New research finds more than 80,000 industrial routers exposed on the public Internet.
It was a miniscule change in parameters – just 2mm – but that tiny deviation delivered to a real robot in a recent hacking experiment could result in a massive product recall or even a major defect in an aircraft design in a real manufacturing scenario.
Researchers at Trend Micro and Italy-based Politecnico di Milano today detailed the proof-of-concept attack they conducted on an ABB Robotics IRB140 industrial robot, exploiting a remote code vulnerability they found in the robot's controller software. They fed the robot a phony configuration file that modified its parameters for drawing a straight line. Instead of a perfectly straight line, the robot drew a slightly skewed one, following the 2mm change in instructions.
"The code was working as expected, but with the wrong configuration," says Mark Nunnikhoven, Trend Micro's vice president of cloud research. "We were getting the robot to change what it thought a straight line was.
"Two millimeters doesn't sound significant, but it made a defect in manufacturing. If that was an airplane … it can be a catastrophic event," he says.
The ABB robot hack was part of a larger study published today by Trend Micro on cybersecurity flaws and vulnerabilities in today's industrial robots, "Rogue Robots: Testing the Limits of an Industrial Robot's Security."
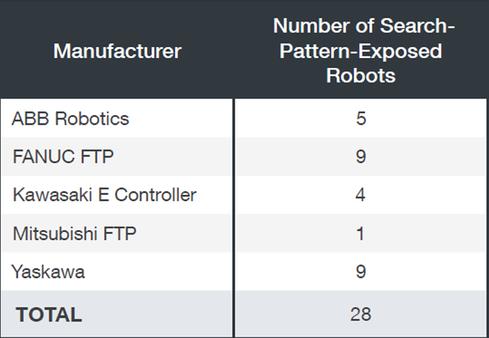
The researchers discovered more than 80,000 industrial routers exposed on the public Internet via their FTP servers and industrial routers in a two-week scan for connected robots from major vendors such as ABB Robotics, FANUC FTP, Kawasaki E Controller, Mitsubishi FTP, and Yaskawa. The scan, using Shodan, ZoomEuye, and Censys search engines, revealed that some of the exposed devices didn't require any authentication to access them.

Exposed industrial routers, according to Censys, ZoomEye, and Shodan search results as of late March 2017 Source: Trend Micro
Industrial robots are commonplace in the manufacturing operations of aerospace, automotive, packaging and logistics, and pharmaceutical companies and increasingly are showing up in office and home environments. IDC estimates that in 2020, worldwide spending on robotics will be at $188 billion. Meantime, robots and their control software are basically as security-challenged as any other Internet of Things devices, containing critical and painfully obvious security flaws that make them relatively easy to manipulate and hack.
Security vulnerabilities in robots can be exploited to take control of a robot's movements and operations for spying, sabotage, or damaging the manufacturing process on the plant floor. They even could be used in such a way that poses a physical danger to humans that work alongside this systems, according to recent research from IOActive that studied popular robots and robot-control software used in businesses, homes, and industrial plants.
IOActive discovered some 50 flaws in that could allow a hacker to remotely manipulate a robot moving about the office, plant floor, or home, to infiltrate other networks there, spy and steal information, and even wreak physical destruction. "Compared with IoT, the cybersecurity threat is a lot bigger with robots. They can move around … and could hurt people or damage property" if hacked, says Cesar Cerrudo, CTO at IOActive.
Even before IOActive and Trend Micro and Politecnico di Milano 's work, the academic community was studying robot hacking: In 2015, researchers at the University of Washington hacked a surgical robot to demonstrate how an attacker could hijack and wrest control of a robot during surgery.
Trend Micro's Nunnikhoven says that like many industrial systems, robots are designed with physical safety in mind, but not cybersecurity. Their controls also are increasingly software-based, and many robots now come embedded with routers for remote-access monitoring and maintenance by the vendor. "Lo and behold we found a ridiculous amount of these [devices] connected to the Internet," some purposely and some unbeknownst to their owners, he says. "They were never designed to be connected to the Internet."
Researchers at Trend Micro and Politecnico di Milano pinpointed five classes of attacks that could be waged against industrial robots by exploiting certain combinations of software vulnerabilities. They reported vulnerabilities they discovered to the respective robot vendors, including ABB, which since has updated its robot with security fixes. Trend Micro reverse-engineered ABB's RobotWare control program as well as the RobotStudio software as part of the PoC hack.
"Testing is a critical process to stay ahead of new cyber security threats. ABB has fixed the concerns in the Trend Micro tests, which helps us provide greater security for equipment in the market. The results also emphasize the importance of using a secure network, since the testing used an unsecured network connection," ABB said in a statement provided to Dark Reading.
Performing a robot hack isn't cheap, however: the researchers say a similar configuration used in their hack could be purchased online for tens of thousands of dollars.
According to Nunnikhoven, the flaws Trend found in various vendors' robots included authentication weaknesses and a lack of end-to-end encryption, as well as other common bugs weaknesses found in IoT and ICS/SCADA systems.
Robot technical information is often available online, firmware images are unprotected, Web interfaces are left exposed, and their software components are rarely patched, according to Trend's findings. The security firm didn't publish specific vulnerabilites in specific products.
They found that an attacker could alter the control system to influence how the robot moves; change the calibration, like in their PoC; manipulate production logic to quietly sabotage the workflow; manipulate the robot's status information so operators don't detect any hacks; and manipulate the robot's status so the attacker gains full control from the legitimate operator.
The manufacturing sector is a juicy target for hackers. According to the new Verizon Data Breach Investigations Report, last year Verizon investigated 115 cyber espionage incidents at manufacturing firms, 108 of which included a data breach. And manufacturing is one of the most frequently hacked industries, according to IBM X-Force Research's 2016 Cyber Security Intelligence Index.
When it comes to robots on the plant floor, the security challenges are similar to that of any other industrial network. The devices are in place for many years and rarely get software updates for design and operational reasons. "These are multi-year investments, similar to SCADA controllers," Nunnikhoven says of industrial robots. He recommends that manufacturing firms conduct network monitoring to watch for nefarious activity, for example. "That way you can see what's going in and out of the robot."
"And [robot] vendors have to do a lot of work to build more secure systems from day one," he says.
Related Content:

About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


