Task Force at George Washington University suggests ways for government to clear up legal quagmires, improve tools, keep us all out of trouble.
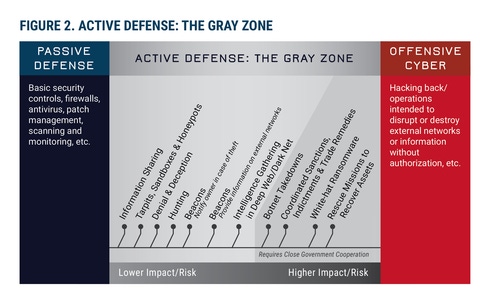
The US government should explicitly prohibit private entities from "hacking back," but empower them to use other methods of so-called active defense against threat actors, according to members of the Active Defense Task Force at the George Washington University's Center for Cyber and Homeland Security (CCHS) in a report today.
The report authors are very clear that active defense is "not synonymous with 'hacking back'" and the two should not be used interchangeably. Active defense, rather, includes technical interactions between defenders and attackers, operations that enable defenders to collect intelligence on threat actors, and policy tools that modify the behaviors of malicious actors -- things like sinkholes, honeypots, beaconing, threat hunting, and gathering intel on the dark Web. It's the "gray zone" between hacking back and doing nothing.
When it comes to active defense, many companies are either "doing nothing or doing them in the dark," says Christian Beckner, deputy director of CCHS.
The trouble is that these activities - even those in the gray zone - may or may not fall afoul of laws like the Computer Fraud and Abuse Act. As the report explains: "Under US law, there is no explicit right to self-defense by private companies against cyber threat actors."
Plus, what really worried the task force, says Beckner, are the companies that think they're doing the right thing and engage in active defense activities that ultimately lead to escalation. They make a bad situation worse - either by causing massive collateral damage or by creating a political conflict between nation-states where there might have been none.
There have been discussions about this before, says Beckner, but the CCHS effort has aimed to delve into more in-depth operational issues, rather than just legal issues. The Task Force includes over 30 individuals from academia, government, and industry, and is co-chaired by former Director of National Intelligence Admiral Dennis C. Blair, currently chairman and CEO of Sasakawa Peace Foundation USA; former Secretary of Homeland Security Michael Chertoff, currently executive of the Chertoff Group; Nuala O'Connor, President and CEO of the Center for Democracy & Technology; and CCHS director Frank J. Cilluffo.
 Black Hat Europe 2016 is coming to London's Business Design Centre November 1 through 4. Click for information on the briefing schedule and to register.
Black Hat Europe 2016 is coming to London's Business Design Centre November 1 through 4. Click for information on the briefing schedule and to register.
The Task Force suggested 15 key short-term actions for the US federal government and the private sector to make, in order to enhance the ability of the private sector to legally and safely use active defense technologies and policies. Some of those recommendations are:
The Department of Justice should issue guidance to the private sector about what they will and will not prosecute -- in both criminal and civil cases -- when it comes to active defense of a company's own security. Although the DOJ just made public some guidance it had issued to cyber crime prosecutors two years ago, this guidance does not specifically cover organization's active defense.
The Department of Homeland of Security should develop operations for public-private coordination on active defense, using existing groups like industry ISACs, ISAOs and NCCIC.
The US State Department should work with foreign partners to develop standards and norms on active defense.
The White House should develop guidance for federal agencies on when and how it is appropriate to provide active defense support to the private sector. Beckner points out that while a large company in the financial industry might be able to carry out their active defense well enough on their own, other organizations may try to stretch beyond their capabilities. Better cooperation between the private and public sector to begin with will help agencies identify when it is appropriate to step in.
NIST should develop guidelines, risk levels, and certifications for carring out various active defense guidelines.
Federal agencies that conduct or fund research and development should invest more in active defense. Beckner said that there is a particular need for "tools that facilitate attribution."
Amend the Computer Fraud and Abuse Act and Cybersecurity Act of 2015 to allow low- and medium-impact active defense measures.
The creation of best practices for coordination between ISPs, hosting providers, and cloud providers on active defense. The task force notes that third-party service providers like these will play a particularly significant role in active defense, particularly since so many companies also use security-as-a-service. They point to Google's aid in Operation Aurora as an example.
Not all members of the Task Force, however, were in full support of its final recommendations. The report includes an appendix written by O’Connor, expressing her measured dissent. O'Connor wrote "the report advocates a more aggressive posture than I believe appropriate, and does not give adequate weight to security and privacy risks of some of the techniques it favors."
She specifically takes issue with the technological tools of "dye packs" and "whitehat ransomware" -- tools that allow for too loose of an interpretation of the CFAA's rulings on unauthorized access to a computing device, even if the computing device in question is that of an attacker.
She further observes, "When it comes to risky defensive conduct that may cross the line and be unlawful, the report makes two observations that give me pause. First, that some cybersecurity firms might be given a license to operate as agents of the federal government and engage in conduct that would be unlawful for other private parties. Second, that the Department of Justice forbear prosecution of companies that engage in unlawful active defense measures." She points to the collateral damage caused by Microsoft when it brought down millions of innocent websites during a 2014 botnet takedown operation.
Beckner says, however, that organizations need more security tools available to them. "What we're trying to articulate," he says, "is what rules should be in the toolkit going forward?"
Related Content:
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




