Malvertising accounts for huge amounts of cyberfraud and identity theft. Yet there is still no consensus on who is responsible for addressing these threats.
Malicious advertisements, or “malvertising” for short, present arguably the fastest growing and least understood online threat today. The technique, used to distribute malware on popular websites via online advertising networks, was responsible for an exponential number of attacks in 2014. This past week, The Huffington Post and several major websites presented visitors with advertisements that infected computers with ransomware, locked them down, and demanded money from victims to get back control of their devices.
The danger
Malvertisements can appear on any website at any given time, and there is little that the website owner can do to prevent them. That’s because they are planted on Web pages via third-party ad delivery networks. These networks auction website placements to advertisers using a high bid, free market system. There is currently very little oversight in this industry.
This system was built for efficiency, so the marketplace has very little regulation to force better security practices. To make matters worse, malvertisers use various techniques to disguise the true purpose of their advertisements, often building entire infrastructures designed to redirect users between URLs. Finding offenders that are impersonating brands with fake software updates in this marketplace is extremely difficult.
Digital marketing is big business
According to a report compiled by eMarketer, the worldwide paid media market is estimated at $545 billion, and it will increase by approximately 5% for the foreseeable future. This industry funds the “free” websites we all know and enjoy online, and malvertising is a major threat to their continued success and expansion.
[Find out how Operation DeathClick put a new twist on an old method of infecting users in Sophisticated Malvertising Campaign Targets US Defense Industry.]
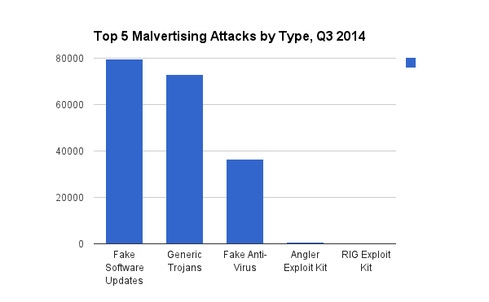
In the third quarter of 2014 alone, almost 200,000 malvertising examples were detected on live websites. The chart below ranks these by type of attack.
What makes malvertising insidious is its ability to hide and deliver malware using an Internet-wide infrastructure that can target specific types of users. Since malicious ads do not persist once a user session is terminated, they’re extremely difficult to detect and track. Worst of all there is still a lot of grey area regarding who exactly should be solving this problem. Meanwhile, consumers and their personal data are being put at risk.
Why should we be concerned?
There are several reasons. First, malvertising accounts for huge sums of financial fraud and is responsible for the theft of personally identifiable data. Meanwhile, most organizations lack the tools to monitor and mitigate this problem. Since there still isn’t any consensus on who is responsible for addressing these threats, no formal processes have been put in place and the problem continues to increase in size and velocity.
The onus is on advertisers and publishers to take the necessary steps to address malvertising and limit the spread of malware on their networks. Until then, it is their customers, the consumers, who remain in the crosshairs.
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




