Google's new mobility management framework makes great strides in addressing security and device management concerns while offering diverse deployment options. Here are the pros and cons.
Google's new enterprise mobility management framework Android for Work (AfW) allows employers to effectively manage and mobilize all devices used in the workplace, even when employees use their own devices. Business-owned or single-use devices for specific employees and customers can incorporate IT controls to improve security and end-user functionality.
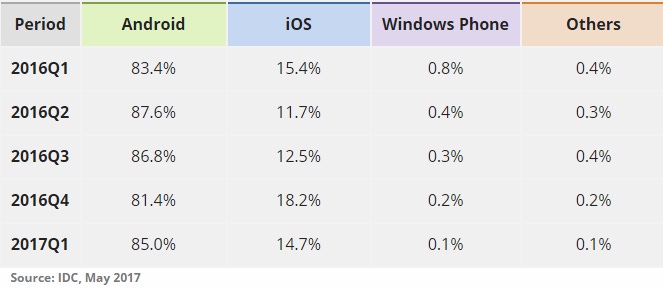
A dedicated Android enterprise mobility management (EMM) solution with an integrated AfW offering is especially critical for the modern enterprise, considering the rising adoption rates of Android devices, as verified by recent IDC research:
While AfW is still evolving into a stable, widely supported ecosystem, it makes great strides in addressing security and device management concerns while offering diverse deployment options and global availability. The program, developed by Google, allows businesses and employees to use Android-based devices for customized work-specific purposes. Through integration with an EMM provider like Codeproof, AirWatch, and others, the Android for Work solution lets IT managers and employees enable tailored capabilities and restrictions in the way the data, apps, and devices can be used for work purposes. AfW features also include a range of privacy and productivity features to the device, which may belong to an employee or provisioned by the employer.
Prior to the AfW service offering, there was no standardized set of mobile device management (MDM) API in the core Android operating system. Several OEMs developed their own set of APIs to enable report management of the device. Popular examples include the Samsung Knox enterprise mobility management APIs on top of the Google Android operating system and the LG Gate, developed as its own set of EMM APIs. As a result, each EMM provider needed to work individually with each OEM and manage the devices through the OEM's EMM stack. For IT and security managers, this meant an ever-increasing number of management portals to handle, at increasing licensing costa and low effectiveness.
Google's Android for Work fills this gap by eliminating the OEM-related API dependency, and offers the same set of APIs in the core operating system. These APIs are available for EMM providers to control and manage Android devices across all the OEMs.
Provisioning Methods
IT managers can use AFW with EMM services to provision and enroll devices for employees in several ways, including:
NFC: Enables quick and easy configurations onto new devices by simply tapping them together.
EMM Tokens: Using codes provided by IT, end users can install specific apps or EMM agents onto their devices from a remote location.
QR codes: Enables devices to scan an image and enroll a device from a setup wizard without any hands-on support from IT for EMM enrollment.
Zero-Touch Enrollment (for corporate-owned devices): Enables simplified, large-scale deployments with support for multiple device manufacturers without any manual setup, allowing end users to use their preconfigured device out-of-the-box. This includes limited support for enforced management apps for certain device and OS versions.
Device Modes and User profiles
Business Only: This device mode is available for corporate devices and offers MDM functionality for individual users, who may be employees, contractors, or other partners. This allows organizations to maintain and configure the same device with unique configurations for every different device owner.
Personally Enabled: This capability is enabled on employee-owned BYOD devices that are connected to the corporate network and enrolled via the EMM. With the Profile Owner mode enabled, the employer or IT manager only gets to access certain work-related data, apps, and features on the employee BYOD device.
Single Use: This mode of operation focuses on the purpose of device functionality as opposed to the end user. As such, IT managers can establish an operating mode with certain features turned on and the rest blocked. These options are useful when the device is used to perform a specific purpose, no matter who gets to use it.
BYOD Challenges & Downside Risks
Striking a happy medium between user satisfaction and enterprise security is key to success in the modern mobility landscape. Single-phone corporate environments benefited from standardized security policies and unified interfaces, but BYOD support increases security risks because it fundamentally changes the nature of the architecture. App- or device-specific vulnerabilities may circumvent an existing security policy, and the more devices (and variety of devices) that are networked together, the greater the risk.
Limiting device interaction reduces risk but hamstrings employees who are accustomed to the flexibility provided by BYOD solutions. This may lead to worsening habits and policies as employees opt to use unsafe workarounds that further expose enterprise networks to malicious or vulnerable apps. All of the above increases the difficulty of managing the mobile environment since your IT department loses a layer of control on user-owned devices. There are also hidden costs to BYOD programs, including spikes in data usage (especially for employees who travel) and increased support costs for a wider variety of devices and apps.
Related Content:

Black Hat Asia returns to Singapore with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier solutions and service providers in the Business Hall. Click for information on the conference and to register.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




