized to make a meaningful improvement in security operations down the road.
"There are a lot of normal security operations that still get breached," Zaichkowsky says. "As they go through that, they learn a really valuable lesson: that the everyday noise in security they defend against -- the spam and rogue AV pop-ups, the junk -- is extremely different from defending against a real attacker that's going to steal data."
Building up a defensive posture equipped to defend against those kinds of hacker attacks is a good outcome, he says.
One security practitioner at a large financial organization says his company has learned important lessons from the recent sting from a substantial and very public breach. "Sometimes a data breach is exactly what a big organization needs to get its security act together," said the security pro, who asked to remain anonymous.
A massive problem is the only thing powerful enough to instill meaningful IT security changes at a company, the security pro says. For years before the incident, he says he went blue in the face warning about potential threats and asking for additional budget.
Organizations that have been through a breach are generally more willing to spend on the resources needed to respond effectively and reduce the risk and impact of breaches in the future. "Usually, it's a fairly big wake-up call that they've got to change what they do," says Liu.
But turning over a new leaf means integrating effective postmortem analysis into the breach response.
"After the initial incident, take the time to plan out the lessons learned," Liu says. "Not just cleaning up and not just getting secure, but making sure you stay secure." That extra work will add to the post-breach expense, but it's a cost worth bearing.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




